Re-imagining: Passwords, Defense, and Your Culture of Security
WATCH ON-DEMAND
Contents
Read straight through, or jump to the section you want to read:
As cybersecurity threats continue to escalate, traditional password management strategies are failing to keep pace. Our expert discussion delves into the heart of password safety issues, unveiling the stark reality: a significant portion of breaches stem from inadequate password management. With 86% of analyzed passwords lacking uniqueness and 21% easily guessed, the call for a transformative approach to password security is clear.
This webinar explores how to engage users with a password-free feel that also serves as a stringent, first line of defense. Learn how to create a dynamic security culture that empowers users to rely on innovative and automated best practices that transform your password management defenses.
We explore how to revolutionizes password practices by introducing password rotation—a feature usually reserved for Privileged Access Management (PAM)—into everyday password management, empowering users with continual access to password vaults and administrators with one-click re-secure capabilities to halt breaches before investigations even begin.
Key Takeaways
- Understand the current state of password management and its pitfalls including the human element
- Gain insights into the disconnect between user responsibility and organizational accountability
- Review the essential shift from expecting users to manage complex passwords to empowering them with smart, user-friendly solutions
- Learn how to dramatically reduce help desk call volumes and improve productivity with innovative password management solutions
Why Watch
If you're seeking to align password management with your business's security objectives and drive urgency in addressing password-related risks, this webinar is a must-see.
Speakers
-1.png?width=300&height=300&name=Circle%20No%20Background%20(1)-1.png)
-1.png?width=300&height=300&name=Colin%20No%20Background%20(2)-1.png)
Bryan Christ
Bravura Security
Sales Engineer
Bryan specializes in security and access governance. For more than twenty years, he has focused on open-source and software development opportunities with an emphasis on project management, team leadership, and executive oversight including experience as a VCIO in the Greater Houston area. He was recently published in Cyber Security: A Peer-Reviewed Journal.
Ian Reay
Bravura Security
Chief Technology Officer
Ian is a key member of the executive leadership team, accountable for leading a mature, scalable, and high-performing development organization, delivering all engineering-related activities. He started out as a developer with the company in 2006 and has taken on increasingly large roles in developing the company’s identity, privilege, password, and passwordless strategies and solutions. Ian's responsibilities include setting technology and tooling direction, prioritizing feature requests, managing release scope and timelines, the build infrastructure and UI/UX.
Webinar Poll Insights
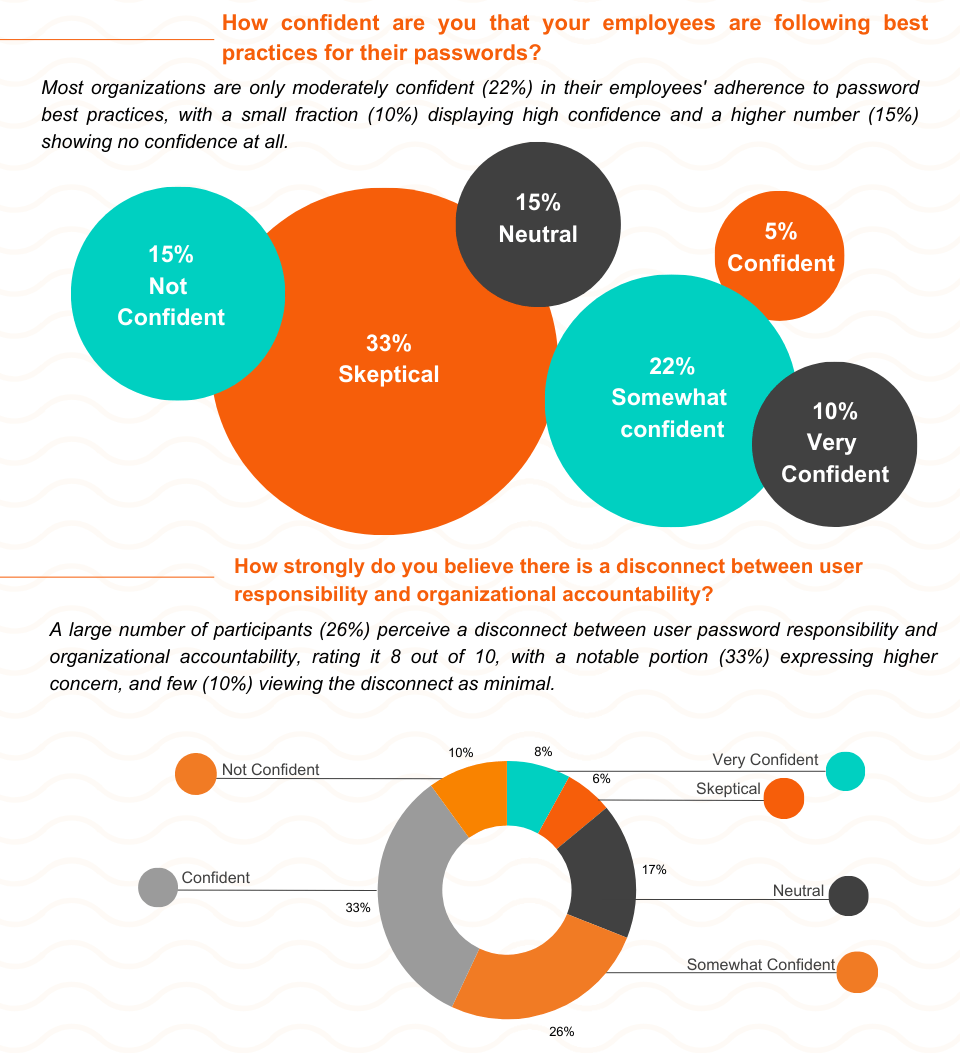
Clarifying the Gap Between Individual Responsibility for Passwords and Organizational Accountability
During the webinar, a series of interactive polls were conducted to gauge the disconnect between password user responsibility and organizational accountability.
Uncover the current pulse of password security with insights derived from our comprehensive poll, designed to highlight the challenges and attitudes influencing security practices. See how your organization measures up.
Assessing Trust and Accountability in Password Security
Amidst moderate confidence in password best practices and notable concerns about responsibility-accountability alignment, enhancing trust in password security emerges as a critical priority.
