From Complexity to Control: How Appalachian State Modernized IAM
See how App State simplified identity management across Banner, Google, DUO, and LDAP and what’s next in their IAM journey.
Appalachian State University's Journey to a Modernized IAM
Phase 1
→ Webinar On-Demand: How Appalachian State University Modernized IAM
→ Lessons Learned: 10 Practical Recommendations for Higher Ed IAM Leaders
→ The State of IAM in Higher Education
Phase 2
→ Webinar On-Demand: From Complexity to Control: Appalachian State’s Real-World IAM Rollout with Moran and Bravura
Lunch & Learn:
→ Book a Complimentary Lunch & Learn by December 15, 2025 and lunch is on us!
Watch On-Demand: How Appalachian State University Modernized IAM
From Brittle Scripts to a Modern Identity Platform that Strengthens Security and Streamlines Campus Access
Appalachian State University’s identity environment had grown increasingly complex — homegrown scripts, manual provisioning, and fragmented tools stretched IT resources and exposed security gaps. Working with Bravura Security and Moran Technology , the university transformed its identity and access management (IAM) program into a modern, sustainable framework that improves security, efficiency, and user experience across campus systems.
Why Identity Management Was Harder Than Ever
With more than 20,000 students and staff, App State’s IAM environment had become a patchwork of disconnected systems: custom Banner tables, manual onboarding workflows, and legacy directories. Each department managed identity differently, making it difficult to maintain compliance and consistency. Technical debt, staffing constraints, and evolving user expectations compounded the challenge.
University leadership recognized that IAM couldn’t remain a back-end function. It needed to become a strategic program — one capable of supporting digital transformation, enabling seamless user experiences, and strengthening security across every system.
A Phased, Collaborative Path to Modernization
To build a stronger foundation, App State partnered with Bravura Security and Moran Technology Consulting to design a phased IAM roadmap aligned with institutional priorities. Together, the teams consolidated tools, established governance structures, and introduced automation to reduce manual effort and human error.
The result: a unified IAM framework that integrates with Banner, Google, DUO, and LDAP — eliminating single points of failure while streamlining provisioning, deprovisioning, and access governance. The university gained a more resilient, scalable IAM foundation that’s ready to support new applications and evolving user needs across campus.
“Identity management isn’t just a technical project — it’s a program that drives institutional change.”
— Scott Weyandt, VP Information Security, Moran Technology
Lessons Learned: 10 Practical Recommendations for Higher Ed IAM Leaders
App State’s experience offers a clear roadmap for other universities tackling identity modernization. Their phased approach, combined with executive sponsorship and cross-department collaboration, set the stage for sustainable success.
Here are 10 key takeaways from the program’s evolution:
-
Align IAM with institutional goals. Treat IAM as an enabler of student experience, security, and compliance — not just an IT project.
-
Build collaboration early. Engage HR, registrar, and departmental leaders to redesign processes together.
-
Address technical debt head-on. Identify legacy systems and replace or retire them before they become blockers.
-
Adopt a phased rollout. Deliver quick wins and adjust as feedback comes in.
-
Invest in governance. Establish clear ownership, policies, and data standards for identity data.
-
Plan for leadership continuity. Ensure the IAM program survives personnel changes and shifting priorities.
-
Evangelize the value of IAM. Communicate how it supports security, compliance, and user satisfaction.
-
Prioritize data governance. Involve stakeholders beyond IT to strengthen oversight and accountability.
-
Manage resources strategically. Equip your team with the right skills and capacity for ongoing operations.
-
Focus on high-impact areas first. Start with mission-critical workflows like access requests, approvals, and certifications.
“We used this moment of temporary chaos to not just fix IAM — but to make the university work better together.”
— Matt McNaney, IT Manager, IAM, Appalachian State University
Program Impact at a Glance
- Unified IAM across Banner, Google, DUO, and LDAP.
- Reduced help desk tickets and manual workflows.
- Improved audit readiness and compliance.
- Built the foundation for automation and continuous improvement.
Download the Full Slide Deck →
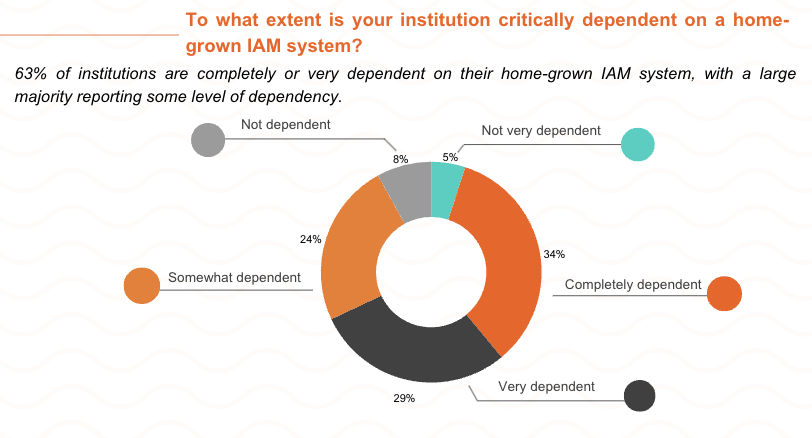
The State of IAM in Higher Education
App State’s story mirrors what many universities face. During the original webinar, more than 100 higher ed professionals shared their experiences managing homegrown IAM systems. The results revealed a sector-wide challenge — and an opportunity for collaboration and modernization.
Key Insights:
-
63% of institutions still rely heavily on custom IAM tools
-
86% cite technical debt as their top barrier to maturity
-
61% face staffing shortages, and 53% struggle with budget constraints
-
Only 14% report limited executive sponsorship
These findings underscore a growing consensus: modern IAM programs must balance security, automation, and stakeholder collaboration to stay sustainable.
"The combination of either changing requirements we're maintaining that or staff shortages or loss of institutional knowledge can change that...that dependency on ERP is not just a source of authoritative information for identity, but actually playing a functional role in identity and access management can be a significant issue."
-Scott Weyant, VP Information Security, Moran Technology
Watch On-Demand: Appalachian State’s Real-World IAM Rollout with Moran and Bravura
Phase Two of IAM Modernization from Stronger Passwords to Stronger Governance
App State’s modernization journey continues. In this phase two session, university leaders join Bravura Security and Moran Technology to share what’s next from password management and access governance to sustaining IAM success across a complex campus environment.
