Ending Complexity with the New Bravura Cloud
WEBINAR ON-DEMAND
Content
Read straight through, or jump to the section you want to read:
Ending Security Complexity With the New Bravura Cloud
Bravura Cloud Supported Use Cases
Mastering identity, password governance and privileged access security in digital landscapes now challenged by the profound pace of AI demands more agility, efficiency and simplicity than ever before. This keynote introduces the new Bravura Cloud. Our cloud-native security fabric will allow you to fortify your organization's security posture today and in the future with exceptional usability, scalability and efficiency. Watch our illuminating presentation that delves into unlocking the untapped value in your organization’s security data held within your existing or potential investments in Bravura Pass, Privilege and Identity. Discover how scalability, usability, and efficiency have converged in a modern cloud-native solution to create a comprehensive strategy that addresses the evolving challenges of hybrid IT infrastructure and digital security.
Watch on-demand the keynote session; Ending Complexity with the New Bravura Cloud, from our third annual Power Of One Conference.
Key Highlights
Standards-Driven Security Strategy: Offer a standards-based data repository enabling organizations to bring their own user experience, reporting, and even AI.
Scalability – Cloud-Native Deployment Model: Explore how a cloud-native deployment model can revolutionize the way identity and privileged access security are managed. Learn how to seamlessly scale your security framework across your organization, regardless of its size or complexity.
Usability - Open User Experiences: Building on the importance of user-centric design, delve into the significance of an open and inclusive user experience strategy. Discover how simple it can be to create intuitive web, chat, and AI experiences that truly promote productivity and ease of use.
Efficiency – Adding Value to Existing Investments: This webinar will unravel the power of the new APIs and integration points being introduced in Bravura Cloud. Learn how quickly and easily you can empower other areas of your organization with data you already have. Leveraging your existing investments, you have already made in Bravura Pass, Privilege, Safe, and Identity.
Use Cases and Best Practices: Through practical examples, gain insights into how organizations can successfully implement scalable, usable, and efficient identity and privileged access security strategies. Discover actionable takeaways to apply to your own security initiatives.
Presenters
.png?width=300&height=300&name=Colin%20No%20Background%20(3).png)
Nicholas Brown
Bravura Security
CEO
Nick is passionate about providing organizations with the depth and breadth of cybersecurity solutions they need to empower their organizations. Nick comes to Bravura Security with over 25 years of experience in enterprise software with innovative startups and large companies like SAP and Oracle.
.png?width=300&height=300&name=Colin%20No%20Background%20(2).png)
Ian Reay
Bravura Security
CTO
Ian specializes in providing identity and privileged access management solutions to Fortune 500 enterprises, financial, government, and higher education institutions. With decades of experience, Ian is keenly focused on software development and customer relationship management to meet the challenges organizations face today and in the changing future of cybersecurity.
Ending Security Complexity With the New Bravura Cloud
It's been quite the year for our company. We were acquired by Volaris Group. We are also excited to introduce our new product, Bravura Cloud.
Built on our decades of experience in the industry, Bravura Cloud simplifies the modern security ecosystem so you can manage everything in real time without ever leaving the Bravura Security Fabric.
Key Principles of Our Product Offerings
Cybersecurity incidents are happening more frequently to organizations of all sizes, across all industries, all over the globe. And while companies continue to invest in complex digital security tools, the speed at which threats are evolving makes it hard to surface risks quickly and efficiently.
That's why we are building our future product and service offerings around the following principles:
- Immediate value: Our products unlock the existing value within your system by surfacing valuable data and insights that would have otherwise remained hidden.
- User experience: We aim to create a streamlined, secure user experience across all our products so you can delight your end-users.
- Standards-driven: Our offerings are built around key cybersecurity and data management standards, ensuring you can integrate data and capabilities wherever you need them.
- Unification: The Kubernetes platform enables you to manage containerized workloads and services across your cloud environment, creating a uniform experience no matter where someone may be logging in from.
Your organization can keep up with the rapidly changing threat landscape by using the Bravura Security fabric and its expanding set of capabilities. You can simplify your cybersecurity strategy and reduce your overall risk.
And now, with Bravura Cloud, you can bring that robust functionality to all levels of your organization. The Bravura Security Fabric can bring rich and detailed operational insights to help guide your decision-making. Surface hidden risks. Prove you're in control.
Introducing Bravura Cloud
When you need a comprehensive data management and security platform, Bravura Cloud will be an effective solution for your organization.
Bravura Cloud focuses on surfacing the value in the data held within Bravura Pass, Privilege, Identity, Safe and OneAuth.
We are creating a security data engine that allows us to power our future by unlocking the value held within our existing products.
Then, over the next two years, we will be bringing new modern experiences and capabilities focused on:
- Password governance: Systematic, intelligent password management capabilities enhance identity security. They simplify compliance management, safeguard critical data and maintain secure digital assets.
- Centralized entitlements: A single, centralized location for permission and privilege management ensures consistency across your environment. It enables rapid response to changes and supports scalability.
- Just-in-Time (JIT) access: Zero-Trust architecture provides users with time-limited permissions only when needed. It creates a system better equipped to adapt to constantly changing access requirements.
- Identity behavioral monitoring: Bravura Cloud enhances threat detection by analyzing trends in user behaviors to proactively identify and respond to threats — including insider threats.