Transforming Password Culture: Empowerment Through Smart Technology
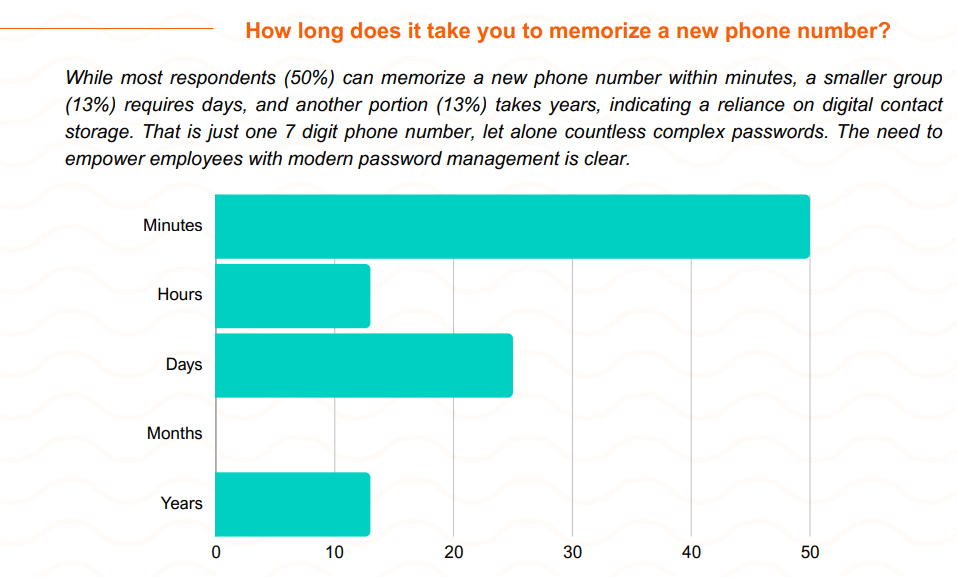
Our exploration into password practices has revealed a landscape as complex as the cognitive networks involved in memory. Just as we have transitioned from memorizing phone numbers to entrusting them to our smartphones, we should similarly evolve our approach to password management. Employees now anticipate a password experience that aligns with the effortless and intuitive interactions they have with their personal devices. By equipping them with user-friendly password vaults, we're essentially enhancing their digital memory, allowing them to manage credentials with greater ease and security. This shift goes beyond mere policy—it cultivates an environment where robust password security is seamlessly integrated into daily work life.
Review the Full Session Transcript
No time to watch the session? No Problem, Take a read through the transcript.
0:00
Thank you for joining us today here at Perverse Security for our webinar Reimagining Passwords, Defense and Your Culture of Security.
0:08
I'm Carolyn Evans, the Director of Marketing here.
0:11
And today we will have two presenters.
0:16
We will have Brian Crist, who is a sales engineer with our team and our very own CTO, Ian Ray.
0:25
Ian and Brian will be discussing how to foster a dynamic security culture, revolutionizing password practices for better defense and turning users into proactive protectors of their digital access with a focus really on measuring security success.
0:42
AQ and a session will follow, So please feel free to ask questions in the chat there as they come up, and we will take some time to answer them at the end.
0:51
With that, over to you, Brian.
0:55
Carolyn, thanks for the introduction.
0:57
For those of you joining us today, we hope that, well, we're glad you're here and we hope that you find the discussion today thought provoking.
1:06
A little bit of housekeeping.
1:08
We are, if you'll go ahead, Carolyn and go on to the next slide.
1:12
Our goal is to keep this session somewhat engaging and we're going to go right out of the gate and to ask those of you on the line to take a couple of polls.
1:22
So if you'll see here on the screen, we're we'd like to know how confident you are that your employees are following best practices for their passwords.
1:34
We'll give you about 30 seconds.
1:36
Take a sip of coffee, get the brain brain, brain blood to the brain flowing and and answer the question.
1:46
So you should see the poll pop up.
1:48
I think most people have answered.
1:50
We'll give it another second.
1:55
All right, and I will go ahead and end that poll.
1:58
All right, thanks Carolyn.
2:02
Kind of an interesting, interesting set of results.
2:05
They're kind of all over the place.
2:07
That's we we're glad y'all participate in that.
2:10
Thank you.
2:11
So we've also got one other poll here that we're going to throw up on the screen right out of the gate.
2:18
Carolyn, if you'll, if you'll launch that as well.
2:23
And, and the question is, how long does it take you to memorize a new phone number?
2:29
By that I don't mean that you can quickly, you know, look and and and key that number into something you need to truly memorize the number, you know, so that if you were asked, you know, off this off the cuff, you would you would know that number with the advent of smartphones.
2:48
Yeah.
2:53
I'll give it just another few seconds here.
3:03
All right, 321.
3:07
All right.
3:09
Yeah, very good.
3:10
OK, Yeah, thanks again folks for participating in that.
3:13
I hope it hope it give you a little bit of of pause to think about, you know how that how you fare with your memorization skills.
3:23
Carolyn, if you'll move us on to the next slide kind of want to introduce go ahead.
3:30
This is just a placeholder we'll move on to the next one.
3:33
Go ahead and sort of set the set the landscape here with with what's what we see in the security arena.
3:42
So some of this information that you see up here on this on this on the screen comes from a variety of different reports.
3:48
The first one here is this this human element.
3:54
So this, this statistic comes from the Verizon report and essentially what they're saying that in this, this is not just password related, but that human beings for 68% of all incidents, there's they're the 'cause they're, they're the ultimately they're the blame, blameworthy cause for security incidents.
4:16
And then another really interesting statistic that came from, from cyber news is they took a list of of 15 billion passwords and analyzed them.
4:28
Ian, we talked about this a little bit.
4:30
They discovered that 86% of those passwords were not unique.
4:36
What, what do you think about that, Ian?
4:39
Like that's for two human memory.
4:41
We only come up with so many different sets of passwords and then we do kind of the, we often tend to do the bare minimum to get it through the password policies to get it accepted.
4:51
That's where I think that speaks pretty loudly that most people are using the same kind of things like a name with a number counting up and down, you know, put an exclamation point on the end.
5:03
While we are trying to use good passwords, it most of us are not being overly successful at choosing good unique ones.
5:11
We, we all are a lot more similar than we'd like to otherwise admit.
5:14
I think absolutely.
5:16
And in in fact, the, you see that middle statistic there.
5:19
The Verizon report also surfaces the fact that 21% of the passwords are just easily guessed.
5:25
And it's an artifact of, of human nature.
5:27
It's an artifact of the fact that we're not using unique criteria when we compose these passwords.
5:34
If you'll advance this on to the next slide.
5:40
So this is the reality.
5:42
I'm I'm not going to go through all of these stats here.
5:45
They come from some very familiar sources.