You’ll learn:
-
How to phase rollout without disrupting users
-
Which integrations moved the needle
-
How self-service improved UX and security
-
Where other institutions can start or restart
.png?width=300&height=300&name=Matthew%20Headshot%20(1).png)
Matt McNaney, Appalachian State University, IT Manager, IAM
![]()
.png?width=300&height=300&name=Scott%20Headshots%20(1).png)

Scott Weyandt, Moran Technology, VP, Information Security
John White, Bravura Security, VP, Customer Experience
Partners in Higher Ed IAM Success
Appalachian State’s journey shows what’s possible when strategy meets execution. Moran Technology Consulting provided the governance frameworks and roadmap. Bravura Security delivered the technology foundation — automating identity lifecycle management, enforcing access controls, and integrating across Banner, Google, DUO, and LDAP.
Now, we’re inviting higher education institutions to learn how.
Book a Complimentary Lunch & Learn by December 15, 2025
Join Bravura Security and Moran Technology Consulting for an exclusive session designed for universities, colleges, and community colleges. Over lunch (on us), you’ll explore how leading institutions assess their current identity infrastructure, identify risk areas, and prioritize next steps for stronger, more efficient IAM. No sales pitch, just insights.

Assess Your IAM Maturity
Dive into our Infographic for a Quick IAM Reliance and Security Challenge Overview
Discover where your institution stands on the IAM Dependence Spectrum with our informative infographic. Understand the challenges in achieving a mature IAM program and the significance of stakeholder collaboration for a secure academic environment. Insights are based on responses from the EDUCAUSE Industry Insights webinar attendees. Don't miss out on strategies to improve your IAM practices.Click here to read the infographic and strengthen your university's security strategy.
Download Now.png)
Review the Full Session Transcript
No time to watch the session? No problem. Take a read through the session transcript.
0:03
Welcome to today's Industry Insights webinar, Appalachian States IGA and AM Straight Talk Success. I'm Jason Martin. I'm an online event Production manager at EDUCAUSE, and I'll be your host for today's webinar. Our panelists are going to be introduced in just a moment, but I want to give you a brief orientation to our sessions learning environment.
We hope you'll join us in making our session interactive, and to do so, please open that chat icon and click and make sure that you can use that as a way to share resources, to post questions or to make comments for our presenters.
When you do so, please select everyone from the chat drop down so that we can all see your comments. We encourage you to type your questions throughout the chat, into the chat throughout the webinar and we'll get to them in our formal Q&A at the end or throughout if we can. If you have any technical issues, please send a private message by selecting hosts and panelists in the chat drop down. EDUCAUSE is pleased to welcome today's panelists.
0:58
Bryan Christ is a Senior Identity Solution Engineer from Bravura Security and has more has focused on open source and software development opportunities for more than 20 years, with an emphasis on project management, team leadership and executive oversight, including experiences of VCIO in the greater Houston area.
1:18
He was recently published in Cybersecurity, A peer reviewed journal.
1:23
Matthew McNaney from Appalachian State University has been an apps app state for 24 years and recently started as the IAM Manager one year ago this month.
1:34
Congratulations, Scott Weyandt, Vice President of Digital Identity and Security at Moran Technology Consulting.
1:41
He has been assisting higher education clients with I am assessments, strategic planning, platform selection and implementations for 20 years.
1:49
With that, thank you all for joining us and I'll hand things over to Bryan.
1:53
Bryan, over to you.
1:56
Hey Jason, thank you so much for the introduction.
1:59
Glad to be here today and I am serving folks as Co host and Pacekeeper for today as long as as also chiming in on some of the various discussions.
2:11
Before we get this get started, we do want to allow some time for various organizations participating in today's conference to share more about themselves about their organization.
2:23
And with that, I will turn it over to Scott to introduce more and technologies.
2:30
Thank you, Bryan.
2:31
Hello everyone.
2:32
Thanks for participating.
2:34
I am Scott Wyatt, VP of Digital Identity and Security at Moran Technology Consulting.
2:41
For those of you who know Moran, we work are focused almost exclusively in higher education.
2:47
We work with about 350 different colleges and universities in the last 20 years.
2:53
We've used that experience to develop an I am assessment framework that really focuses on maturing an IAM program.
3:04
And I think we're going to touch a little bit about the IAM program perspective and today's discussion.
3:10
We had the honor of working with Appalachian State a number of years ago on a strategic plan and road map and platform selection project.
3:19
And so thrilled to be here to partner with them again today.
3:25
Thanks, Bryan.
3:26
All right, thank you, Scott.
3:27
Carolyn, if you want to move on to the next slide please.
3:30
So as introduced earlier, my name is Bryan Christ, I am a sales engineer with Bravura Security just briefly mentioned that we have been and the identity and access management space for nearly three decades.
3:43
You can see some of the organizations that if we've worked with, I think you will find them familiar.
3:49
One of the things that's been nice about it is it has given us sort of a front row seat to the challenges that higher education and other institutions of learning have have faced and we've taken those into account as we've built out our solution.
4:05
So next you would think that we're going to introduce Matthew and we'll just have to hold off there for just a second.
4:11
What we want to do and Carolyn, if you'll move to the next slide is we got to conduct this in, in a couple of occasions in a room full of folks and alive environment.
4:23
And so some of these questions we're going to launch a poll here in a second, but we'd like to get your feedback.
4:28
We would like to to hear from you on some of these questions.
4:32
Again, these are questions that we have asked of live audiences before.
4:36
And so the first one here being to the extent that your institution depends on home grown solutions.
4:42
And so just a little bit of color here that could be applications that you built in house or it could be integrations that you performed yourself to glue things together or both.
4:54
So if you'll consider that and then Carolyn, if you'll move on, we'll we'll talk to the next one and give some folks some color on that as well.
5:04
Yeah, so the some of the challenges we've we've heard a lot of them.
5:08
We think that these are probably some of the more popular ones that we're showing here.
5:12
But if you'll weigh in on that and just tell us what you think are the struggles that are are holding you back from achieving a mature identity and access management program and then Carolyn has just introduced the third one.
5:25
Hopefully folks are getting a chance to fill out this poll as we proceed.
5:31
So this one is somewhat similar in the fact that you know, we kind of want to know you know how much collaboration is is going on across the various stakeholders departments.
5:49
So when you know what the challenges are, you need to obviously bring in folks and and we want to know how broad that is happening in your organization.