These capabilities enable Bravura Cloud to mesh beautifully into the Bravura Security Fabric and expand its reach, further reinforcing your cybersecurity posture and simplifying your overall system.
The Bravura Cloud Process
We can most effectively explain how Bravura Cloud works with this three-step process.
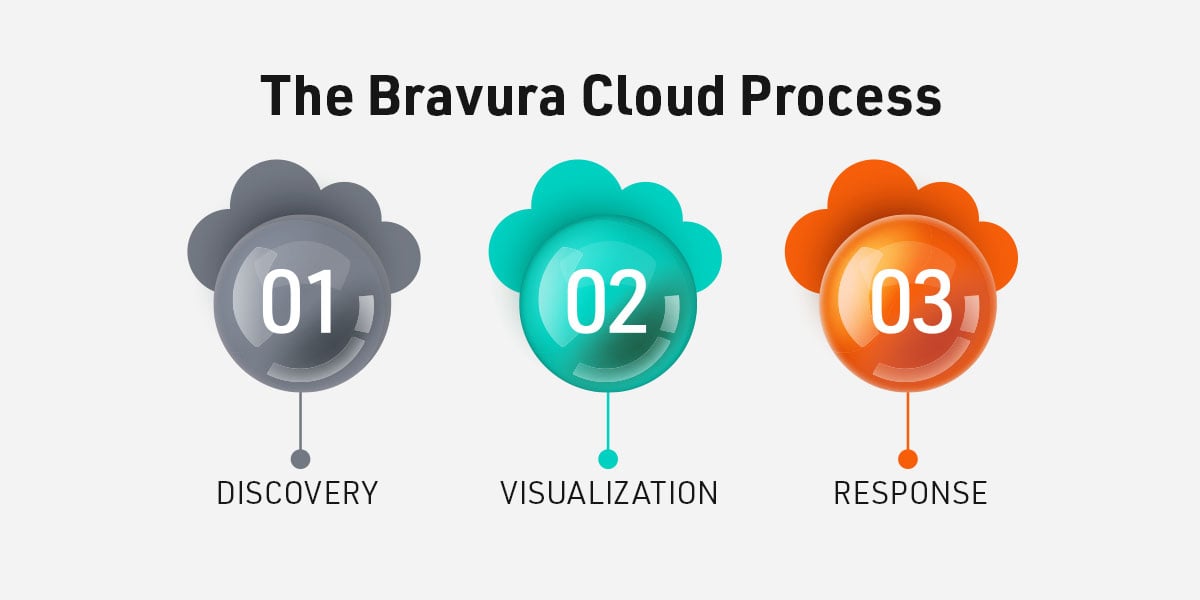
1. Discovery
Data discovery is one of the most important steps in data security because it gives you a complete understanding of the data you have and how you need to protect it. This deep understanding is essential for:
- A robust security posture
- Simplified compliance management
- Accurate risk scoring
- Insightful analyses
Bravura Cloud leverages REST APIs, which enable the tool to interact with RESTful web services — cloud-based services that conform to the Representational State Transfer (REST) architecture. Through this interaction, we can extract valuable data from existing instances and import them into Bravura Cloud, unlocking total visibility into your data and cybersecurity environment.
Additionally, bring-your-own-data capabilities enable you to configure your own database using open-source programming languages like GraphQL and SQL. You are the real-time master of your data — Bravura Cloud simply allows you to maximize its power.
2. Visualization
Raw data can be difficult to understand, leading to inaccurate or incomplete insights and holes in your security. Intuitive visualizations — charts, graphs, tables and more — help illustrate the full store of your data so you can take the most informed actions.
We designed the Bravura Cloud platform to provide a simple yet rich UX, with powerful dashboards that allow you to understand your entire data environment at a glance.
Whether you use Tableau, Excel or Power BI, you can integrate your own Business Intelligence (BI) tools and data services directly into the Bravura Cloud platform for seamless data transfer and analysis. Plus, internet connectivity means your authorized users can access this data from anywhere, on any device.
3. Response
Taking a proactive approach to cybersecurity is the most effective way to protect your organization from internal and external threats. Bravura Cloud's built-in threat monitoring and response mechanisms kick in immediately upon detecting a potential threat, significantly reducing your risk of suffering an attack.
Here are some examples of how it works:
- Notifications: When a threat is detected, the platform will notify users via their preferred communication channel, whether that's email, chat or SMS text.
- Automated workflows: Bravura Cloud automatically creates service tickets to kickstart threat elimination measures upon detection — which can save your organization thousands in losses by helping you take care of problems faster.
- Leverage FaaS: As a subset of serverless computing, Functions-as-a-Service (FaaS) is a cloud computing service that simplifies security responses by allowing users to execute code without having to manage complex microservices infrastructure. FaaS is highly effective for high-volume workloads, such as data processing and aggregation.
Supported Use Cases
Bravura Cloud is a thoroughly modern solution designed to support advanced use cases and capabilities, such as:
- Frictionless password management: Combined with the Bravura Security Fabric, Bravura Cloud is a powerful password manager. Built-in automation can randomize your password and retrieve it from Bravura Pass or Bravura Safe for JIT delivery, eliminating the need to remember or create new passwords.
- TaaS: Bravura Cloud allows your organization to get access to best-of-breed cybersecurity and data management tools without the associated costs, research and deployment hassle. Your IT requirements will be simpler, but you'll have significantly more advanced software at your disposal.