5:48
But the punchline is, is that when there is a breach, they tend to be very costly.
5:57
And at the heart of that are these weak and insecure passwords.
6:03
Ian, we were talking about this, you know, statistic here that you've, we've kind of narrowed this down to the higher education space just for this particular slide.
6:14
But the, the principle, you know, largely remains the same, you know, with other verticals on this statistic.
6:21
But Ian, what, what do you think?
6:23
You know, what was the what was the reason that from 2019 to 2020 there was nearly a a doubling of this kind of these kinds of attacks on higher Ed?
6:34
What did that survey say?
6:36
That's where really the we're we're at a bit of an inflection point as people are starting to apply a lot more automation and bot style attacks and now with more modern attacks as well, AI driven attacks.
6:50
And it's just one where the complexity of doing this is dropping off, the cost is dropping off.
6:56
And so as a result, we're faced with more and more of these.
6:59
And so 2019 to 2020 was kind of where some of the, you know, some of the automation was really becoming a lot more applicable at scale.
7:08
And then people were, you know, attacking the weak points, the people who have reused the passwords from some of those past slides, the people who were choosing poor ones that barely made a pass, the password policy and that were easily guessed and can be and be attacked that way.
7:29
And so that that's where we're trying to see that growing there.
7:32
And then it's just continued on for subsequent years as they're just getting more and more sophisticated and, you know, more advanced and cost effective.
7:40
So.
7:41
Yeah, yeah.
7:42
Thanks.
7:45
If you'll go ahead and move us on to the next slide, I kind of want to get folks thinking about why things haven't been working.
7:59
I mean, so we're talking about decades here where we seem to be stuck in this pattern of expecting users to not do bad things.
8:10
And it, it goes back to, I think again, the Verizon report when they talked about the human element wasn't specifically focused on passwords.
8:20
But I, I think that they touch on something in that report, which is this idea that we're asking humans to do things that are sometimes mentally difficult, right?
8:33
To compose complex passwords, to expect them to remember them, to not procrastinate.
8:40
Ian, what's that?
8:41
What's that old saying about repeating history or something that yeah, we have to learn from our history, otherwise we're doomed to repeat it.
8:50
And reliant on human memory is just not something that can be effective.
8:55
I'll personally share my poll results.
8:57
It took me years to learn my wife's phone number, let alone a good new random password.
9:01
It just doesn't jive in my head.
9:04
So I'm one of those where it's just I have to learn from my past history.
9:08
I need something different.
9:10
Yeah, it's funny.
9:11
I was when I was thinking also of that old saying, it says something like insanity is doing the same thing but expecting different results.
9:18
I think all of that applies here, right?
9:20
We, we keep trying to get users to do the right thing, not recognizing that there's a little bit of a, a mental brick wall there.
9:28
If you'll go on to the next slide, we, we actually conducted a survey not too long ago on this very topic about what users are doing to deal with the, the challenges of memorizing passwords.
9:44
I mean, organizations continue to encourage longer passwords, more complex passwords.
9:53
And it's, it's having this sort of detrimental effect on the other side of the equation, which is the users hit that mental wall.
10:01
And then so they do things that are inherently unsafe.
10:04
And and we sort of I just sort of bore itself out in in the survey we conducted.
10:10
Haley, if you want to go on to the next slide there.
10:13
So we want to want to hit you all up with another poll.
10:15
So we want to simply ask, you know, how often are you changing your work related passwords?
10:25
Give that a little bit of thought.
10:35
These are anonymous.
10:35
So honesty is the best, best policy here.
10:47
Give it just a just give it about 10 more seconds for folks to chime in.
11:02
All right, we'll call a wrap.
11:04
Thank you for participating in that survey.
11:07
I surprised that 2 two of the answers didn't didn't get any treatment at all on that.
11:13
So again, good information there.
11:16
Thanks for sharing.
11:18
If if you'll move us on to the so the next I would kind of talk about.
11:24
So we were, we were looking at sort of the, the portrait of the security landscape from a very broad perspective.
11:31
I want to drill down into some specifics at this point.
11:35
1 shocking statistic is that, you know, 80% of businesses are still using the password as their primary security element.
11:45
In fact, it's so funny that just the other day I was reading an article, I think it was penned in 2010, and IBM was, you know, forecasting that within six years, so circa 2016, that you would never need to use a password ever again.
12:02
But that's simply not the reality.
12:05
And Ian, you and I talked about this a little bit.
12:07
I think you had some thoughts on this you wanted to share.
12:10
Yeah.
12:11
Like that's where, you know, as part of businesses, you have to handle such a wide range of different environments.
12:20
And certainly there's the, the, the large common ones where you, you integrate them in with your Federated approaches and things are generally working fairly well.
12:33
You tend to take a bit of a, you know, get try and do your best to get your perimeter secured.
12:39
But then the reality is for most organizations is once you've reached that perimeter, that's when a lot of the time it still results in passwords being used under the covers for for all of those systems behind the scenes.
12:52
And that's when, again, allowing people to, you know, choose those passwords means that often some of the most important systems are actually the ones that are having some of the the weakest governance being put into play on them.
13:07
And that's a real business risk that is being exploited by those by by those groups as they're levered, as they're finding our weak spots and then attacking them.
13:20
And so definitely it's there.
13:24
There's just no silver bullet here right now.
13:26
That is obvious.
13:28
That's for darn sure.
13:29
Yeah, you're absolutely right.
13:30
I mean, folks have tried to kind of pivot away from the password and leverage other factors.
13:38
But as you said, there's no, no silver bullet.
13:40
If you'll move us on to the next slide, Haley, what is really interesting about, you know, this idea that there's really no silver bullet is for the organizations that have tried to move off of the password or, you know, supplement the password with different factors.
13:58
The reality that we found our self in now is that even in those cases, some of the things that folks have pivoted to have become insecure.
14:07
You know, I can remember a time when no one really criticized the one time pen delivered by SMS.
14:15
But as you can see here and this just just a a drop in the bucket.
14:19
I mean, the number of cases of, of, of a crime related to SEM swapping is on the rise.
14:26
And, you know, as we were kind of pulling this content together, I remembered this story about a gal who decided to to use AI for the day to see if she could, you know, deceive, you know, organizations and Co workers into thinking that she was, she was really, you know, working versus, you know, trying this experiment.
14:48
And, and I was shocked to find it.
14:50
So she fooled her bank.
14:52
But there was a more, even more recent case where a journalist cloned his voice and, and thwarted the IVR system, right?
