Privileged Access Management Solution for Modern Businesses
Learn how an enterprise-class PAM solution can prevent breaches to your company’s most sensitive data and IT systems.
BEST PRACTICES GUIDE
Deploying a Privileged Access System: 9 Actionable Strategies to Ensure Success Download as an eBook
Contents
Read straight through, or jump to the section you want to read
Managing Privileged Access
PAM Research and Methodology
PAM Solution Adoption
Challenges to Securing Privileged Access
Integrating PAM with Third-Party Platforms
PAM Best Practices and Processes
An Unhealthy Reliance on Shared Privileged Accounts
Risks of Standing Privileged Accounts
Managing Privileged Access on Endpoint Devices
Outcomes from Adoption of PAM Solutions
EMA Perspective
Why Your Privileged Access Management Vendor Matters
54%
of organizations have granted privileged access on business
systems to users who are not direct employees of the company
Source: EMA Research Report
The Necessity of Managing Privileged Access
It is an unfortunate fact of IT security that no system is entirely unbreachable. Even the most hardened computing environment enforcing the most comprehensive security protocols must enable human actors to access stored information and perform administrative tasks. At some point, every IT system must be updated, patched, configured, and analyzed. The very existence of these access points inherently brings with it significant vulnerabilities. In the majority of cases, however, the most sensitive system components require elevated privileges to access. Typically (although not always), dedicated IT administrators are specifically authorized and granted enhanced privileges to perform IT management tasks. Similarly, some stored information, such as financial records and company secrets, may only be accessible by high-level business personnel specifically authorized to access such information.
Traditional methods for enabling privileged access evolved from an expansion of common password management practices that have been the hallmark of security since the earliest days of computing. Unfortunately, techniques such as enforcingtheuseofstrongpassword strings (i.e., using a complex mix of alphabetic, numeric, and special characters) and requiring periodic password resets have proven to be woefully ineffective on their own. Such approaches failed to address the fact that human brains are not equipped to memorize numerous complex strings that are constantly changing, and most users will bypass privileged access management best practices by using the same privileged password for multiple accounts or sharing privileged passwords with their peers. Additionally, hackers and other bad actors have become rather adept at finding ways to bypass traditional password-based controls, such as by utilizing cracking software, engaging in phishing attacks, employing keyloggers and spyware, or performing brute-force attacks.
While the use of poor user authentication processes will create significant vulnerabilities with typical user accounts, they are catastrophic when employed with privileged accounts. By their very nature, privileged accounts are completely unrestricted, so anyone able to gain access to a privileged account can perform any task and open any file. In many cases, privileged access granted to one system may enable the performance of privileged tasks on another system, so breaches could spread throughout the business IT environment.
t should also be noted that the dangers of employing weak privileged access management security for protecting privileged accounts is not just limited to preventing attacks from malicious attackers. Employees who have been granted privileged access may also misuse their authorization to perform tasks that could disrupt business operations. For instance, they may change operating system parameters, install software, or otherwise make unapproved changes to key system components that could crash or decrease the performance of applications and servers. Additionally, privileged users may intentionally or inadvertently delete critical data or share sensitive files with unauthorized individuals. Since traditional methods for managing privileged accounts do not record activities, privileged users are not held accountable for their actions.
Best practices supporting privileged access management (PAM) were developed to ensure the responsible delegation and governance over privileged accounts and services. Key components of a PAM strategy include:
- Identification of privileged access users and accounts
- Authorization and approval processes for granting privileged access
- Restriction of activities that can be performed with privileged access
- Limitation of duration of privileged access
- Recording, alarming, and auditing of privileged access use
While most organizations recognize the importance and value of adopting PAM best practices, adopted approaches vary widely. Certainly, PAM requirements are dependent on business use cases. Organizations managing more sensitive data and more stringent compliance attainment goals will need more effective methods for monitoring and controlling privileged access. However, even in less security-conscious environments, a lack of effective PAM controls can be disastrous to business operations. Finding the right balance of adopted privileged access management solutions necessitates an understanding of the different processes and technologies, how effective they are at meeting security goals, and the impact they will have on business productivity.
Back to top
Did you know?
On average, roughly 19% of business users (non-administrators) have been granted privileged access to enterprise data, apps, and servers
PAM Research and Methodology
To assist organizations with making strategic decisions on the PAM approaches and privileged access management platforms that will most effectively ensure the security of their most sensitive accounts and IT resources, Enterprise Management Associates (EMA) conducted primary research evaluating real-world enterprise experiences on the requirements, challenges, and management techniques employed for securing privileged access. The intent was to evaluate outcomes and experiences between the different approaches in order to quantify which provide the greatest value in reducing risks and improving management efficiencies in today’s demanding and dynamic IT environments.