6:02
So we'll give you just a few more seconds, fill out that poll and then Jason will pop the results on and we'll all get to see what each each other, each other thinks.
6:13
Maybe let's give him 10 more seconds, Jason, and then we'll follow the wrap.
6:18
That sounds great.
6:18
And I see most of us are there.
6:20
We're almost 2/3 of the way there.
6:22
So that's pretty great.
6:23
But yeah, give me, folks, just a couple more seconds and and we'll, we'll call it a quit on that one.
6:34
All righty.
6:35
Looks like we are slowing down.
6:36
So I'm going to go ahead and end the pull.
6:38
And here are the results.
6:42
There you are, Bryan.
6:45
All right.
6:45
OK.
6:46
So first question, not a shocker.
6:49
So again, when we do these in a in a room full of folks in a live environment, that is very much congruent with the number of hands that get raised.
6:59
And when we ask this question, if you will Scroll down to the second question or I guess I can do that here on my end.
7:07
Let's see what are the biggest challenges your institution faces it this one's interesting.
7:14
We've we've seen some of these that mix is pretty good.
7:19
And then lastly that's that's encouraging to see.
7:25
I mean the right answer I think is, is to bring in as many of your stakeholders as possible and I'm sure we'll get into some of that here in just a bit as we're going through the content.
7:33
So folks, thank you so much for participating in this poll.
7:37
Found it very insightful also very confirming to some of the things that we've we've already known.
7:43
And with that what I'm going to do is I'm going to turn it over to Matthew at this point and he's going to introduce the problem statement from Appalachian in terms of their identity and access management program.
7:55
So Matthew, over to you.
7:57
Thank you, Bryan.
7:58
So as you can read on this slide, we had some technical debt and changing of our requirements.
8:06
So Appalachian State is a maybe not large compared to to everyone that's here, but we have, we've recently surpassed 20,000 students and the geography of where we are frequently the advertisement for Appalachian is nestled within the mountains.
8:25
So I would say more like enclosed by the mountains.
8:29
So expansion can be difficult that Appalachian State and we certainly experience that in our technology as a lot of people are probably experience you do the best you can with what you have.
8:42
And we have many very capable and talented people working in Appalachian State who have built the IAM process as best they can within the University.
8:54
But as time and technology have increased and gotten better and there's more reliance on outside web programs and such SaaS systems, we found ourselves kind of at a deficit.
9:09
And so we've reached out.
9:10
And so prior to working with Brevira, we, we decided we had outgrown these systems both just technology wise and also how we handled our data and our data governance.
9:25
And so we have reached out to try to better organize our homegrown systems, work within Brevira and also have better governance over our data.
9:39
All right, Thank you, Matthew.
9:41
Scott, was there anything you want to add?
9:42
Or I know the next slide is definitely going to be something that you're going to have some thoughts on.
9:47
So Scott, why don't maybe you start off here and and just kind of give us an overview of where Appalachian State was before all of this and then I'm sure Matthew will have some thoughts as well.
10:02
So, Scott, why don't you share with us what you got?
10:06
Yeah, sure, Bryan, thanks.
10:07
Yeah, I mean, absolutely.
10:09
One of the critical points for Appalachian State was as as Matt mentioned, there's rapid enrollment, right.
10:20
So changing requirements needs for greater flexibility, but at the same time most of the core identity and access management functionality and even the logic resided within banner tables and the custom application of certain banner tables for identity and access management functions that that situation isn't that uncommon for banner schools that we work with.
10:54
But the combination of either changing requirements we're maintaining that or staff shortages or loss of institutional knowledge can change that.
11:06
But also we're seeing there's so much ERP migration and change happening that all of these things that that dependency on ERP is not just a source of authoritative information for identity, but actually playing a functional role in identity and access management can be a significant issue.
11:30
And that that was really the the, the key driver in Appalachian State.
11:35
But as we got in there and we looked and performed our assessment again not just on the technology but talking about people processes, we really identified that there was business processes that needed to be addressed, still need to be addressed in some cases.
11:53
And to do that, that meant shifting away from thinking of identity as a technical problem.
12:01
How do we solve this technical issue, what we used banner to thinking about it on a programmatic level and saying well, how do we establish broader awareness of the needs and changes, how do we create enough collaboration to address things like business processes.
12:18
So that's really kind of where things were when we when we first entered there a few years back.
12:26
Matthew, is there anything you would like to add that that would be helpful to folks on in the audience to kind of understand where you were before all of this?
12:35
Yeah.
12:36
And he's exactly right.
12:37
And that we, we really had to step back and with their help kind of look at like how we were organized and how we were working through these processes.
12:46
For example, we have two onboarding areas.
12:49
We have Academic Affairs and human Resources, two different departments bringing on staff and faculty and different methods different ways.
13:01
So we really had to look at not just how is this program going to work for us and help us, but also how can we use this point of temporary chaos to also look at our business processes and try to make it not just fit the program, but just bring together the university in this, in this process and try to make everything better.
13:25
Because we have been using the same processes for a long time, different the same programs for a long time.
13:31
And as Scott mentioned, you know, you lose the people who originally created those and things get long in the tooth.
13:37
It's those programs can kind of be like a Jenga, Tire, Jenga game where you like to try to add more features onto something to make it work.
13:47
You're actually pulling out from the foundation of it and it makes it more likely to to fail.
13:55
And so, yeah, we, we had a lot of issues to meet.
14:00
Yeah, great.
14:01
Thanks for sharing.
14:01
In fact, it kind of dovetails pretty nicely into this next slide.
14:06
So there's probably no shocker here that the polling questions were somewhat tied to the content here, but I think you're going to see pieces of that here in the slide.
14:16
And since Matthew, you were just talking about things like, you know, the foundation and what was kind of glued together, maybe you can talk to, you know, some of these items that were the were sort of the challenges that that you perceived.
14:36
Sure.
14:38
Yeah.
14:38
So I am as truce have been invisible.
14:40
That's true.
14:41
And I'm I'm sure a lot of you have experienced this is when things are working you don't hear a lot about it right.
14:48
It's just things as long as things are functioning it's it's when things when problems arise that that you're looked at critically and I I am was working.
15:00
I I mean I am works kind of OK as it is but it's just that the more complex the more things that we have to get involved and then it's it's just it it adds on time to the people who have to work on those processes.