15:00
So not all factors are created equal, right?
15:05
And so some folks have pivoted to these things and then, you know, a year or two later have found them obsolete.
15:11
And So what does that mean?
15:14
That means for a lot of folks, they, they go back to a higher, you know, reliance on, on the password, right, Ian?
15:21
Yep, absolutely.
15:24
And that's right, I think possibly in the next slide if we were to go to it.
15:31
Yeah, let's let's talk about this for a minute.
15:34
So what you saw in that previous slide was some attempts to move into the kind of multi factor authentication space, some of it not working out so well, Ian.
15:44
So multi factor has been under the spotlight a little bit here with an an incident called the snowflake incident.
15:52
Why don't you talk to us about that here on this slide.
15:55
And like that's where a lot of people depend right now heavily on on a failed authentication to give them that like Pins or push notifications or other approaches either relying on that to safeguard their business critical resources.
16:14
The problem though, is sometimes mistakes happen and these don't get activated or sometimes people are attacking the MFA approach and doing it quite effectively.
16:25
And so there's, there's kind of one of those and, and, and again, in both of those attacks and they get access to your critical resources like what happened in Snowflake.
16:33
And then both you start to get compromised, but then also your customers get compromised.
16:38
And it can, you know, be a very negative experience for everybody who's involved.
16:43
And that's a major risk and a lot of people have been kind of going off of that.
16:49
Any MFA is better than no MFA and that's true.
16:53
But also too any password is better than no password.
16:57
That also is true.
16:58
But for both MFA and for passwords, we have to be thinking about how do we get both sides stronger?
17:04
Because you can't just strengthen one and ignore the other side.
17:08
Because again, in in, you need both factors to be strong so that when somebody comes up with a new compromise or a new attack or a new social engineering approach, that that you can rely on that other factor being strong.
17:25
You can't ignore one at the expense of the other.
17:28
And I think that's one of the key things here, snowflake.
17:32
They were kind of ignoring the password strength.
17:35
And so as a result, people were able to guess some very easy ones.
17:39
Some of them were apparently well known for many years and, and, and being actively or were on compromised lists and just people never changed them.
17:48
And so, you know, that's when you're just putting all your pegs in the MFA basket and hoping that it works.
17:53
And if there's any problem there, then you got a really, really big issue resulting from that.
17:59
Yeah, I, I think that, and I hate to say it this way, but I, I feel like the, the idea is just, you know, well, let's light up MFA and then we're done with it, right?
18:09
And it's almost driven by, I've seen this in cybersecurity insurance policies, right?
18:15
It's like, OK, well, I'll check this box, right?
18:19
And, and now I'm secure and I can move on with life.
18:22
And that's just simply not the reality.
18:25
And I think this incident highlights 1, you could have problems with your MFA and then two, as you said, you can't do one without the other really.
18:34
And then this is in the, in the case of Snowflake, that was the case, right?
18:38
There was a password, it was known to be insecure and it was just, it was neglected, right?
18:44
So it, it's MFA is important, but it is, is certainly, again, to use the terminology used earlier.
18:53
It's, it's also not the silver bullet.
18:57
If we could move on to the next slide, you touched on Federated access earlier.
19:08
A lot of organizations have deployed federation.
19:12
We ourselves provide Federated solution, but in dealing with our customers, we know that federation is, is, is somewhat of a, a Unicorn answer to the problem because it's the minute you introduce legacy systems into an organization, you know, that utopia vision sort of just goes out the window.
19:40
You know, what was really interesting as we were kind of thinking about this and, and looking around and seeing at what what was going on in the landscape around us.
19:52
There's a survey conducted and you know, institutions are, are not only not getting rid of mainframes, but they've admitted that they're going to continue to expand their mainframe footprint.
20:07
And you know, I don't know about the last last time you checked, but mainframe was nowhere near being integrated into the, the SSO world, right?
20:17
I mean I think they what what they just recently work around for the 8 character limitation on a password or.
20:25
What what is it is that they've changed, they've made recently passphrases have been around for a while, passphrases.
20:30
That's right.
20:30
It's just that they're still shockingly poorly adopted because again, like it's hard to evolve legacy platforms and legacy business approaches that can be very disruptive.
20:42
So this for two, a lot of people tend to put a lot of that focus around making sure that perimeter is as secure as possible.
20:48
With modern breaches, again, you, you find a weak point and then you navigate through it.
20:54
So again, you just, you can't, you can't just depend on the exterior having good, you know, good approaches.
21:01
You need to make sure that your interior is as as hardened as possible as well.
21:05
And that's I think one of the key takeaways.
21:08
All businesses have these have this infrastructure element that that is necessary.
21:13
And again, like, you know, again, networking gear is another great example of one where there's been a lot of history here and a lot of past attempts and that can be murky and uncertain.
21:22
So again, making sure that you know that the underlying infrastructure is solid, that's the critical, like make sure no password is left behind because that's the one that's probably going to be the one that gets exploited.
21:34
Yeah, I I like that.
21:35
I might borrow that in the future.
21:37
No password left behind.
21:40
If you will move on to the next slide real quick.
21:44
I want to talk to you real quick, Ian, I want to put this in your court here.
21:49
Talk to us about the Secret Zero problem.
21:52
It may be a new term for folks on the line.
21:56
So maybe kind of unpack what it what it is first and then sort of what it betrays.
22:04
And so like Secret Zero problem is really a reflection that people don't trust what others are doing.
22:11
And so you end up wrapping user content like their passwords and other sensitive material with encryption to try and make sure that it's secure.
22:22
And the secret 0 problems is you have to keep going down the layers of your infrastructure until you get to the root layer, which is the 0 secret, that one secret that basically helps secure everything else.
22:37
And you know, in the past, some people might have allowed their people to choose.
22:42
That's zero secret.
22:46
Chances are if you allow them to choose, somebody's going to do 0123456789 as that root secret, which kind of defeats the entire purpose.
22:57
And so, and then as a result, now they've really focused on taking that decision out of people's hands for the, the root 0 passwords or the root 0 encryption keys, making sure that those are auto generated, making sure that they're as strong as possible.
23:12
But again, you're taking those principles at the low level to try and keep things secure, but the actual content that you're securing with it is weak.
23:22
And so as a result, you still have a pretty significant attack space as a result, like you're securing the, the, you're securing the foundation of the house while leaving your upstairs windows open.
23:34
And so, you know, then somebody might be able to climb in through, you know, the the areas that you haven't got to yet.