- Containerization: Bravura Cloud runs on Kubernetes, which is Google's open-source platform for container management and services. Leverage extensive microservices without needing to navigate the complex infrastructure behind them.

Review the Full Session Transcript
No time to watch the session? No Problem, Take a read through the transcript.
Carolyn Evans (00:00):
About everything that's new and get to engage with you. So in today's keynote session ending complexity with the new Rivera Cloud, Nick and Ian are both going to introduce something that's very exciting. We think you'll be very excited about it as well. Nick Brown, he is our chief executive officer. Nick comes to brave Security with over 25 years of experience in enterprise software with innovative startups and large companies like SAP and Oracle. And then Ian, who will be diving into Brave Cloud with you is our Chief technology officer. So Ian is very passionate about software development and customer relationship management. He is very excited about solving problems that organizations face to help shape the future of cybersecurity. And with that, over to you Nick.
Nick Brown (00:57):
Okay, great. Hope everybody can hear me now and excited to be here with Ian and kicking off our power of one conference with everybody. So welcome and let's get rolling. So just a quick safe harbor. Won't read it. We're talking about some future features and functionality in our product that we're in the process of delivering to market, including what we already have available and launching today around Vera Cloud. So you'll see this probably throughout the sessions that we're presenting as we're trying to keep you guys up to speed on where we're going and what we're doing to help move our products forward for our customers.
(01:39):
So talk a little bit about the past year just to give everybody a baseline of what we've been going through during the past 12 months. It's been an exciting year and just to highlight a few things that have happened to us along the way here. Our name changed. We got acquired by the RIS Group a year ago last September, so it's hard to believe A year's blown past. RIS is part of Constellation Software, which comprises over 1500 enterprise software vendors in the markets and we're excited to be part of that team to be able to collaborate and learn from each other and help us then deliver better software solutions for our customers. During the year, we launched two new products, brave, reverse, safe and Bravero One-Off to really help bring better password management and passwordless security to our customers, leveraging these new technologies and new products that we've released.
(02:40):
At the same time, during all of this movements and change, we've been driving innovations within our security fabric, especially around our three core products of past identity and privilege. And then today we're announcing a new way to add more value for our customers in Revera Cloud. And to kick everything off for the power of one, I just want to take a moment to thank everybody for joining us. Thank our partners for supporting us in the event and clearly thank a couple of our customers who are here presenting their experience and their journey, both the good and the challenging or the bad you might say, but excited to be presenting with them and hearing what they're seeing and what they're excited about in our products and working with us as a vendor.
(03:36):
Just looking back at the last year, some highlights of a few of the core features and capabilities we've added to our platform and our core products, as well as the ongoing innovation we're doing with new products that we're delivering to market. You'll see a lot of focus in our core platform around APIs and ensuring we're modernizing the ability for folks to get access to the data that's within our applications, to be able to express that, build user experiences, integrate user experiences through the hard work we've been doing primarily in our 12 X line of the product. We're also looking at how we can make it easier to kind of proxy in for our SaaS solutions and get data out of your on-premise solutions and deliver those to the user experiences. We can supply through the cloud on Vera Safe, we launched it, but it continues to be a product where we deliver value about every other month.
(04:40):
We do about six releases a year on safe and add additional value that we hear from our customers and clients and react nimbly and quick to those requirements. We've added the ability to unlock on device integrated with SAML Federation, created a variety of different experiences including desktop apps and always trying to make sure that everything we provide has a high degree of self-service and reliability for your end users to be able to identify themselves and get back into the system and reset whatever they need to as far as passwords go. And then finally, with all these secrets and all this information kind of pooled into these applications, we wanted to beef up the security around those applications and delivering and then making sure it provides you with a passwordless way to access safe privilege pass and identity we thought was critical for our customers and for modernizing your platform with some Fido two compliant type capabilities delivered to your enterprise.
(05:50):
But moving on a little bit about our thinking and how we've evolved. I've been with the company now, it's hard to believe almost three and a half years going into the fourth year here of our journey together as an organization and really driving hard around a strategy that we can share with our customers, get their feedback on it and really working with our customers has been how we've come up with our strategy and how we do things and also why we're delivering a product like Vera Cloud to the market, which would be the primary focus of what we share with you in this session today.
(06:30):
So our core product principles as a team from sales to customer support services and engineering, qa, what do we think we want to deliver to our customers as we innovate in our product? So one is how can we give you immediate value or even more value by unlocking what you currently already have from us in your solution? Either making sure you can adopt new capabilities of the product or exposing and surfacing the data and the insights that are maybe locked behind three decades of development that we've been doing and how we store and retrieve data internally within our system. But how do we then get that out and expose it to our customers and focusing on a user experience and the ability for not only us to build great user experiences and modernize the look and feel of our applications, which if you're a customer, you may have asked this many times of us, we're focused on it, but also allowing you to bring your experiences to the table and delight your users so that you have higher adoption, seamless use of the products and the tools that you need users to be excited about so that they're providing the highest level of security and participating in a great security program at your companies.