15:13
It adds on the manual processes to fit those products or solutions where you have to instruct people of how to OK, well we know you've been doing it this way but now you need to start working it this way and that in itself as time progresses that becomes antiquated and deprecated and and then you get the the problem of well, this is how we've always done it and it's like well that doesn't fit the newer technology.
15:41
So, yeah, as that kind of combination of problems, yeah, our strategic goals are really one of the big things is who has access to the data and who should, who should see that data.
15:54
And part of our IAM process has been the governance of IT deciding having stewards for each area of data so that when data is requested, you know who to ask.
16:08
And they have oversight on that instead of people just going, well, I need access to this.
16:13
Who do I speak to and we go, I don't know someone Bill works with databases, go ask them.
16:19
We need to have people who were just not in tech but are outside that work with the data, the registrar's office and admissions and health services and people like that and have buy in and work with them on determining who has that kind of access.
16:35
And I wasn't here for this.
16:36
This the project the I am project actually began prior to my employment but so I can't speak to this the presentation to the chancellor's cabinet but it certainly was the genesis of of everything that we've had within the last two years and it was convincing of we need to look at this.
16:56
We need to get everything in order and we need probably need we need some help on this And so that's why it was funded.
17:02
That's why the department that I'm I'm the manager from was created.
17:07
That's why the IGA committee that I'm on works with that that's why data governments has been formed.
17:14
So there were a lot of things that came together from just what was just a presentation to the chancellor and discussion with different members of within and outside of central IT OK yeah.
17:27
So I'm what I'm going to do is I'm going to ask you a kind of a a tie in question here which is you saw the results of the polling and do you think that you know in terms of getting that broad department engagement, how do you think Y'all fared did?
17:42
Did were you happy with with the amount of collaboration you got or do you think that it could have been more or it was just right or what did you I am But you when you're pursuing this process and you're working through it, you really hate to use this over word use.
18:00
But you have to be proactive.
18:02
You have to reach out to everyone that is involved.
18:06
You need to look outside of IT.
18:07
You need to work with people who work with the paper and pencil and spreadsheets and try to approach them with how do you do this?
18:18
What are the problems that you have when you do this?
18:20
How could that process be made better and how can we work with you on this?
18:26
Many times I come from like Bryan, I come from kind of an open source background in which we would design or I would design software for people and it wasn't done in a vacuum.
18:38
I didn't see what the problem was and then just develop it.
18:41
I would go talk to those people and try to find out exactly what they wanted in the software and then form the software around their needs.
18:50
And that's kind of the beauty of open source and we kind of did that I think the same the same way and and with the Identity Access management is we went to those different departments and said, you know our goal is to try to make everything better.
19:04
We're not trying to push because anytime you bring forth new technology, people are going to get nervous.
19:09
So I have to relearn this stuff all over again.
19:12
So we would try to approach them as like we are open to suggestion and we are not trying to force something upon you.
19:18
We are trying to make everything that you're doing better and make it so you know where to go when you need information or you know how to onboard people and try to make all these processes easier.
19:29
And I think when you're open like that and you are interested in buy in and you approach these people and are thankful for the information they have.
19:38
I I I think it it can be easy and I'm I'm very satisfied with my team and and how well they've done in reaching out to people across campus.
19:48
Very good.
19:49
Scott I'm going to ask you a similar question here so you're you know kind of a third party that came to work with Appalachian State on all of this.
20:00
Would your what would your observations on the same, you know thought here would would you agree with Matthew or do you think that there we kind of were places that maybe still needed to be be looked at in terms of collaboration or?
20:17
You've seen, you've seen a lot.
20:18
So I'm I think the audience would be interested in your perspective on that.
20:22
I I think I mean Matthew's correct, especially for where they are today.
20:29
The the I Am team or the project team we we work with in IT was extremely open to listening, collaboration, serving the campus so that that they had the right attitude, they didn't necessarily have the right channels or level of awareness and that there was really two things that happened.
20:53
The strategic alignment was really important for making the business case to the chancellor.
21:00
So as part of the assessment, you know we do an assessment, we come up with a plan, we work with IT, we all think it's great, but then it's like all right, that's the easy part, right surprise, we agree.
21:11
Now we have to bring in front of the board, right, the cabinet, and say we need money for a solution, we need money for implementation.
21:19
We want to change the way IT is organized.
21:22
We want to hire people, right?
21:25
The real that's really where the rubber meets the road and approve this.
21:29
And so we work together to craft the business case, the executive message.
21:34
And that's all premised on convincing campus executives that IAM is not just middleware, right?
21:42
You don't want it to be where projects go to die, as people have referenced it in many places as an inhibitor to DEI initiatives, zero trust, work day readiness, digital experience and so forth, right?
22:00
So how do you bring the message to executives and maintain that level of awareness for continued support and funding that's necessary not only for the initial investments, but to Matt's point, right, but to establishing constructive relationships across campus, cause part of it is very much listening.
22:22
That's absolutely where you start.
22:24
But you're also have to get to collaboration.
22:27
I I mean if HR is going to have to change some processes, you know, maybe it's the academic side, maybe it's staff side, maybe it's healthcare, if you're going to be able to effectively deliver day one readiness for all of these employees potentially.
22:44
But the same thing on improving student experience and onboarding, you have to work with recruitment and admissions and registrar etcetera.
22:50
And so raising awareness is very much about listening to what their needs are, strategic alignment, but it's also very much about and this is Michael Barker from UNC.
23:04
You know, he says he relies less on the formal governance channels then that he and also, you know, direct reports and his, you know, and even reports below that are really charged with going out and listening, but always making sure you're giving the message as part of the conversation.
23:23
I am as critical to what you want to do, right.
23:26
And so there's also this sort of evangelizing as part of that, so that they don't know what Identity and Access Management is nor, you know, typically should they.
23:35
But there is a sense of raising awareness as you listen that I think is critical to the collaborative environment you want to build.
23:44
God, I am so glad that you said what you just said.
23:49
In fact, Carolyn, if you'll move us on to the next screen.
23:55
So Matthew when he was speaking a minute ago talked about lessons learned and then Scott, you just brought this up, the lack of understanding about identity and access management.
24:08
You know we have our take on it, which is we think the word in and of itself is somewhat opaque.
24:14
It's been diluted by 1 vendor over here says, you know this is identity.
24:20
Another vendor over here says this is identity.