23:40
So that's where how do we bring some of these best practices, principles, these things that are that that haven't shown to work to help people secure those higher levels in their organization, to make sure that people can't crawl in through the through an upstairs window or through your back door kind of thing that you might have forgotten about here.
24:02
Yeah, thanks.
24:03
Thanks for the explanation, Ian.
24:04
It really does.
24:05
You know, it, it, it, it just simply demonstrates that there's, if you'll go on to the next slide, it it demonstrates that there is sort of this contention between those that are responsible for security.
24:22
Can we move on to the next slide?
24:25
There we go.
24:26
Yeah, there there's this sort of this contention between those who are responsible for security and those who are accountable for creating that password, right?
24:37
And so that's our assertion in a nutshell, is that ultimately accountability rests with the organization.
24:46
When there's a breach, when there's an incident that there's that human element, there's the blameworthy cause, right?
24:56
But then there's the person or the group that's held responsible for that, right?
25:02
And sometimes, a lot of times there's there's a disconnect.
25:08
We actually want to put that up to y'all as a question.
25:12
So on the on the if we'll move on to the next slide.
25:15
We want to get y'all to kind of weigh in here.
25:17
How, how strongly do you think that there's a disconnect between the user's responsibility and the actual accountability in the organization?
25:28
Is there a disconnect?
25:29
And if so, you know, where do you, where do you think that falls on the spectrum?
25:34
So if you'll go ahead and launch that poll for us and we'll give folks about, I don't know, 1520 seconds to weigh in, we'll go five more seconds, 54321.
26:18
OK.
26:19
Thanks again for participating in our poll there.
26:25
We appreciate that good feedback.
26:29
Carolyn, if you'll move us on to the next slide, want to kind of shift and talk about so kind of talked about the reality we find ourselves in both the broad level and, and a little bit more of a granular level with the problems in the security landscape.
26:48
I, I, I know that some of you are probably familiar with a illustration like this, but I want to talk very briefly about the anatomy of an attack or the sequence of an attack.
27:04
While there's no exact cookie cutter, you know, pattern for an attack, they tend to look a lot like this.
27:13
Get some kind of credential.
27:14
We saw that in the Verizon report.
27:15
You know, most breaches start with lost, stolen, breached credentials.
27:21
Deploy some command and control so that you can backdoor yourself in there, do some reconnaissance, try to move laterally, elevate, rinse and repeat until eventually you get sufficiently permissioned set of credentials that allow you to breach the critical systems, exfiltrate and then hold that data hostage for ransom.
27:43
Ian, I want to talk to you about this particular sequence.
27:46
And there's some places along this chain that are are really interesting and and important.
27:54
So talk to us about some of the significant points along this chain.
28:00
For sure.
28:01
Like right now, a lot of people are really focusing on step one around the, you know, the external points where people, you know, are acquiring credentials and then gaining a foothold within an organization.
28:16
And so that's where a lot of the focus is, where people are turning on MFA, where people are trying to bring in other authentication options that are a bit more robust against some of the modern attacks.
28:28
But again, when there's a problem, people are able to breach step one, and then they're able to start moving through and get into stages 3 and four.
28:40
And that's where they can often move laterally through organizations and do reconnaissance.
28:48
Because like a lot of a lot of organizations, when they detect a breach, it might take them months to change all those passwords.
28:59
And in the meantime, how much confidence you have that you have fully eradicated and that people are not moving around and doing further reconnaissance and breaching additional systems.
29:11
It's a long time like say like if they compromise your domain controllers, several months is a long time to tolerate that your passwords might be known.
29:22
And that's where it's, it's a significant risk and one that if you can bring in approaches to rapidly re secure those potentially breach credentials, you can start breaking that loop in steps three and four really rapidly.
29:40
And also when you take a comprehensive view on passwords that no password should be left behind, that you, you understand the controls for all of the accounts that can navigate through step one and get into your organization.
29:53
You can understand where your weak points are, make valid investments to figure out how to improve those also.
30:00
But then also understand that if you do get a compromise, these are the few points that are really going to be painful, that it is going to take a little while to break those loops three and four.
30:09
So, but but it's important for us to map that out, understand that where our weak points are and also to to remove the ones as many as possible as quickly as possible so that, you know, if you are faced with as breach, that you can get most of your organization re secured in, you know, matter of hopefully hours at the absolute most.
30:34
That's what we, I think we all need to be looking towards here is how do you break that loop on three and four as quickly as possible and as comprehensively as possible when you're faced with breach.
30:46
Yeah, absolutely spot on, right.
30:47
The idea would be to sort of short circuit what's happening in sequences 3:00 and 4:00.
30:53
As a side note, you know, we are a privileged vendor and so we've introduced this before and a lot of emphasis has been placed on, on, on Step 5 and rightly so, right, protecting those critical systems with with privileged access controls, password randomization, etcetera.
31:10
And I think those principles are super important.
31:13
And as you'll see here in a bit, we think that they are leverageable beyond just privileged access.
31:20
Carolyn, if you'll move us on to the next slide.
31:25
So we want to kind of shift the conversation to what good habits look like.
31:31
You know, early on and I introduced, I just sort of teased out the cyber news statistic about the 15 billion passwords that they analyzed, how, you know, 86% of those that they analyzed were not unique.
31:49
What also surfaced and it's a really, we don't have time to go through all of the data that that report presented, but it was just absolutely interesting.
32:00
50% of users used 8 characters or less, right?
32:07
So Ian, what's the significance there from a technical perspective?
32:11
I mean, I think the audience already knows it, but but just say it for the sake of saying it like that's for her, you know?
32:17
Took me takes me a year to learn my wife's new phone number and it's only 7 characters long.
32:22
Learning 8 characters is a bit of a challenge for me if it's truly random.
32:27
But then also too, if you are adopting a 1516 character password policy like you really should be, you know?
32:34
I'm only human and I have to accept where some of my weaknesses are going to come in there.
32:40
I'm probably not going to remember it.
32:42
And if I do, what I'm going to do is I'm just going to fall into the predictable case where I'm adding a number on the end and counting up or counting down or changing like, you know, adding an exclamation point or changing the special character.
32:53
Like it's not like I choose good passwords because it's just, it's too hard to remember good ones that that's where I'm, you know, yeah, I have to accept that I'm human on some of these things.
33:06
Yeah.
33:07
There's actually, there's actually a principle, Miller's Law on this, which was kind of a philosophical, you know, assertion that people can only remember 7 pieces of data.
33:23
And like with phone numbers, there may be a way to like logically cluster that and break that down.