For the research, EMA surveyed 160 IT professionals knowledgeable about PAM practices and how they are employed in their organization. All respondents were located in North America and distributed across a wide range of industry types and sizes to enable visibility into requirements and experiences by market segment. All respondents were carefully vetted to ensure they were knowledgeable about the topic and use of IAM solutions in their organizations. Eighty-four percent of respondents were from IT departments, of which 76% held a senior-level position, including IT manager, IT director, IT security director, CISO, CTO, or CIO. Full demographics of survey respondents can be found in the Appendix of this document.
Business Usage of Privileged Access
Enterprise requirements for monitoring and securing privileged access to business IT resources vary greatly depending on individual organizational goals and supported environments. The identification of optimal PAM practices relies on understanding key business requirements so adopted solutions can be aligned appropriately. Even across businesses recognizing a near-identical set of requirements, the priority of introducing specific PAM capabilities will radically differ depending on the emphasis each organization places on specific goals. For instance, some businesses may target solutions that are specifically designed to reduce management efforts over those that provider greater security improvements or increased cost-effectiveness.
In any identification of an appropriate PAM solution to adopt, an initial determination should be made on the scope of IT support the approach will require. At a basic level, this can be determined by identifying the number of users that will be managed by an adopted solution. It can generally be presumed that all IT administrators will be authorized with privileged access. After all, how else can they be expected to perform their primary job function? While this represents a relatively small portion of a typical business’s workforce, the scale of privileged access usage substantially increases when including non-administrators who are not directly responsible for managing IT systems. According to EMA survey results, on average, 18.67% of regular users have been granted privileged access to business servers, applications, and data. To be clear, this just includes support for enterprise hosting environments and does not including users who have been granted privileged access to endpoint devices, such as personal PCs (a topic covered later in this document). Among survey respondents, 98% indicated that at least some non-administrators were granted privileged access to business systems in their organization. Roughly one third of respondents indicated privilege access was granted to greater than 25% of their workforce.
The percentage of business users granted privileged access remains relatively consistent across business sizes (Figure 1). This indicates particularly worrisome conditions for large enterprises. For instance, a large business with 10,000 employees is likely to have granted, on average, almost 1,800 users with privileged access. Clearly, the greater the use of privileged access, the more likely organizations will face incidents of abuse and misuse and the more challenging the environment will be to monitor and secure.
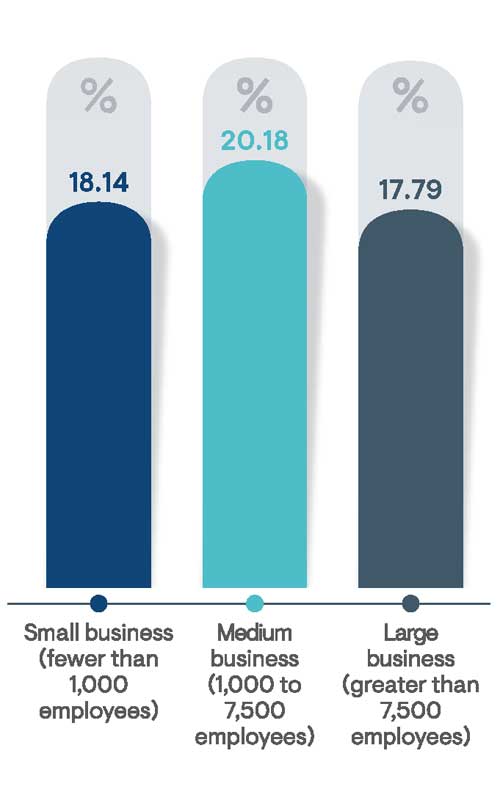
Figure 1: Average percentage of users (i.e., non-administrators) in respondent’s organization who have been granted privileged access to business servers, applications, and data by organization size
The types of supported users granted privileged access will also impact the security requirements of an organization (Figure 2). Unsurprisingly, IT administrators were noted as the most likely users of privileged accounts. However, in about one-third of cases, IT administration was reported to be performed exclusively by or in conjunction with external managed service providers (MSP). Database administrators (DBAs) were noted as the non-systems-administrator business role most likely to have been granted privileged access. Typically, DBAs require privileges in order to configure system parameters in order to optimize database performance and perform other routine tasks, such as backups, updates, and storage management. Similarly, software developers often require privileged access to change system settings in order to resolve conflicts and performance issues with the applications they are developing.