(07:57):
To enhance this even further, we've gotten really focused on standards and making sure that we are an IT friendly application that lands into your domain and into your organization in a way that makes it easy for you to use our capabilities within our product and in connection with other products that you have and that you need. And as we evolve forward, we want to make sure we're providing a unified way to deliver our capabilities on our cloud, your cloud, their cloud, so that whether you're deploying our products in your data center in a private cloud that you've acquired from AWS or Google or Microsoft or you're using our SaaS solutions, we want to make sure you're getting the same product that everybody can choose from and really making sure that the choice of where you deploy it doesn't compromise the functionality that we can deliver to you. So these were principles we established that I think became the foundation for what we feel we want to move forward with.
(09:06):
So as we looked at the Vera Cloud solution, we really broke it down into the processes that we feel we can support and deliver. And so the first part of the process is discovery, right? What is in your landscape? What is your security data look like? How do you apply different filters or views on that data that are important to you if it's for compliance or risk scoring, because we're all trying to make sure that our solutions are providing the security we say they are and we can prove it, we can analyze that data and maybe find new insights and new issues that are surfaced because it's easy to get access to. And a lot of times you need to bring your own data so there may be other systems that aren't currently integrated with Vera security platform and that data might be important to bolster your analysis and provide new insights.
(10:05):
Once you discover that the only way to make it useful is ensure that you have a great way to visualize that data through rich user experiences, building powerful dashboards that help you quickly monitor critical areas of your landscape that you are very interested in, maybe bring your own user experience, whether that's a custom application or portal or a third party application you want to integrate with. Very important there. And then making sure that the data that we put into revera Cloud can leverage off the shelf BI tools, whether it's Power BI or others that you might be using. Some people maybe even use this one called Excel as part of their process and we want to make sure it's easy to get access to this data, analyze it with tools you're familiar with, and discover and understand what you need to do to kind of fix any issues you're finding in your response and highlight what you're doing really well.
(11:11):
And then finally, getting all these insights, it's great if you can take action. So how do we create an environment where you can respond to what you're seeing, notifications, simplifying and unifying the way we do notifications and then enabling all notifications to have a channel output, whether that's email, traditional approach or chat or texting or whatever. Just want to make sure that you can see and alerts and get immediate action happening within your organization and create service tickets in ServiceNow or any other solution you might be using there. And then we provide a library of what we're functions as a service where if you see an issue in Vera Cloud, you'll be able to address those issues with functions that you can use to fire off into the core platform and update and fix any issues you see in your landscape.
(12:12):
So just to give you a picture of what things look like at a very high level, we have on the left hand side our reverse security fabric, which includes the five products we've talked about on the left, integrating the data from those solutions and the events that are happening in those solutions and log files and everything and pushing them into Vera Cloud in a kind of pub subtype capability that's available, which allows you then to in Vera Cloud, do just in time functionality, monitor behaviors, threats and risks to your organization, use password governments to help you do vaulting and self-service centralized entitlements. And the core of what's in VER cloud two is a security data engine that helps us take data from our system and other systems and transform it into a representation or a schema that allows you to deliver and find insights in that data and integrate that data into other tools that you might be using. And as I talked earlier, making sure that you can do this in the deployment model that you choose from, whether it's our cloud or yours or your data center. With that, I think I'm going to turn it over to Ian. He's going to talk a bit about how it looks like some technical things that might happen to make this work and then go into a demo. So Ian, I'll let you take it away. Thank you very much,
Ian Reay (13:53):
Nick. So yeah, so just to carry on with what Nick was talking about here is we're going to walk you through how cloud can bring some immediate value to the existing investments you've made with the reverse security fabric, how we can consume the data that already exists in your existing environments, how we can surface insights, how we can help starting to identify risks that you might not be aware of yet. And with this strategy that we've implemented, we wanted to again make sure that we could do this quickly and easily without any kind of disruption to your existing programs and make it a seamless experience to begin this journey here. And to do that, what we've done is we've implemented Discovery ETL service. What it does is it extracts the data out of your existing instances back to 11 oh is what we're supporting back to.
(14:55):
So maybe about six or seven years old. We can then extract that data, we can then transform it and load it into River Cloud Cloud being a built on top of a SA native infrastructure, Kubernetes is a foundation to that with the data storage scenarios that we need to really power our future here to be able to represent data in the ways that allow you to really power great analytics and new user experiences, be able to drive operations and processes such as what Nick was alluding to, like the functions as a service, and be able to monitor and observe how things are working properly, be able to bring in modern authentication approaches and then surface this content through really compelling APIs, designed for analytics, designed for user experiences, and also designed for being able to subscribe real time for updates.
(15:58):
If you see accounts being added to a sensitive group and we can notify you in real time about that, you can then take action and assess that, whether that's desirable, whether that's undesirable, whether you need to take an action immediately on that time can matter a lot. And so being able to do real time subscriptions and real time notifications we feel is key to going forward here. And you'll see that being a key element of our go forward strategy. And then on top of that foundation with great data, great operations, great authentication and authorization, building up new user experiences, and in this demo we're going to be showing you our discovery cleansing inventory and governance stages do we feel are really important to be able to build up that foundation, get rid of some of the identities and content that might've served a purpose in the past but now could be orphaned or unnecessary.
(16:55):
Be able to build up that inventory of identities and have confidence who has access to what in your environment, and then be able to govern it and be able to identify changes to this that's going to occur over time and be able to surface problems and risks and be able to adapt policy changes that will occur. And so I'm going to start now walking you through the steps here of what this is here and quite excited to share this with you here. Just one second here. It looks like Nick, I might need you to stop sharing. Thank you. And then I'm just sharing my screen here.