33:28
But what we're asking people to do, right is random and long.
33:33
And and that's what does make for a good password, right?
33:36
It has to be lengthy.
33:38
So it's to stave off brute force attacks.
33:40
And it has to be complex again, you know, to make it where they can't be easily guessed or components of it can't be easily guessed.
33:47
What's really interesting about the this that same security is that when it came to these passwords, there were some common, I think to the tune of something like a million of those in involved the the use of the year 2010.
34:05
I won't say what the word was, but I think it was like 2.7 million used a particular curse word as as part of that password.
34:14
So this, what this tells you is that human beings are struggling to make complex passwords and when they hit that limitation, they do bad things.
34:26
They use, you know, predictable components of those passwords that make them them easily.
34:31
Guess so.
34:32
So, but it still doesn't change the right answer.
34:36
The right answer is you still need long passwords and you need complex passwords, you need training.
34:43
So, you know, we, we at the beginning of this presentation, we surfaced some, some internal statistics from a survey that, that we conducted showing that users are still doing bad things.
34:55
And that's despite getting annular, annual or even more frequent training.
35:03
But that doesn't mean that training's not valuable.
35:05
It absolutely is.
35:06
There's a lot of good, you know, cybersecurity principles like, hey, don't pick up that USB stick that you found in the parking lot and plug it into your computer, right?
35:16
I mean, training is still immensely valuable.
35:20
And so as part of a a good, good habit in your organization, you should continue to do that policies and updates.
35:27
Let's talk about that this for a minute.
35:29
You touched on it earlier, Ian, but what's the conundrum right now with with policies?
35:36
If I say today we're gonna go from a 16, you know, character password to a 25 character password.
35:43
Why is that challenging for the organization?
35:46
What would be on the obvious, like when, as we're talking to everybody here, of course, everybody's worried about, you know, their employees wanting to take pitchforks and hunt them down when they're trying to increase the length of these policies.
35:59
Because, again, it creates so much friction and frustration.
36:01
You have so many people going, how am I supposed to remember this?
36:05
You know, again, I'm probably not going to remember it now that we're all working remotely, chances are we're going to be a lot less embarrassed to write the passwords down and sticky notes and put them on our monitors at home kind of thing.
36:16
Like that's where you have this major amount of friction here.
36:19
And so as a result, people are concerned around increasing their like setting their policies in a way that actually reflect the needs of the organization.
36:27
That's where again, kind of who's accountable is really critical in the the topic here because we do need to secure these better yet the people who are making the choices of what to adopt aren't necessarily able to make the right decisions there.
36:46
And so and because these policy changes are hard, most people take a very, very long time updating them to reflect modern threats.
36:54
And so rather than it taking, you know, months, maybe in some time planning related years to deploy a new password policy into and get adoption in there, what would it take so that we could update the password policy and roll out a new set of requirements in the matter of days or at most maybe weeks once people are discussing it here?
37:16
How do we make that easier so that we can have that flexibility to adapt our policies?
37:21
I think that's a really important thing for us to think about here.
37:24
We shouldn't be tolerating months and years to change password policy to reflect modern threats.
37:29
We need to be able to do that quickly and not have pitchforks and torches being taken towards us here as we do this.
37:38
Yeah, I mean, the the pitchforks and the torches, I mean, nobody wants them.
37:43
It's best to get, you know, it's the best to avoid them if you can.
37:46
But it doesn't invalidate what the right answer is though, does it?
37:49
Again, no, it doesn't.
37:51
Yeah, the right answer is that we need to have, we need to be able to run a secure organization and use because again, like we, we have to have both factors being strong.
38:00
We can't tolerate passwords being weak and just depending entirely on MFA approaches, that's not working.
38:07
We need to make sure that both sides are strong.
38:10
That way if an attack is available, we can depend on both sides to protect us.
38:14
Yep, absolutely.
38:17
If you'll move on to the next screen here.
38:20
So, you know, we've, we've talked a a lot about, you know, what's not been working traditionally.
38:26
So, you know, for decades we've been expecting users to do certain things that quite frankly, they're just not capable of, especially with the, you know, the, as we talked about a minute ago, the, the right policy is a long password is a complex password and it's a unique, you know, it's a unique password and people are going to hit, hit a wall there.
38:49
So we want to introduce just a paradigm shift in the way that organizations tackle password management with pass plus before a pass plus.
39:02
And one of the fundamental principles that we believe that a solution, if you're going to do this and you're going to do it right, you have to make it easy on the user, right?
39:11
Like that's the friction point is all of this stuff that we're expecting them to do is difficult, right?
39:18
So give them an experience where they really don't need to think about passwords, where they're securely vaulted.
39:26
If they need them, the hope is that they don't need them, right?
39:30
You know, with advancements with things like Windows Hello and Max Touch ID, right?
39:36
Like getting access to some systems is inherently getting less reliant on the password.
39:41
But as we mentioned already, most organizations have, you know, legacy systems laying around or every once in a while you're going to be prompted for a password.
39:51
And so make it really, really easy for the user to get that password when they need it.
39:57
Ian, anything you want to say about that?
39:59
Did I, did I leave anything out?
40:01
No, like that's where say like if you're to go back to, you know.
40:06
How people are using their phones these days and go back to the telephone number.
40:09
I remember 2 telephone numbers, my parents and my wife's, everyone else I've forgotten.
40:14
I use my phone to store the passwords or the phone numbers.
40:17
I don't remember them because I have an easy way to access them.
40:22
I can embrace that.
40:23
I don't have to have a Rolodex in my head.
40:26
I can just relax and oh somebody gives me a new phone number.
40:31
Cool.
40:31
I put it into where I store them and I don't.
40:34
I give it the name that I can recognize the person's name.
40:36
I don't have to remember that.
40:38
And that's where I think we need to start to embrace the same kind of approach with passwords where it's just we're going to forget them.
40:46
We have to accept that we're human and how do we actually make it a really good experience and how do we simplify it, you know, take out of some of that anxiety.
40:57
So absolutely.
40:58
And to continue that analogy, I'll just make one final comment and we'll move on, which is I use my fingerprint to get into my phone too, so I don't.
41:05
Yeah, good point.
41:08
If you'll take us on to the next slide.
41:10
So that's sort of the end user experience.
41:14
Then you know, the other piece of this is if you're going to make this paradigm shift in how passwords, end user passwords are governed, then you also need to make it easy on those who are faced with the pitchforks.
41:32
If I can say it that way, These are the folks that are gonna get the Flack when things are difficult.