24:22
And of course you know we're, we're we're explaining to folks what we believe identity and access management is.
24:26
And so I think there's this dilution of the term and so there's this kind of it's got its own sort of education curve to it.
24:36
Scott, it sounds, it sounds like you would agree with me on that.
24:41
Any other, any other thoughts on that from the things that you that you've seen you know or or Matthew, you'll both brought this, you kind of brought this up a little bit.
24:50
Yeah, I I mean one of our clients Humber College in Toronto, I've learned so much working with them because they are a large institution.
25:00
I think it's roughly 20,000 sort of traditional on premise on campus students.
25:07
But they've been rapidly expanding in the non degree certification lifetime learner programs thousands of thousands which has really reshaped the way that they approach identity and access management right of how do we provide real time and access progressive profiling so that you're serving the access that people need consent and privacy.
25:33
Really customer I am focused solutions but it is funny.
25:38
So they when we started a project with them they were like OK we read through your proposal take the I am out of everything.
25:47
No one on this campus wants to hear the word I I am again based on previous experiences and we're calling it digital identity.
25:55
And so I was like well I don't like that that's at least a step in the right direction.
25:58
So you know and but in part of it being digital identity is not just not using IAM but it was also tried to move it from sort of data heavy ERP workforce discussions to customer interface and digital experience discussions.
26:16
And so that was just a a big take away that you know from our experience with Humber in terms of so how I am can be sometimes not effective but also the how that can be related in terms of our how we focus on what the problems are and what the solutions might be.
26:36
Thank you, Scott.
26:37
Matthew, I'm going to turn to you.
26:38
This is quite a bit of content on this slide.
26:41
So we could probably spend 15 minutes on each bullet here, but I'm going to ask you to maybe pick two or three of these and just briefly share with the audience some of the challenges and lessons learned thus far.
26:55
Yeah, One of the ones that may just jump out of people is that we lost the IM manager three months into phase one.
27:02
So yeah, so there was a very talented individual who helped them bring up this, this project and work with everyone on that.
27:10
And within I think several months they were every someone else identified that they were talented and decided to hire them away from Appalachian State.
27:21
So I was hired.
27:24
So they they actually the university carried on the IAM process without leadership for a a good deal and I I applaud them at the progress that they made And then I was hired much later and there was and that kind of when I came in that was bullet point number one is I didn't completely understand what I am program really is and what it entails And so there there was a lot of of learning to do that the resourcing on project and operations and the spaghetti when you start diving into.
28:01
I didn't I had access to banner but I didn't have a lot of experience working within banner information.
28:07
So when you get into that code and when you get into how that information is set up it was very eye opening.
28:15
So it was it was a challenge for me to learn banner, learn these external processes and how they relate to getting data in the system and onboarding people, working with people who are kind of overlooked because they were the single source on a particular piece of code or how they did something or a process and working with them to open up that process and get their trust in in working with us and the system.
28:51
So yeah, there's been a lot of a lot of learning and a lot of challenges.
28:57
There was a a can't remember.
29:02
It was oh, I remember it was the first day that I started working.
29:05
My boss told me did you know that 50% of IAM projects fail And I was like, no, I I didn't know that.
29:10
Thank you for welcoming me to this position.
29:13
But I can understand why that failure exists because it is, it's a lot of work, it's a lot of outreach, it's a lot of collaboration and it's a lot of gathering of of data and structure and categorization.
29:28
So yeah, it it is, it is a difficult process but I believe ultimately rewarding.
29:35
Yeah, I think I thank you for sharing that because I, you know I think one of the things that we want to get out of this conversation today is letting these folks that are on the line know that they're not alone in some of the ways that they may feel.
29:46
In fact Carolyn, if you'll move to the next screen, I think you I think you use the the term eye opening.
29:53
I think that's probably on a good day.
29:56
On the on a bad day you might describe describe it a little bit different than and with this was of course this was part of our polling question that we asked earlier about home grown.
30:07
To me, spaghetti, having been in the open source world, has a very specific connotation.
30:12
It's the mess you find when you crack open code.
30:14
Then there's no rhyme or reason or thought to it.
30:16
But it can be certainly as we've described on the previous slide.
30:20
It can.
30:20
It can involve processes.
30:23
It can.
30:24
You can describe integrations as spaghetti.
30:28
So, Matthew, maybe you can carry that thought a little bit further and then we'll have Scott chime in.
30:35
And to kind of just generally describe what he's seen in terms of commonalities out there.
30:40
So Matt, Matthew and kind of maybe unpack a little bit about the spaghetti.
30:44
Yeah, I mean, it's just the fact that you can't with with all different systems doing different things, you can't always.
30:55
I mean, you want it to be like spaghetti that's dry, right?
30:58
All in a row in a box.
31:02
But as you start to boil it, it doesn't really, that's not really what happens, right?
31:06
The more you use it, the more it gets entangled.
31:09
And so we were trying to bring structure to that and Moran actually suggested like the Active Directory.
31:16
We had more of a, we had a deeper tree structure for Active Directory.
31:20
We're simplifying that by categorization of affiliation of users that are at Appalachian State and we believe it's that that will simplify it and make it easier to use.
31:33
We got a paper cut for the printing system and we hope to because that was that was a large issue across campus of of controlling how printing was used, the creation of the IM unit we're there's only three of us.
31:47
We probably expect that to to grow as we get past into the past total production of Provera.
31:54
We're only in phase one now.
31:55
After phase three, we probably expand as we try to reach out to other projects and other systems.
32:04
Consolidating.
32:05
The employee on boarding us spoke about that.
32:07
We got academic affairs and we got human resources and we all met together and just said how do you do it and how do you do it and what are the similarities and how can we make this better for you.
32:19
And so we kind of took bits and pieces of how academic affairs and human resources did their things, got them to meet, come together and we came up with a single solution that we developed on campus so that we could on board and get demographic information about people when they were coming in, greatly simplified, how they were doing that before getting on house in order to be prepared.
32:38
Again that goes back to creating the IM System project, the IGA Group, which is a collection of different people from around campus to talk about the IEM issues tech wise and the data governance committee to talk with the people outside of IT of how they think data should be collected and watched over.
32:59
And then the final thing was we had hundreds of generic accounts looked at that decided to make some new business processes about that.
33:07
There's a new standard that is going to be published in which we we don't use it as readily.