(17:37):
And so what Nick has highlighted here is that VE cloud is being built on new user experiences, standards driven strategy. We want to make sure that we're supporting the standards moving forward, that people need to have confidence to secure their platforms. And so under here we've introduced new authentication service here currently and it supports SAML and IT supports OAuth, OpenID Connect, and really gives us that foundation that we can grow off of here. In the case of the demo here, I'm just going to log in with Azure. We're going to be talking about some enablement sessions that we're going to have in the future here that allow us to start talking about how people can start to develop seamless authentication strategies around password change experiences using some of these modern standards and protocols here. Really excited to have those. We'll be sending out some details here after this demo here.
(18:39):
And then getting people in to user experiences that are modern user experiences that are pleasing and ultimately backed by the APIs that we're talking about here. Being able to build up a dashboard so you can see your real time state here when discovery is running and you're seeing the numbers tick up and tick down, that can give you a lot of confidence that you're in control of where you're currently sitting at. And coupled with our persistent listing capabilities out of ad and delap and whatnot, and we are introducing that in our SaaS platform here in our November release here, being able to provide those capabilities so people can really have confidence that they're seeing a real time view of their current, of their posture that has some real opportunities to it here and see those trends over time here about identities being created and deleted groups users and building out these dashboards is going to be a key theme that you're going to see in this presentation here in this UI too.
(19:44):
We of course are making sure we have the fundamentals such as standard experiences that people prefer such as light and dark themes, the ability to do custom themeing quickly and easily that yourselves as customers can drive yourselves without needing to engage in any kind of services engagement to do theming. Of course, having translations, we will be shipping with our full suite of core translations here and that these are ones that are simple and easy to extend further. Furthermore, also making sure that this is accessible on day one. Accessibility is a key topic. We understand that for many of our customers, making sure the experiences here are things that can be pleasing for people who might have a visual disability that can often impede their ability to interact well with software. Now as we're so going back to where the discovery layer is here, we've integrated this with one of our demo environments where it's one of the demo.
(20:50):
If you've had a session with people from our field of enablement team or sales engineers, then you've seen those demo environments where we have a range of different systems in there and they have a range of different accounts. This is one of them based on 12 six as previously stated. This can go back to the 11 oh version of our product suite. So we have quite broad coverage in who we can offer these new user experiences towards. Once we've discovered people's content, we can then pull it in to this user experience here where we have a list of the users that we've discovered from your platforms. As you can see here, that wealth of both legacy and modern platforms that we can discover from they're here. You can get that overall view. You have quality of life elements such as being able to quickly and easily search and filter accounts based on the platform that they're in or the application that they came from.
(21:48):
Be able to do simple things such as choosing which columns to display and once you've chosen the columns to display, also change in the ordering to them being able to export. One thing, as we've been talking to our customers, one of the key driving themes is they want easier access to the data so they can work it, they see a problem on the screen here, they want to take it and share it with a team member or take it offline and work with it here. And being able to just quickly export this content here in a csv, then you can take it offline and work with it here. And that is what you see on the screen here. That's one of our key guiding lights. And you're going to see this through this presentation around how can we make it easier for people to get access to the data to do their jobs well?
(22:45):
And so that's where you'll see this whenever you see a search engine. We want to make sure we can export the data. Whenever you see a dashboard, we want to make sure that you can get at the underlying data backing that quickly and easily and then when you're going, so this is kind of a key element of starting the process of surfacing the risks and problems that you might not be aware of in your environment. And so that's where we're starting to introduce a new concept that is compliance rules. And what compliance rules are things that can apply a rule against a user, a group, a system, and it applies checks. And if people fail those checks, then of course we can surface that here in this user experience, we can record that failure. We can also see if they were in compliance, now they're falling out of compliance on a topic and we're building up a library of these compliance rules that allow us to ship a number of compelling ones that commonly are needed by most organizations, but then also to encourage people to start to extend those rules.
(24:07):
These rules are being so you can click into them, you can configure them using this wizard style of an experience. The rules are based on the same strategy that you're seeing in the UI around an API first strategy and a standards based strategy. So we use the API to allow us to define a query that allows us to surface the identities that that compliance rule should apply to. In this case, we're defining a query where we're surfacing all users that have a primary email specified and then in order to do a check, what we're doing is we're also getting that user's family name and given name because those are key pieces of data in the email policy that is being adhered to. Then we're leveraging a standard that has emerged in the open source community in the last few years that really has significant power because of that power.
(25:04):
People are adopting it for a wide range of policy decision points, and that's open policy agent and open policy agent defines policies in this format here. This is a rego format here, and it's been proven to be able to handle some of the most complex policy decisions that you're going to have. And so we're going to ship a number of these as baselines, but we're also going to encourage people that if they need to extend them, if they need to customize them, if they want to build their own, but they can do that. But one thing too that you're going to see here is trying to think through what is a modern user experience In this context here, because policy is a challenging topic, many policy tools start to rapidly look like kind of an airplane cockpit with all of the options and nos and buttons that need to be exposed to allow you to define policy.