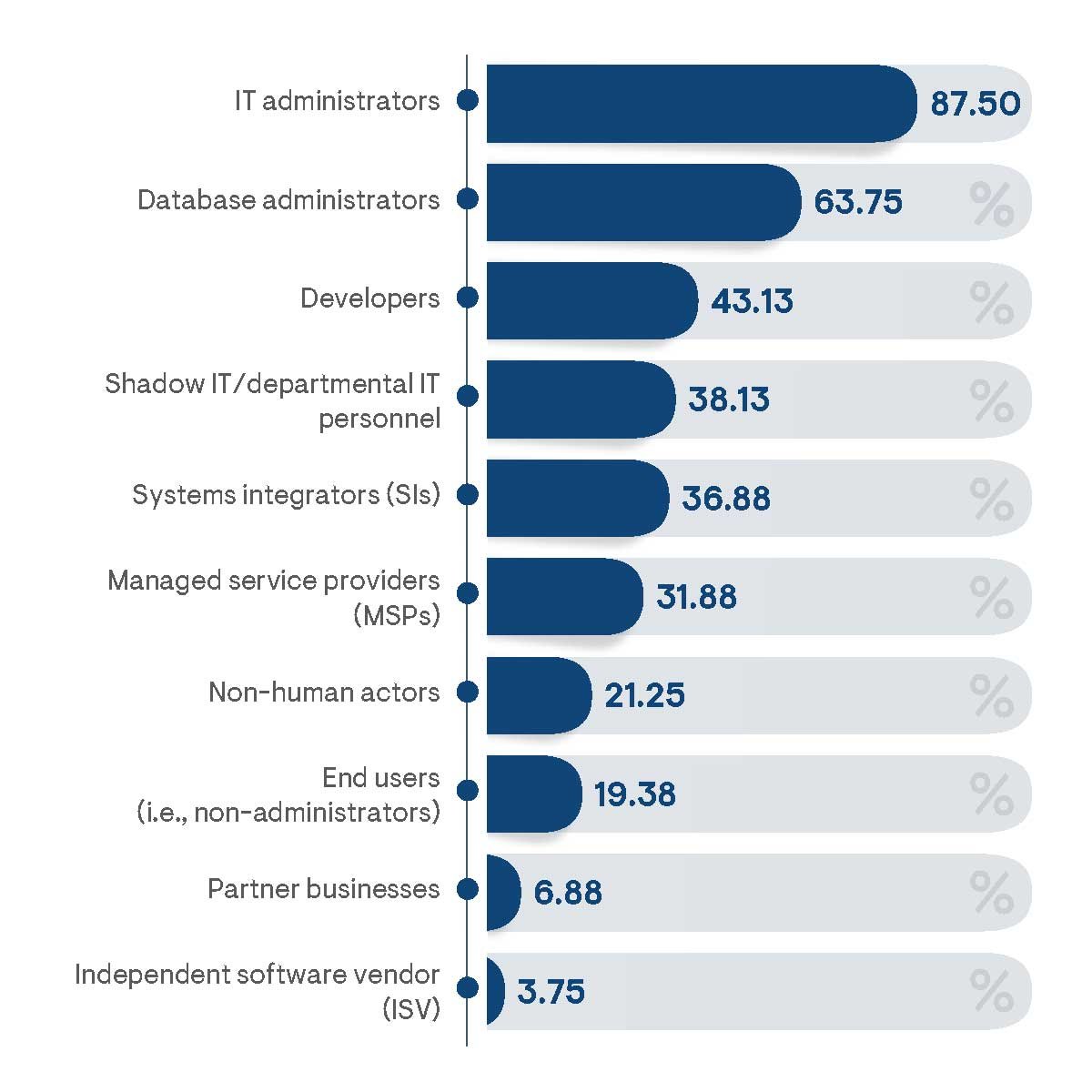
Figure 2: Percentage of survey respondents indicating the types of users granted privileged access in their organization
In total, 54% of surveyed respondents indicated their organization has granted business system privileged access to users who are not direct employees of the company, including MSPs, systems integrators (SIs), independent software vendors (ISVs), and business partners. Healthcare institutions were most frequently noted as granting privileged access to non-employees, as recognized by 94% of respondents from that industry vertical. Non-employees are more difficult to hold accountable for actions performed and may make it more difficult for organizations to achieve proof of policy compliance. This challenge is only exasperated by the admission of 38% of respondents who are aware that “shadow IT” systems deployed in their environment have been granted privileged access. Shadow IT refers to applications, cloud services, or other externally created technologies that are introduced to work around IT limitations. Of course, this is only an indication of known privileged shadow IT occurrences, and the true percentage is likely much higher because many organizations are completely unaware that these even exist in their environments (hence, the “shadow” designation). The use of shadow IT was most frequently indicated by responders from the finance and manufacturing industries (53% and 48%, respectively).