33:13
Pretty much any excuse somebody could come across as a process they needed to work, they would create this generic account or non human account.
33:21
So we are we're going to slim that down.
33:24
We've already had our first purge of inactive accounts.
33:27
We're going to do another purge.
33:29
We're going to restructure that have different standards and it's also a security issue of how we were handling that.
33:36
I think we were a little laissez faire and how we were handling out those accounts.
33:40
We brought in both the CISO office security office and we also brought in university communication for greater oversight of how those accounts are handled.
33:50
So the entire process was a little battery shock of just getting different areas to look at how things are going and reassess.
34:01
And the drive of of implementing the system gave us the excuse or the the ability to reassess, look at different things and different processes and how things were were handled.
34:16
And you can kind of use it as an excuse for asking people let's is there a better way to do this?
34:24
I know you've done this historically, but is there perhaps a better way of doing this?
34:27
This is a good opportunity with things changing around campus and when things changing with how we look at data to maybe make some changes and hopefully make things easier and better for you.
34:39
Yeah, I like the, I like the optimism in that last statement you made.
34:43
In fact, Scott, what I'm going to ask you to do, if you could just take maybe 2 minutes before we move on to the next slide and you, you see a lot of different organizations.
34:55
And you know, can you talk about this problem and reassure the folks online that they're not in isolation when it comes to this and and how you see it then and where you've seen it?
35:10
Yeah, absolutely.
35:11
I mean, first, I have to say that while yeah, as the poll showed, many, many people are leveraging home grown scripts or applications solutions for some part of their identity and access management architecture, some step of the functionality, but the situations that they're in are quite different.
35:35
I mean depending on staffing and resource or gaps, skills or gaps, institutional knowledge or gaps, the approach to replacing, supplementing, componentizing some of the home grown applications more so than if it's just a bunch of you know, loose scripts developed by people over time.
36:01
I mean we see very different approaches to this as resolved the projects that we're working on and you know it's a question of where does the risk lie in terms of operating with either the technical debt or just a home grown solution that is difficult to support.
36:23
Where is the solution inflexible or flexible right in terms of what might be worth the reserve.
36:31
And then then it really requires a sort of charting out the road map to identify well where do we start from a componentized view of the architecture, which solutions match best in that area.
36:45
But then also phased road map that may continue to leverage some pieces of the home grown applications specifically for some time.
36:56
But you have a progressive road map that's moving you to or more modern, easier to deploy and leverage solutions.
37:04
But it doesn't have to be a, we bought the perfect solution and in 18 months we're going to be completely off our legacy technology.
37:16
And it really depends on the institution size, complexity and capabilities.
37:23
Yeah, it's it's, it's great that you ended on that note about where they want to go.
37:29
If Carolyn, you'll move to the the next screen.
37:32
I'm going to ask Scott to to talk about this is you've been working with Appalachian straight in a strategic strategic manner.
37:40
Can you talk about what you know what the long term goals are, where you would like to see them, you know down the road sure.
37:51
And you know I have been away from Appalachian State a little bit over the last year, but you know the goal, I know that they have and they have selected reverse security as a critical piece of of that goal is, is really moving from a state of technical debt that led to inflexibility to a state in which they can make continuous improvement, right.
38:24
And so they aren't looking at identity and access management as a tool and a project.
38:31
So in you know six more months, you know Mac can wipe his hands that we didn't, right.
38:37
It's really about leveraging a solution, building a team and as we said collaborating with the campus and identifying continuous opportunities to leverage those solutions to bring additional value to the campus.
38:55
And so I know from a long term goal perspective, they're very much focused on the relationships they need to build and maintain across campus and the skills and solutions they need on the team to be able to continually add value and and really help to transform the digital experience for Appalachian State.
39:18
But I couldn't put words into the Matt's mouth, right, Matt, isn't that what you want to do?
39:25
Yeah.
39:27
Yeah, you're you're correct.
39:30
Speaking as a manager right now, it's just like I just I I want it to work.
39:33
I mean we're still in phase one.
39:35
We're trying we're making you know we we have phase one we have user acceptance training coming on within the next week and yeah you know it's it's so new and it's it's so all-encompassing that you do have you feel like you do have a lot of eyes on you when you when you are touching all these different systems.
39:58
But also it's it's kind of funny this the popularity of the project.
40:03
Popularity is probably too strong at work, but the.
40:07
The more you talk about it the more you reach out to people is is people like come back to you and like this is all going to be handled and I am right all right Bevor is going to take care of this like I I I'll hire somebody and they'll sit down and they'll have all the permissions like well we're working there we're trying to get to that point we've and as you said there is no like we're done.
40:29
In fact I believe you know once we get in production we're just going to it's it's an ongoing process.
40:34
We're going to have to look at everything, all the systems that we currently connect with and start trying to incorporate those into the process and see if we can get the management of those with identity to to function.
40:48
But then there's always going to be something else that comes up down the road that we that we're going to want to work with.
40:54
Hopefully as this is used more often and more universities and businesses adapt to this, that other or other other systems will see that as like well, we need to have the APIs, we need to have the REST protocol, we need to have the ways that people can manage these permissions because there's going to be an expectation that there's connectivity between the campus and what's what's going on.
41:20
That isn't always the case now but we hope that the popularity of of this movement will make an effect on other projects that that we have to adapt.
41:31
And I'll go, Oh yeah, you can, you can set permission levels based upon these protocols and such like that.
41:38
So Matthew, there's a handful of things appear on this slide.
41:44
And it, you know, you could kind of look at it kind of buffet style, but what you know without, without putting you in a box here, you see anything up here that is just jumping out as you like.
41:55
It's a Phase 2A, phase three kind of thing, things you've already talked about old.
42:01
Phase two, we're working on phase two, we're working on the pass password management.
42:07
And so we hope to have that almost to come around in a congruent state around the time that we get phase one done.
42:13
So hopefully phase one and phase two will kind of land at the same time and we can concentrate on the phase three which is like the request approval process of asking for different permissions and manually set.
42:28
Yeah, the control access to institutional data is is again the governance kind of thing and that will work on that will work with systems that provide that view data that we need to incorporate with with Vera to try to allow that kind of view access dependent upon your position or the department that you work within.
42:49
So yeah, there's there's a lot of work to be done.
42:52
We're kind of we're early looking forward to it until we get out of phase one, but there's a lot of challenges to to come for sure.