(26:05):
And that's where we're exploring an alternative way of doing this because we're actually using some of the generative AI platforms out there to help us write these policies, to help us write these queries. We give the generative AI or schema, we give the generative AI our goal for the policy, and it's actually extremely good at generating these items for you. So as we're exploring here, is that a better user experience where you can ask in natural language, I'd like to find all my users who have an email address and I would like to then pull out their family and given name. Then I'd like to confirm that their email address is in the format of given name, family name at our company. And that is significantly easier for many people to understand and take part on both to generate them. But also too, when you come back and you need to review these compliance checks, try and figure out if they still meet your needs to be able to quickly summarize them too.
(27:14):
And so you could ask the generative ai, could you please just explain this to me? Explain it to me like I'm a five-year-old because again, these things can get complicated. Can you just please walk me through the basics that can really help in allowing many people to take part in this and assess it and ensure that the rules and checks that you're applying reflect your needs as an organization. And so then as we go through this, we can then start to surface some of this material. We want to be able to surface this in a really good way that allows you to get access to access to the data that you need to make decisions when you see a compliance failure. Compliance shouldn't be a question about what the next steps are. Those should be known and you should be under control over what those are.
(28:06):
And this is where we're introducing a new analytics platform that allows people that we will be shipping dashboards on here that really provide a lot of wealth and common scenarios such as an overview of your user population, a breakdown of inactive and active users risk scoring, which we'll get into here in a minute, as well as a breakdown of your infrastructure based on the platforms that are in play here. So you can see the number of active and active users across your environment here, like the active users are ones that currently have an accounts on the assistant inactive ones are historical, and through tracking for auditing purposes and be able to see breakdowns of these compliance rules, both the ones that are in progress that you might be working on that might not have been run yet, but the ones that have been run such as employee password palsy, adherence or email consistency check that I was just talking about here.
(29:04):
And so people can go through and define these compliance checks and then start to understand how compliant are they, how good are they, how about are they? So in the case of in this environment, if we're checking against email policy adherence, that check is maybe for every 90 days right now, 45 of the accounts that we can observe are from passing of the ones where we contract password policies too, a thousand of them are failing. Now what does that breakdown in this dashboard here we can start to surface the breakdown of ones that past and then understand and easily gain access to the breakdown of the users who are in violation. And again, one of the simplest steps that you can do here around users in violation is identify your users, identify their manager and ask them, it's your responsibility to fix it So we can inspect this, we can get access to the data, people can download this data as a CSV.
(30:10):
All of this is editable and configurable by you so we can start to surface the content here and that way people can take this offline and work this through properly, figure out the next steps that are going to be necessary to carry this forward here. And so that's a simple way of going about here, but with our capabilities with the functions of service that Nick was alluding to here, we're starting to get opportunities to make this significantly better for you because you can send an email for this or you could potentially fire a function for each one of these asking for that password to be changed or for that account to be disabled. If it's in violation, either change that password or disable the account. If you were to say change the password for them, then you could have that password maybe get automatically synced into the user's ver safe, which we have offered a new connector for in this year.
(31:24):
That way people can sync these passwords into reverse safe, and then when people need those passwords, you can gain access to them quickly and easily. That's actually how I am operating at reverse security here is I have randomized passwords for everything. I use the reverse security fabric to put new randomized passwords in for me. I then store them in safe and if I need them, I go in and get them. And it's actually really frank because I don't have to remember these passwords, especially as we all have to adhere to stronger password policies, like 15 character password policies. We want to make sure that we are keeping these things quick, making sure that these things are smooth and easy, and that's where we have opportunities for driving these kinds of tools and capabilities here. And so that's where I'm really excited. We're going to show some enablement material on this year and coming up webinars we're going to get into after we're done the demo here.
(32:29):
I'm certainly looking forward to talking about this more with you. Now, this we want to make sure is user edible, that people always have access to be able to configure these and use these analytics that both we provide and that they can extend. But we also, because we're adopting a GraphQL style of an approach to these analytics, we can also support third party BI tools. Again, Nick was alluding to this earlier in the session here where people can bring their own reporting platforms. This case here, this is a video of one of our employees who tied up cloud instance to Tableau. And this is just using off the shelf integrations with Tableau and GraphQL APIs and people can start doing these rich reports and scenarios using the tools that they're familiar with. That way then they can present this in ways they're familiar to decision makers and people can really identify their best paths going forward here when they see problems, when they need to prove correctness.
(33:41):
These things can be done now and the tools that you are comfortable with and that you're already using just to make things quicker, simpler, and easier for everybody. And this is something that is already fully because of our focus on standards, both in APIs and authentication and in authorization around what people are allowed to see. And so that then allows, so with this wealth of data that's now been assembled through these APIs, we can now start to think about with all this data, how can we really assess the risk? Because when you have 18,000 accounts, it can be very tedious, pretty error prone too to really go through and earnestly come up with an assessment about how risky are each one of these accounts. And that's where right now, one thing that we're doing in coordination with our parent company, Polaris, is exploring the opportunities for how generative AI can help with doing assessments.
(35:00):
In many cases, the AI can come to very similar assessments that people can, and it's just that if you're being asked to do 18,000 assessments, that's both costly and people get tired, people, their decision-making capabilities drift over time. And so an AI doesn't, and the ais are very effective at understanding and determining common things such as what a description of a group entails, what a target system platform is, it understands what SharePoint is, it understands what a admins group is, it understands when people use shorter acronyms that might really be hard to write a rule or a check for in rule-based systems, the generative AI cannot see through that and it can read it like a person and make an informed decision that this is probably a sensitive group. And if you have access to SharePoint, people are probably going to be motivated to do it because again, knowing about this area, people will be motivated to compromise the administrative rights to SharePoint.