The percentage of users granted privileged access is, again, fairly consistent across business sizes, with only a few easily accountable exceptions. DBAs are almost twice as likely to be granted privileged access in large businesses as in small businesses (71% to 42%, respectively), which is consistent with the distribution of database deployments. MSPs are somewhat more frequently empowered with privileged access in small businesses than with large businesses (40% to 30%, respectively), exemplifying the increased reliance on managed services by smaller businesses. The granting of privileged access to non-human actors—including applications, IT services, and IoT devices—was almost nonexistent in small businesses but indicated to be in use by 34% of large businesses.
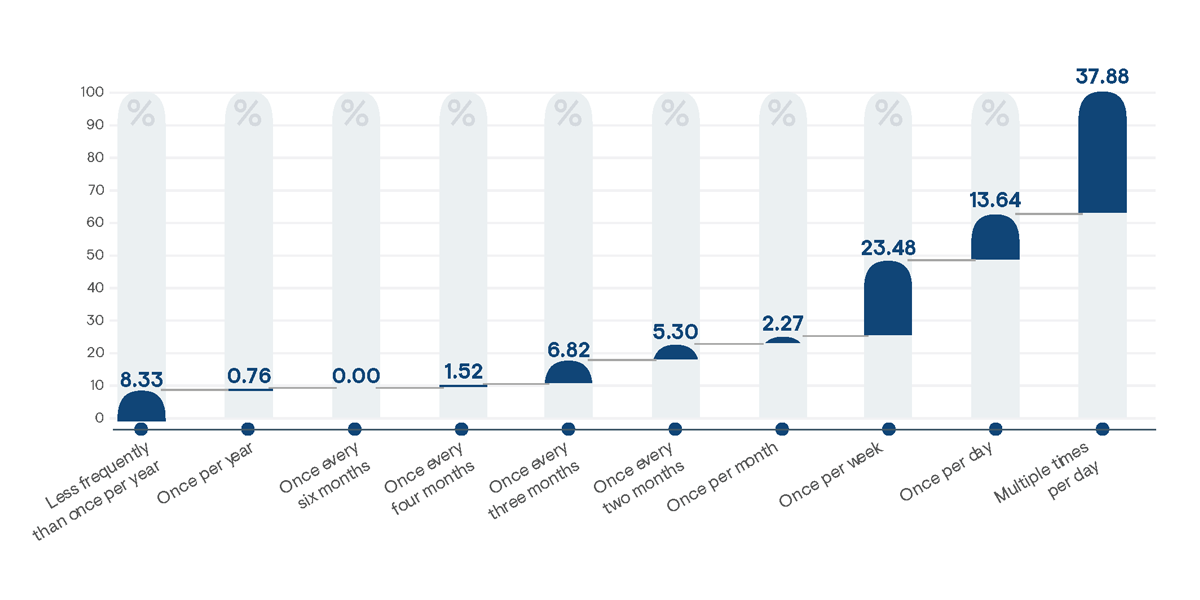
Figure 3: Percentage of respondents indicating how frequently the average user (i.e., non-administrator) in their organization who has been granted privileged access actively uses their elevated privileges.
While it can be expected that IT administrators will utilize their elevated privileges fairly regularly as part of their primary job function, usage by non-administrators varies greatly between businesses (Figure 3). Across all users in all organizations, an authorized non-administrator can be expected to employ privileged access 280 times each year. More than one-third of all non-administrators utilize their privileged access multiple times per day, and 25% employ their privileged access only once per month or less frequently. An argument can easily be made that users who do not require privileged access less than once per month should not be granted privileges at all because they can easily request that privileged activities be performed by IT administrators without significant disruption to business productivity.
For many organizations, the scope of PAM is not limited to the number of supported users and frequency of use, but also includes the diversity of managed resources. While almost 77% of total respondents indicated their organization manages privileged access to on-premises servers, nearly the same amount noted support for cloud-hosted servers (Figure 4). Among small businesses (with less than 1,000 employees), PAM processes were reported to be employed more frequently to support cloud-hosted servers than on-premises servers (86% and 74% of respondents, respectively). This is emblematic of the somewhat increased reliance on cloud services by small businesses in comparison to medium and large businesses. A broader emphasis for support of cloud services was particularly noted for respondents from healthcare, high technology, and professional services industries. Healthcare respondents, in particular, indicated a significant gap, with only 38% reporting support for on-premises servers and 81% noting requirements to support cloud-hosted servers.