43:03
Good segue into the next next slide, Carolyn, if you would talk to us about phase one, you know what were your goals there, what, what, what were the clean indications.
43:17
I think that we saw on the previous slide that Y'all are getting ready to go into user acceptance testing.
43:23
So to talk to about just real briefly about some of those clear cut goals for phase one, we're trying to get what the Birthright entitlements, the major entitlements that are required for sign in and e-mail, LDAP, Active Directory, Duo and Google established so that when people move on board and off board into the system, they have access.
43:47
One of the major processes that we're just about we're trying to wrap up right now and we're going to work with admissions on is the student tier system of what access they have in the different phases as they arrive on campus.
44:02
You are a student enrolls or has to be enrolled.
44:06
They are admissions decides who they're going to invite to campus and they are admitted.
44:11
The student accepts that invitation and then pays their deposit and is in a member of of the university and then the student registers for a class.
44:21
So there's four different stages of how that student is implemented into the system and there's different areas of the like entitlements and permissions that are required for that.
44:32
And so that's something we hope to bring.
44:35
We're we're pretty good on the Birthright entitlements.
44:37
We think we have that nailed down.
44:38
The student thing will be coming.
44:41
We also have a something that is recently, recently in regards to the entire process, the year, the year or two that we've been working on this is multiple positions for a single user.
44:56
I would guess that with a lot of businesses, you know, you were hired for a single purpose.
45:00
That isn't always the case when it comes to we have people who are faculty who teach classes, but they also work as a staff member in an area.
45:10
We have faculty that teach but are also the chair of maybe a research committee or they work with doctorate programs or something like that.
45:21
And they're membership within these positions can change and their entitlements may need to change as well.
45:29
They may have student workers in a certain position and when they leave that position where there's no longer a need for them, they may lose the ability or they may need, we need to make sure that they lose the ability to have access to that payroll.
45:43
And those are the kind of the challenges that we're get to.
45:45
But we think we're very close on that on phase one.
45:48
Phase two, again this is the password thing and we're we're working on that and the phase three will be when we start incorporating more.
45:56
These are the requests from people who go to the help desk that we work closely with and they were fantastic of.
46:03
I need access to this.
46:05
Well, let's have a supervisor.
46:06
We need that is that we've provisioned for allowing this access and let them approve it or deny it.
46:15
We have working with the security office with logging and working with the, I can't remember I want to say splurge or splug or it's something like that about something hitting the floor and making a sound.
46:30
There's a logging program for security that they use that we're also working on at the same time.
46:38
So yeah, there's a lot of there's a lot of things we have a good expectations of of where we're going to be within the next year.
46:45
But there are still a lot of challenges going on.
46:47
We will meet those challenges.
46:48
But yeah, there's a, there's a lot of different things.
46:53
Yeah, that's I'm glad to, I'm glad to hear that it sounds very optimistic.
46:58
I think the word you were looking for there is Splunk, which is a popular logging system.
47:05
Carolyn, if you'll take us to the next slide real quick.
47:09
So one of the things that both Scott, you know and Matthew you mentioned early on I I heard y'all use the word program both and I think it's really important folks on the line if you've been listening especially in just the last couple of minutes as the we were covering some of those slides, hopefully you picked up on this this idea of phases and you know he was a Matthew was able to sort of articulate you know what what kinds of functionality was going to be tackled in each phase.
47:41
And it's really important I, I'm gonna let Scott chime in here in just a minute.
47:46
But one of the things that we absolutely know is the boil of the boil of the ocean approach to identity access management not just in higher education but in other verticals as well is an absolute recipe for disaster.
48:01
And one of the things that I think that people don't realize when they they actually take a multi phased program versus project approach to tackling identity access management is you can I didn't this wasn't planned but the optimism that was shared with us is just on that previous screen once you get something tackled and behind you it's it's refreshing and you feel motivated to move on to to the next phase.
48:29
And of course you know it affords the opportunity for things like course correction and stuff.
48:33
But Scott we'll let you have the last word.
48:35
We've got about 10 minutes left before we have to get into a little bit of wrap up here.
48:39
So I'm going to let you have the last word on this in terms of you know do this, don't do that.
48:46
As it relates to programs and projects, sure.
48:50
And I think we'll moving into Question Time soon.
48:55
But yeah, and I I think these themes have been been called out throughout our discussion today for both Matt and I.
49:04
And I think the this is really where it gets added.
49:09
I'm fine.
49:09
You're correct.
49:10
Obviously it's not a single project and it spans you know quarters, months, years in terms of phasing out the implementation and deployment of IM functionality and improvements.
49:25
But it's also of different scope.
49:27
The program approach recognizes that if your vision is is more than just select a tool and get it in place without causing too much ruckus, you know, if if the goal is larger than that and it's really to bring transformational value to your campus repeatedly over time, then it really needs to be viewed.
49:56
That is, identity and access management needs to be viewed at the program level and that is there needs to be mechanisms to make sure that your investment, your time, resources, dollars and identity are aligned with the strategic goals and most important initiatives in IT and at your institution.
50:17
And there needs to be, as Matt said, it takes effort right, to establish the type of relationships and awareness across campus to get buy in and collaboration.
50:28
So you're out there listening to what they need, but you're also establishing patterns of collaboration that is you know the prerequisite for things like business process redesign, better data entry, but also data governance and data standards and then obviously establishing policies for the camps as well.
50:54
All of these are are are really critical for long term success and all all of them are really based upon raising the awareness of the importance of IAM even if we don't use that word or those that acronym, but also establishing the the relationships that allow for collaboration.
51:31
And I think Bryan just disconnected.
51:33
I I can y'all hear me.
51:36
Oh, there it is.
51:37
Yes.
51:37
OK.
51:38
Yeah, I did.
51:38
I lost connectivity right at the end.
51:41
Carolyn, I'm not seeing your screen but I know what is on that last slide.
51:46
So we're going to, we're we're running low on time, we've run a, we'll wait for Bryan to rejoin us, but yeah, it seems like we are running towards the end of our hour.
52:02
So if you all do have any questions for the panelists, I'm also happy to tee those up for them.
52:07
I'll take this opportunity to also talk about the resources that are on your screen.
52:12
So again you can use this QR code to book a complimentary consultation.
52:18
You can also download the helpful resources by going to the site and the site is also listed there.
52:23
And if we don't have Bryan join us back, which he might be here in just a moment.