(36:07):
They will then also be able to potentially discover it a little easier. They will then be able to dig into and understand what kind of risks are there because again, the risks of SharePoint versus the risks of say like Microsoft Dynamics are quite fundamentally different in terms of financial and confidentiality and privacy related information. They could be getting exposed. So can help you surface this stuff here and make those assessments a little quicker or a lot quicker because again, like a cent per assessment and a few seconds per assessment and then you run that assessment, you are overall generating your risk profile using some pretty compelling capabilities here, especially when you factor in how this data engine it can see for a user, can see the groups that it has, the accounts that it has, plus compliance checks that might be good or bad. And if you have a lot of problems with compliance checks where there smoke there, fire principles could apply that people might need to look into here a bit more.
(37:09):
And so we have these wealth of capabilities here that we're building up on this platform here as well as we want to make things easier for people to consume, we want them to have a more pleasing experience. And this is where as we start introducing sort of a toolbox so to speak, of really good and rich capabilities that we offer, but then also other people can do, we can start to have better experiences such as a better email experience. I just leverage these APIs to send myself an email around a risk assessment. And so again, a well formatted HTML email where people can call out and emphasize certain areas that are important. This data is just being pulled through the API. And then people can also decide whether you want to do this based on events. Events like all events such as all risk assessments, being notified of all of them, maybe only being notified of some risk assessments, maybe ones for your subordinates or people in your department or also ones where risk scores are above or below a certain level.
(38:17):
These kinds of things we want to make simple with the upcoming functions as a service capability really make people give people the tools so that they can hone and drive and react to real-time events in their ecosystem while also being able to enhance the usability of this, ensuring that people have a good experience going forward here. Email is just one chats of course or another. That's where we want to have this flexible platform so we can add these tools quickly and easily to people's platforms so we can react to their needs very effectively. And so that's where now ultimately out of all this year is trying to really focus on standards, focus on APIs, focus on usability, and making sure that this is something that you can have access to as a SaaS hosted service or also be able to gain access to this and something that you host yourselves if that's something that you need or want.
(39:28):
That's where one of the principles that we're backing here is our cloud, your cloud, their cloud where people should have the freedom of being able to gain access to this. Now we are of course going to offer in the early access program hosting in our cloud for people. We are going to provide guidance and information about how you can start to host this if you so choose to host it here. And that's also where it's part of this infrastructure here. Using the analytics platform here is giving people the tools to be able to maintain this if they choose to do it, such as gaining access to the application log, it's gaining access to the performance details of how things are reacting, gaining access to user experience, tracing in case people in your organization might have a complaint, making sure that people have those tools so that they can offer a really good and compelling experience regardless of which cloud environment they're working in. And so those are things that we'll be covering in some upcoming webinars and enablement material here about what does it look like if you want when you are exploring cloud native applications that such as proof of cloud that you are going to be hosting internally yourself here. So certainly a lot of very compelling opportunities in our near future here and certainly things that we're looking at talking through and socializing with people here.
(41:03):
Now, one final thing that I might do here is just highlight how we've started to think about generating enablement material for if you wanted to bring your own user experience to play here. So what we've done is we have created a bring your own experience. It is meant to be enablement material and it's meant to show how the APIs that we're bringing here are ones that people can use to bring new and compelling experiences to their customers. So one of our customers came to us asking about being able to do an immediate password reset on account, the account gets created and then 10 seconds later you need to do a password change on it. And that's something that our discovery layers, again, we discover, we build up a profile, we're building up the identity representation of people. That's just something that was something that we weren't able to offer historically.
(42:08):
Now under the Bera cloud ecosystem, we can potentially take action a lot more quickly and robustly to allow people to do an immediate password change on account that was just created. Then we're also in this video here now introducing a second, bring your own user experience. The second one is around a just in time request for a role where people log in with that new password they just set, provide a ServiceNow ticket number, be able to select the LDAP group in this case, but also applies just generally to roles. Then we can in real time put people into that role. That way the next time that they log in, now they have that firefighter level access to be able to see the background details of this application so that they can take action and maintain 'em. And so these are just a few kind of enablement examples about how people can do things quickly and simply in both of these cases.
(43:11):
These are very tiny Python applications that do not require any knowledge of building web UIs to build. And just kind of an example of things that can be done right now as well as say if people want to bring chat experiences to play here, these exact same APIs and capabilities can be leveraged in that scenario too. And so we want to enable people to be able to bring these kind of capabilities quickly and easily if they so choose. Of course, we're going to build out our experiences, we're going to modernize a number of the experiences that you and your employees are already using, but if you wanted to embed into an existing help desk experience, embed into an existing chat app strategy that you might be driving forward here, these things can and will be available easily as we generate enablement material and introduce you to these new APIs and capabilities and that way too, find the right fit for people moving forward here. So I know that's a bit of a whirlwind of a demo, as you can tell, we've been working through quite a lot of content and trying to handle a number of things we've been hearing from people from as we're talking to you and hearing about what some of your friction points are here. And so I think I was thinking maybe we could move on to the next day share we talking about some of the future enablement sessions we might be doing here.