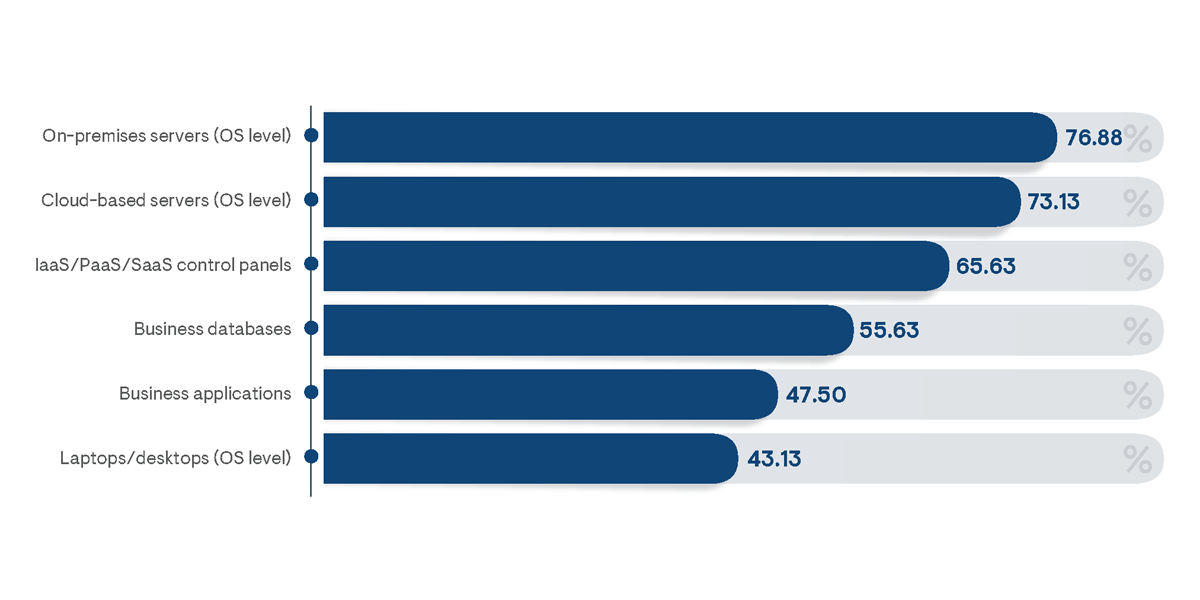
Survey respondents indicated a greater likelihood of controlling privileged access to overall operating system environments than more granularly to individual business applications. This indicates a significant level of PAM immaturity among the majority of organizations with requirements for supporting privileged access. Financial institutions were the businesses indicated to be most likely to support individual business applications (as noted by 86% or respondents from that demographic), while high technology businesses were identified as the least likely, with only 20% currently noting support.
PAM platforms are principally being introduced to support server environments rather than end-user workstations, as indicated by the relatively low (43%) of respondents who noted PAM support was extended to endpoints. In the majority of organizations, endpoint device administrator accounts and end-user privileges are either maintained by the users themselves or set using basic operating system or domain control settings. Respondents from healthcare and manufacturing institutions were the least likely to note PAM support for endpoints (25% and 28% of respondents, respectively), while professional services businesses were indicated to provide the broadest endpoint device support, as noted by 70% of related respondents.
Back to top
80%
of organizations discovered that a privileged access policy
violation had occurred within the preceding 12 months
Source: EMA Research Report
Privileged Access Management Solution Adoption
Given the broad and expanding requirements for controlling privileged access, it is not surprising that most organizations have developed long-term goals for PAM enablement. On average, survey respondents reported they were halfway through their planned rollout of PAM capabilities, with larger businesses indicated to be somewhat further along in their plans than smaller businesses (Figure 5). Financial institutions were noted to be the furthest along on their PAM journey (59% of the way, on average), while professional services were reported as the most lagging (38% of the way, on average). Only about 5% of total respondents indicated they had achieved their PAM goals and only 2% conveyed that they have not yet begun to address their PAM adoption plans.