41:37
And so our proposal is very simple take.
41:40
So if you'll think back to the, the illustration we gave about the sequence of an attack and I talked about how do we have traditionally focused on, you know, stop the buck stops on sequence five with privileged access and guarding the keys to the Kingdom still need to keep doing that.
41:56
By no, no means am I diminishing that by if you don't have privileged access, you need privileged access.
42:02
But take those principles and apply them to end user credentials.
42:07
In fact, the you can make the argument that there's a little bit of blurring the lines going on right now where all credentials are privileged credentials.
42:16
And so we would say take the end user credentials and just randomize those.
42:26
Make em strong, make em comply with your your company policy.
42:31
Whether that's 16 characters, whether that's 25 characters or, you know, one day 50 characters, does it really matter?
42:38
Enforce that, you know, so that there is no question as to whether there your, your users have good password hygiene and you want to say anything else about that?
42:48
No, that's for two.
42:48
Once you've forgotten the passwords, it makes it really easy to change them.
42:53
You can change them through automated approaches.
42:55
Just make sure they always put the new password into the place that people can easily gain access to them and they're kept safe.
43:01
And that's where also too, it's freeing from a policy perspective because if your employees don't remember them, they also won't really care when you change them because it doesn't actually affect them day-to-day.
43:14
And so that's where, you know, as we, you know, to improve the user experience, to improve our security, we just have to accept our weakness, but then also embrace that weakness.
43:28
Because if we can solve that through just making sure that the passwords are always available through different form factors, whatever people need them when they need them, then you know, again, we can, we can reduce the pitch force so you can reduce the, the bringing torches and everything.
43:43
And you know, again, and that it's actually improving the security foundations and it doesn't negate the adoption of these other capabilities.
43:52
You still want MFA, you still want biometrics.
43:56
It's just that also now you can have confidence that you haven't gotten that the password can still be used when you adopt these other things.
44:03
Often the password can still be used to log in.
44:06
That's what happened with so like the Snowflake case is that people could still use the password even though they thought they had MFA on.
44:14
And then you have the breach opportunity.
44:16
So again, just, you know, making sure the passwords are good and usable benefits everybody in the organization.
44:24
And that's where you can shift the accountability on to the organization cause the organization ultimately choosing how strong the passwords need to be, taking the employee out of making those accountability related decisions, improving their experience.
44:38
Yeah, absolutely.
44:39
That's, that's spot on.
44:40
If you'll go to the next slide, the, the, the comment you just made Ian about if you move the, if you move the accountability and the responsibility, right.
44:54
So if you move that back into the organization where it belongs.
44:57
So folks that are responsible when a breach happens, if if you're also empowering them to manage and govern those passwords.
45:08
What interestingly, what comes out of that from a technical and a practical perspective is we're talking so far about being proactive, which is randomizing.
45:18
If you think back again to the anatomy of an attack in those sequences, we're talking about, you know, proactively short circuiting, you know, sequences 1/3 and four.
45:29
But also, and I think you even mentioned this, Ian, on the off chance that you think something bad has happened, if you that same technology that's proactively randomizing, you can do effectively an out of band randomization, right?
45:44
So if you're doing it every 30 days, 45 days, 90 days, whatever your policy dictates, but all of a sudden you suspect something, you know, bad has happened, you can click the easy button and you can take care of that with, you know, a portion of your user population or all your users if you need to, and ensure that you haven't left any stone unturned, right.
46:05
So there's there's kind of two facets to this right?
46:08
One is the proactive, but also having the confidence that should something happen, you can also be reactive and very quickly reactive.
46:16
I couldn't agree more because when you have a compromise and everything and you're like, is it really did they really break in?
46:21
How far did they go?
46:24
How far should I go?
46:25
Well, if I try to send off of, if I ask everybody to change their passwords, I'm going to make everybody angry and everything.
46:32
And those kinds of decisions can create the delays that allow for further compromises to occur.
46:39
Whereas if you take that anxiety and that worry out of the equation and to your point, give them that easy button to quickly rotate without disrupting your employees, all of a sudden you can react a lot quicker and with a lot more confidence.
46:53
And to help break that loop as quickly as possible.
46:57
You don't have to have that same level of, you know, circling the wagons and get on all of the leadership on board with these kind of changes here and everything.
47:05
You can, of course, keep them informed, but you can take those steps a lot more proactively when you've removed the friction and the difficulty with all the employees.
47:15
So key opportunity, I think like that's where to just reduce the time to remediation.
47:20
Don't accept months.
47:25
Absolutely.
47:26
And there's, there's one last, you know, kind of artifact on this that, that I'll mention and then we'll move on, which is there's the sort of the proactive, there's the reactive.
47:37
And I, I would say there's, there's sort of a third case that lives somewhere in between, which is, we talked about it when we're talking about good habits, which is enacting password policy and doing it in a timely fashion.
47:48
If I've got these kinds of controls, then the other thing that I can do that is proactive is if, if, if those who are making the decisions about what constitutes a good password make that decision today.
48:04
You know, whatever your password policy is, you're, you're typically gonna have to wait n -, 1, right?
48:10
So if it's 45 days, then I've got to wait 44 days, you know, for users to take care of the problem.
48:18
But if I've pull the whole mechanism back into the organization, into the teams that are responsible for it, I can make that policy decision in a day and I can also effect that change in a day, right?
48:31
So really bringing the control back into the organization just yields a multitude of benefits.
48:37
If you'll move us on to the next slide here really quickly, one of the things that we're talking about from a, a, a tooling perspective is not only, you know, providing folks that again are, are are sitting in the hot seat with the measures to enact these changes to be proactive.
49:04
But if you're doing this, then you need to be able to provide confidence to those who are asking the questions.
49:12
How do you know you're adhering to policy?
49:15
How do you know things are being changed in accordance, you know, with the, the mandates that your organization has?
49:23
And so one of the things that prefer a pass brings to the table is an extensible set of reporting that allows you to ensure those things are going on.
49:34
Ian, I know that the reporting is near and dear to you.
49:37
So I'll give you a chance to, to chime in here.
49:39
We do need to be conscientious of time.
49:41
We've got about 8 minutes left.
49:44
Yeah.
49:44
And so that's for two here.
49:45
One of the things we've been investing in quite a bit over the last six months is analytics that allows to really leverage our system level visibility that we have as part of our automated discovery processes.
49:59
We can really empower people to know these accounts are being managed through your privilege platform.
50:04
These accounts are being managed through your past platform.