Ian Reay (44:48):
Awesome, Ian, go ahead and stop sharing it. Sounds good.
Nick Brown (44:56):
Okay, so just to provide you with some next steps and then I think we can stop and take some time for questions. It looks like we have some time to do that, so I'll let Haley or Kalin make sure we stay on time. So next steps. I think Ian's taking you through high level the overall platform that we're supplying with revera Cloud and some of the functionality you'll see there. Really what we're trying to make sure we do is get the data into an environment that allows you to explore it without disrupting your production system, but then actually go back and update your production systems as needed. But making sure it's fast, it's easy to integrate with and move forward. And during October, November, based on the Vera Cloud platform, we're going to be talking about frictionless password management tools as a service. So how can we deliver functions and tools and capabilities as a service to this data set.
(45:57):
And those are the October webinars that we'll be publishing and are on our websites in November. We're going to really focus in on standards based just in time access, which I think Ian just demonstrated at the end how I could request access and then my access was revoked at the end of the video once I no longer needed it. So making sure we're not creating standing privilege and making it easy to go after what people need to do their jobs. And then finally, as we talked about in this, we've been exploring AI within our group and within RIS and how we can leverage AI and natural language search to make it easier to answer complex questions and provide the capabilities in our platform for people to see and interact with new technologies that I think can make their experience easier, better, faster, and secure.
(46:57):
Finally, just to give you an idea where we're at with our Vera Cloud release planning, we have our first version of the product out today working on a limited access program with about 10 key clients that we're pursuing. So during October and November we'll be gathering feedback, implementing new capabilities in the platform as we work with customers to think about what are the new insights we're seeing together just in the past few weeks demoing to some key customers and working with them. We've found all kinds of new values that this solution will supply to them that they think are really, really valuable for their company. I make things better. So if you're interested in exploring more about Vera Cloud, getting a demo based on your situation and where you're at, please just reach out to your account manager. We also have a webpage where you can request a demo and see if you're interested in a limited access program. I think that will be great. We're seeing a lot of excitement here and initiatives, so look forward to hearing from you. And then in November we'll be shipping the version of the product that will be generally available to anybody as we move forward. So really quick timelines, great experience, a lot of work went into this over the past 12 months and we're excited to see where we're at with Vera Cloud. So it's an exciting time for us and hopefully you see some value here for you as a customer, ofra security.
(48:39):
Alright, with that maybe I'll pause for q and a if there are any questions. Otherwise, thank you all for attending the keynotes and look forward to the rest of the sessions today.
Carolyn Evans (48:55):
Alright, so if you have any questions, please pop them into the chat button window, sorry at the bottom. And I think we had one question about any other specific integration with reverse security solutions that you can touch on,
Ian Reay (49:16):
Ian For sure. So one of the things that you'll see both for our existing releases that have come out since 12 three and our future release plans is continuing to build out the rest APIs and past privilege and identity. And that allows us to leverage a lot of those critical and core capabilities that really can add a lot of value for discovering and targeting from a lot of the systems that you've already put a lot of effort into targeting and that are on-prem environments that will not be SaaS native. And so we really want to encourage people around thinking about what these tools like the functions as a service, what that could start to look like when you can create accounts, update accounts, delete accounts against any of your systems, add and remove group memberships, add and remove groups, change group owners. Those are all things that are currently capable that we are currently capable of doing in 12 three versions of past privilege identity.
(50:28):
And so as we're surfacing tools in Provera cloud for doing this, people can invoke these capabilities through either the existing REST APIs and past privilege identity or through the functions of service tools that we're introducing through Vera Cloud. Then we can really start to surface a lot of the hidden value that we have for cleansing your accounts, for doing corrections to them, for removing orphan accounts, for being able to remove dormant ones or be able to disable dormant ones and then eventually remove them if they're not being used. So there's a lot of opportunities there. Furthermore, also, we're getting a lot of feedback that people, that they really want to bring our workflow details into cloud, that they want to bring our event audit history into Provera cloud that they, and again, one of the most thought provoking ones is what RA privileges session recording starts to look like under the data stores and the APIs and the ability to do the new alerting and risk analysis ina cloud.
(51:48):
That's certainly a very, very thought provoking topic that we'll be breaking into quite a bit in the next year here as we're going forward here. And so one of the key things here is we want to surface this value, we want to make it easier for people, and that's one reason why we're investing heavily into the rest APIs that we're doing in 12 three and newer versions is to get people those tools to really drive what some of their future could hold. And also one reason why I say we introduced the fine-grained access controls in 12 six so that people can really control the scope of what those tools are allowed to do, make sure that the tool is allowed to do approved things and not necessarily other things. And those same principles of fine grain access control are going to be getting applied in Provera Cloud. So again, you can have confidence in this. And so that's where key top of mind is how do we surface value quickly and easily here. So
Ian Reay (52:55):
Further questions.
Carolyn Evans (52:58):
Okay. Yeah. Thank you Ian. I think those are all of the questions that we have right now. Thank you everybody for joining. We will send you an email to register for all of the four upcoming deep dive webinars on all of those topics that Ian had touched on and look for those. And we look forward to talking with you again soon.
Ian Reay (53:26):
Thank you everybody. Thank you everybody.