Most enterprise PAM goals incorporate the establishment of related policies, the introduction of process improvements, and the employment of automated monitoring and management tools. The types of managed tools utilized to achieve PAM goals provide a primary indicator of the level of PAM maturity achieved by an organization. In total, 76% of survey respondents indicated their organization employs more than one technology for managing privileged access. The majority of survey respondents (about 66%) noted they had adopted a commercially available solution specifically designed for managing privileged access (Figure 6). Other popular approaches include leveraging directory services (such as Active Directory or LDAP), utilizing features of a general identity and access management (IAM) tool, or controlling access at the network level with network access control (NAC) platforms, network segmentation technologies, or other network management tools. It is encouraging to see a decreasing reliance on low-maturity PAM approaches, such as shared spreadsheets, inexpensive personal vaulting products, and user account authorizations native to operating systems.
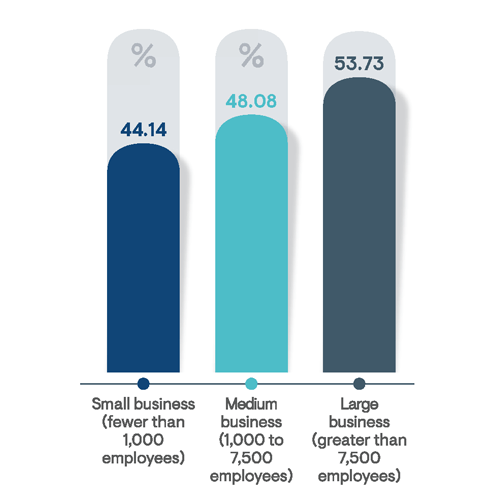
Figure 5: Average percentage of planned PAM capabilities survey respondent organizations have already rolled out in their organization, segmented by business size
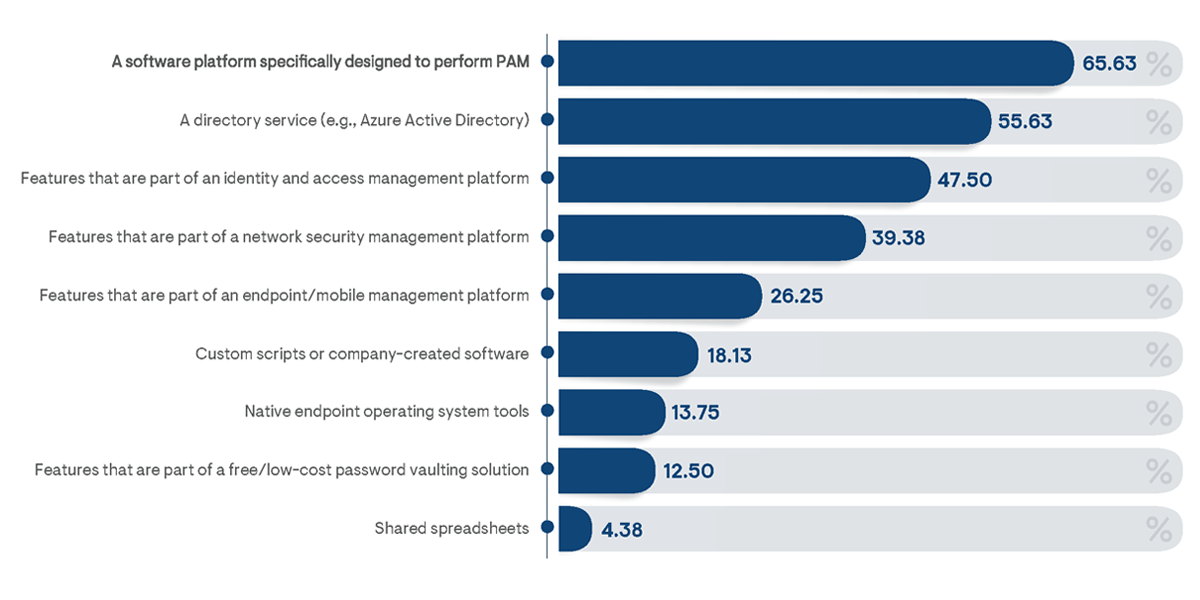
Figure 6: Percentage of respondents from organizations that currently utilize a platform specifically designed to manage privileged access indicating the primary reasons for adopting the solution
The adoption of software platforms specifically designed to manage privileged access were noted by 82% of responders from medium-sized business (with between 1,000 and 7,500 employees) and 67% of large business. Only 37% of small businesses noted adoption of PAM-specific management solutions, indicating larger organizations are more likely to prioritize PAM solution deployments. The principle method employed by small businesses (according to 60% of respondents) is to utilize features of an IAM product. While typical IAM platforms lack the enhanced capabilities of a PAM platform, basic features can be leveraged to control access to standing accounts that have been granted privileged access.