52:27
I'm happy to also throw it back to Scott and Matt for any closing comments and thoughts.
52:36
Scott mabier, over to you.
52:41
Sure.
52:43
Oh, there's a good one.
52:45
I think that's for you, Matt.
52:46
About how long do you anticipate the project to take to be complete?
52:50
So I guess when is there a phase one go live?
52:54
Yeah, we anticipate it to be done two months prior to today that didn't happen.
53:02
We we hope to have finished UAT in March.
53:06
We hope to go live with phase one in May maybe phase two may occur around the same time and then three we haven't, I don't I can't remember if we have a timeline on that.
53:21
There's been pushed out from phase one but we experienced a couple of discoveries as we got closer and closer to our initial deadline that had to be addressed.
53:33
So we have to universities will understand this We we're trying to implement this at a time in which not many people are in the system.
53:41
So it's it's got to be around summer or it would have to be around winter break or sometime around that.
53:45
So although we think we're probably be ready prior it, it needs to be may about the time when students are finished with exams and moving out and did you say that you're going to be your hope is that phase one and the password management phase two will be deployed simultaneously then in May was that the that's the dream.
54:07
Yeah, I hope we can achieve it, but we'll, we'll see how it goes.
54:12
It depends on how much, how much is needed when we're through UAT.
54:17
If we decided that there's more that we need from bravura or we need to make changes, as I said, we're doing this.
54:24
We're doing phase two stuff in conjunction.
54:27
So perhaps they will feel like, Oh yeah, I think we can probably ramp this up about the same time.
54:32
So we're just starting phase two and it'll probably be followed quick.
54:39
If I recall you said phase three is gonna be focused on access request and approval certification functionality.
54:45
Is that the goal to identify a pilot group of, you know, business units slash app application in which to the leverage Bravura to provide request approval and certification, correct.
55:02
Yeah, yeah.
55:04
There are a lot of external, lot of external processes and a lot of processes that could probably be reviewed to with an access through brevira instead of a manual request or a an account that is made specifically for, you know, certain access.
55:28
So yeah, we're going to analyze those, those outliers, right.
55:32
And there's probably either options for identifying low hanging fruit in the sense that it impacts a lot of people, It'll it'll make a lot of people's lives easier, but it's not a difficult reach in terms of technology, system integration.
55:49
And on the other side there can be, there's a targeted targeted group that maybe have access to more privileged or secure data and you know also going that way.
56:01
So there's different ways that you can get started, but again, just like we talked about earlier, you know the, the Access governance piece, request certification, approval is a forever project, right.
56:12
It's always about prioritizing and identifying a place to start and then figuring out you know what space you know two dot or 3.2 and then 3.3 and three and really taking a more agile approach to to make those improvements definitely.
56:32
And as you said well we would have to weigh like Oh well this is kind of easy but this is more mission critical.
56:37
You know which do we approach first.
56:40
It looks like we have a great question about identifying any of the major challenges in the phase one implementation.
56:46
You mentioned they had some setbacks or discovery occurred recently.
56:50
What the the way you build your system you have expectations about how things are going to work.
56:59
When you ask somebody else to have the same expectations as you that isn't always going to happen.
57:05
So how we expected the implement the getting to work with Google and Duo and LDAP and how we had Active Directory set up was kind of a challenge and you would, you would run our back and you would see you know problems in there and that's and then you have to go back and communicate with them and and and fix those things.
57:26
And so there was always little challenges if we were just always trying to get everything working properly.
57:31
You know, we take everything apart.
57:33
I mean like I think we got to get in this time, we put it back together, maybe there would be a problem with it.
57:39
Phase one was just there were a lot of things we didn't expect, the academic affairs, the HR separation, how things are defined.
57:48
We have affiliate accounts which are accounts that are non paid accounts but don't necessarily but but have rights within the system.
57:57
And then you go, well, this is vendors over here, they have access, but these are, these are they have like military staff that come and work with people on campus.
58:07
With that we have athletic trainers who come in for a brief amount of time.
58:11
And so you just, you learn a lot about just how people are identified on campus and just what what permissions do they have and what should they not have and how long are they here and how does their contract is, Is it nine months, Is it 12 months when their contract drops off, How is that handled?
58:30
So they're just a lot of challenges and you just have this baked in system of handling these things and people have coped with that for a long time and it's become institutionalized And you're starting to, you know, the more you pick at it, the more things start breaking apart and you, you're just learning a lot and just trying to adapt it to the system.
58:49
No.
58:51
Well, Scott, Matt, thank you so much.
58:52
I don't know if Bryan got back connected with us and brought those back.
58:56
Yes.
58:57
For those of you struggling with your cell phone issues today, I know there's a big problem across the country and and maybe even beyond.
59:02
So we really appreciate you addressing that.
59:04
Bryan.
59:04
Just any quick closing thoughts.
59:06
We got a, yeah, just the next steps here.
59:10
So we appreciate everybody being here.
59:13
If you found any of this insightful, we do have a download that you can see here up on the screen, a complimentary consultation that's that's being offered.
59:23
I believe Scott y'all are offering that.
59:27
And then we would love to showcase some of the solutions that we've discussed, especially our newest introduction which is Bravura Cloud, which is some really incisive analytics as you, you know try to structure your program and your various projects.
59:43
So back to you Jason, Fantastic, really appreciate it.
59:48
And as you all have seen there, please feel free to take the the link there for the survey.
59:53
We really do appreciate your feedback.
59:55
We provide that to the presenters as well as use it for our purposes.
59:58
So it's really useful.
59:59
Also the resources from today's session including the recording will be made available on our site later today and you'll be able to share that with your colleagues and we hope they'll join us for another webinar.
1:00:09
We also have our demo day coming up for cyber security tools on Monday, which Bravura is a part of as well, so.
1:00:16
We hope to see you there and Matt, Scott, Bryan and everyone back behind the scenes.
1:00:20
Carolyn, thank you so much.
1:00:22
Nikki.
1:00:22
Really appreciate it all.
1:00:23
Have a great Thursday and a good weekend.
1:00:26
See you all next time.
1:00:27
Thank you.
1:00:28
Thanks, everybody.
1:00:29
Thanks, everyone.
1:00:29
Appreciate it.
Request a Demo Today
Ready to take your institution's IAM strategy to the next level?
Request a demo today and see how our solutions can tailor to your university's or college's specific needs.