50:07
These are the accounts that you might have a problem with that seem to maybe not be governed or maybe you're being forgotten about.
50:15
We allow people to measure those and that way they can also surface areas that might not be too well known also to to measure that and take appropriate steps.
50:25
You know what are the right type of controls, empower people with that knowledge so that then they can reduce the the numbers of these special case.
50:34
You might not be able to eradicate them all.
50:35
Sometimes these things have been around for a very long time.
50:39
But again, measuring them and knowing where they exist is critical to you having that confidence.
50:45
When you can press that re secure button quickly, what other things might you need to do afterwards?
50:50
So again, maybe you can re secure everything in a couple hours.
50:53
I'm trying to make sure it's only within a few days.
50:56
And we have a playbook, they have a plan in case of a compromise.
50:59
Our system level overview really allows you to have that confidence that you can see all of the identities regardless whether their service accounts, shared accounts, team accounts, blah, blah, blah.
51:09
We can see it all and give you that view of what is and isn't being covered right now.
51:14
That's really important.
51:15
Yeah, absolutely.
51:18
Carolyn, if you'll move us on to the next slide.
51:22
I touch on this just briefly.
51:25
I, I think if you can manage to visualize what we're suggesting here, which is removing the burden that comes with expecting users to compose good passwords, to manage passwords in a timely and effective manner and remember those passwords, there's a lot of benefit that comes out of that.
51:51
Number one, you're reducing your help desk call volume.
51:54
Statistically, it is the, as a percentage, it's the largest amount of work that your help desk deals with.
52:01
So if you're not expecting users to remember passwords, then you're in, then you're by nature driving down the cost to, to the help desk if users don't have to remember the passwords, right?
52:15
So there's a productivity element of this, you know, if you forget your password and you can't get logged in or you can't get into that application, then you've got productivity downtime.
52:26
And then of course there's the hard costs associated with, you know, you fail an audit, right?
52:31
In some heavily regulated environments, there are steep penalties, fines, you have your cyber security insurance ramifications, all of that.
52:40
Those hard dollars are associated with, with, with problems in this space.
52:45
So not only are we, we, you know, suggesting that you do things that make your life easier, but we are also suggesting that these kinds of proactive measures can actually, you know, drive ROI advantages and efficiencies.
53:03
Go on to the next slide here.
53:05
Carolyn trying to trying to boogie.
53:07
We've got 5 minutes left exactly for Q&A.
53:11
So we'll we'll take as many as we can.
53:15
So if you've got some questions, if you'll surfaces in the chat and we'll do our best to answer them.
53:22
Awesome.
53:23
Thanks.
53:23
Brian, there was one question that Ian answered in the chat.
53:29
The question was you brought up mainframe.
53:30
Does your solution offer an ease of use connector to take away management of passwords from that legacy environment?
53:37
And Ian, do you want to just reiterate your answer?
53:41
For sure.
53:42
That's where what we can do is provide approaches to help people move from passwords to pass phrases and start to adopt stronger approaches for the mainframes.
53:55
And both of these are available through the Pass Plus strategy where if these are user centric accounts, these can be rotated periodically and made available for people to easily use.
54:05
They don't have to remember these now stronger passphrases.
54:08
We're also to through verb privilege where we can introduce just in time controls where people need to request access to the mainframe and then get access to temporarily the strong passphrase or be automatically connected up.
54:19
So we can support multiple approaches there depending on what's the the best controls that you're that you desire.
54:26
Awesome, thank you.
54:28
We have a couple more questions.
54:30
So there is one.
54:32
Is there a video that shows the end user flow for this?
54:35
I know we don't have videos yet, but Brian, do you want to comment on that?
54:40
Yeah, so we do have a video that's coming.
54:43
What we would like to do, and you can see that here on the screen is to schedule with us an opportunity for us to showcase the solution.
54:52
So I'll walk you through sort of visually what that looks like.
54:57
We make the sort of the password free frictionless experience.
55:02
It's, it's a password manager and it's available on just about every conceivable context you can think of, right?
55:11
So you can access it through the web.
55:14
So all major web browsers are supported.
55:17
There are browser extensions for Firefox, Chrome, Safari, Chromium variants.
55:26
There's a desktop application for Windows, a desktop application for Mac, and then obviously there's, you know, the solution on on iPhone and Android.
55:42
And as an Android user myself, I routinely use the solution and, and, and just simply use my fingerprint to, to get in there to almost parallel what Ian was talking about earlier.
55:53
So we would be happy to, to take you on a tour of the solution.
55:59
Just just book that with us and we'll be glad to do that.
56:03
Fantastic.
56:05
We have one minute left, so I'm going to try to sneak in one more question.
56:10
There might be some resistance to this.
56:12
How would we get around it?
56:16
Ian, do you want, I guess I'll take that.
56:18
I've actually kind of dealt with this already.
56:21
So I won't say who the customer is, but we, we have a customer that is, is going to tackle this problem by introducing it to the security team.
56:34
First.
56:36
The security minded folks that have we've introduced this solution to really like it.
56:43
And so for them it's a no brainer.
56:46
And then once they've adopted it, then the great thing is, is they become internal champions, right?
56:53
So then it becomes this, well, we're all using it and it's working really well.
56:59
You know, we should expand the scope of this.
57:02
So that's the approach that we walk through with with one of our customers who asked this very question.
57:11
And I think it's an absolutely sensible strategy.
57:15
Yeah, I couldn't agree more.
57:16
That's where, again, get the people who live this, who have to deal with these very strong passwords and make them your champions because it's so freeing not having to remember these things.
57:26
I haven't remembered a work password for I don't know how long right now because we're applying these strategies.
57:31
And again, like it's just makes my life easy.
57:33
I don't have to stress over anything like this.
57:36
It's not important to my job anymore.
57:39
Just make it easy, right?
57:43
Awesome.
57:43
OK, Well, thank you everybody for joining us today.
57:46
We are at time.
57:47
And so if you have any other questions, please feel free to shoot us an e-mail, any of the emails that you've received from us, you can just respond and we will make sure it gets to the right person.
57:58
And also, we'd love if you would schedule a solution showcase so that Brian and Ian can get into all of the details that they didn't have time to address here today.
58:07
And we can set that up anytime.
Request a Solution Showcase
Ready to revolutionize your password security? Don't let outdated practices leave your organization vulnerable. Schedule a solution showcase to learn how our innovative approach can transform your employees into proactive defenders of your digital realm and put the power of one-click re-secure in your hands.