Among organizations that have adopted a PAM-specific platform, the primary reason for introducing the solution was noted as a need to protect sensitive business data (Figure 7). This is no surprise since data protection is the principal reason most organizations introduce security practices in the first place. Beyond this, however, the most frequently noted reasons for adoption focus on increasing visibility into privileged access states. Specifically, monitoring privileged user activity, identifying users with privileged access, and ensuring accountability on the execution of privileged tasks were each noted as key motivators by about one-third of PAM platform adopters. Holistic visibility is essential for enabling access governance and achieving regulatory compliance, but this is very difficult to enable using basic scripts and API-based integrations to collect the information from third-party security and monitoring platforms.
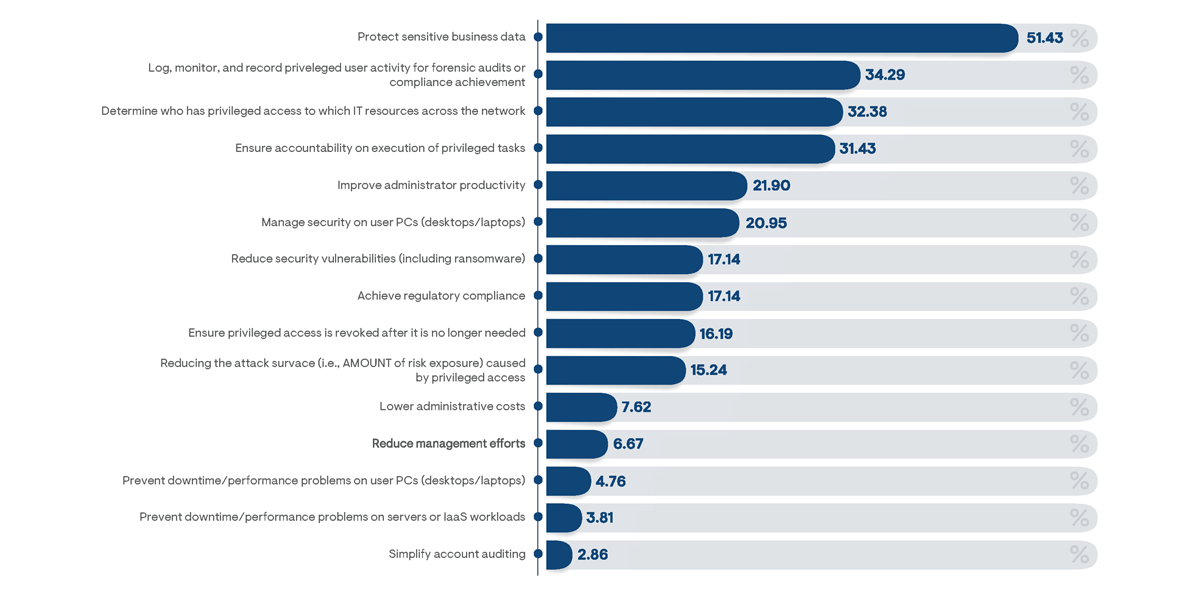
Figure 7: Percentage of respondents from organizations that currently utilize a platform specifically designed to manage privileged access indicating the primary reasons for adopting the solution
Interestingly, 62% of respondents from small businesses (with less than 1,000 employees) that had adopted a PAM-specific platform noted the reason was to improve administrator productivity. By comparison, only 11% of large businesses (with greater than 7,500 employees) noted administrator productivity improvements as an adoption motivator. Small businesses typically maintain diminished IT support organizations but are required to achieve the same level of security and compliance achievement as their larger competitors. As a result, IT administrators in small businesses often “wear many hats,” performing a wide range of IT management tasks rather than specializing in particular areas. By improving administrator productivity, small businesses more effectively achieve organizational requirements without overburdening support staff.
More generally, the features most valued in any PAM solution are those that provide real-time controls over management processes. Among all survey respondents, the most frequently valued capability is providing granular privileged access controls to specific IT resources (Figure 8). This result is indicative of the increasing business transitions away from a reliance on open privileged accounts—which have unfettered access to all IT applications, data, and servers—toward targeted and policy-based privileged access authorizations. Similarly, the use of multi-factor authentication to ensure proper user identification for privileged accounts is highly regarded, as is the detection and alarming of unusual activities. Together, these top three feature preferences indicate increasing requirements for adopting active privileged management processes. While this is certainly an improvement over traditional reactive privileged access controls (which identify and resolve problems only after they have occurred), they fall short of enabling proactive PAM capabilities. Proactive PAM features—including the revoking of unauthorized privileges, the continuous discovery of privileged users, the elimination of standing privileged accounts, and time limitations on privileged account usage—were less likely to be noted as a valued PAM solution feature.
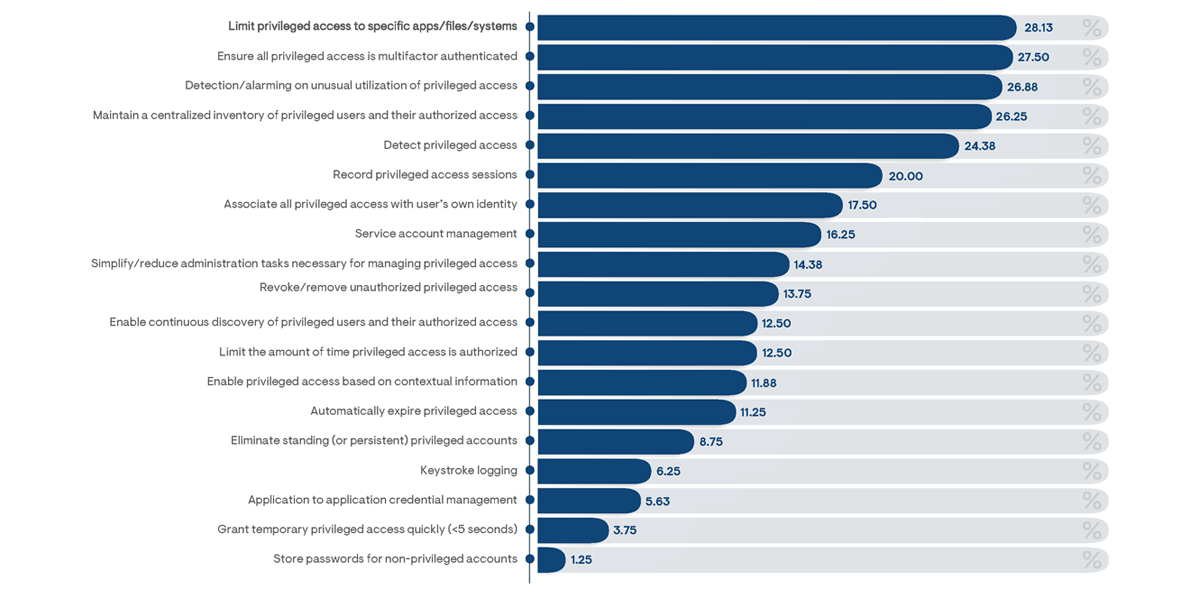
Figure 8: Percentage of respondents indicating what they consider to be the most important capabilities to be included with any enterprise PAM solution
The ability to maintain a centralized inventory of privileged users and their authorized access was broadly recognized as a priority PAM feature by small and medium-sized businesses (by 29% and 42% of related respondents, respectively). However, only 13% of large businesses indicated this to be a key PAM capability. Since this is an important capability for achieving privileged access requirements for regulatory compliance, it seems likely that large businesses have already introduced alternative solutions for recording this information. Conversely, the use of MFA on privileged access was recognized twice as frequently as an important capability by large business responders than it was by small business responders (39% to 17%, respectively), indicating this to be a capability more likely in need by large businesses today.
The ability to manage service accounts was almost exclusively noted as a key PAM feature by 30% of large business responders, with no small business responders and only 9% of medium business responders indicating the capability as valued. Service accounts are typically used in operating systems to run specific applications or programs. They are often never changed from default settings and operate independently of tradition authentication processes.
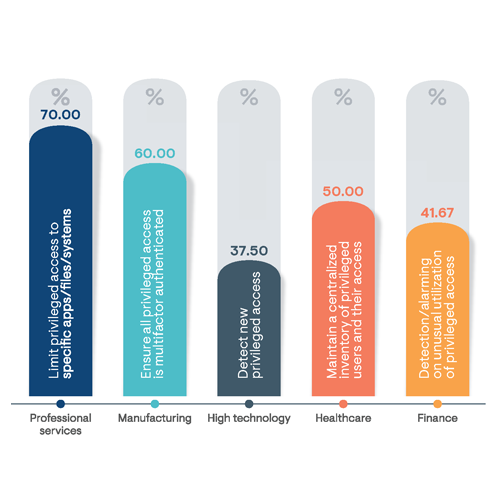
Figure 9: Percentage of respondents indicating what they consider to be the most important capabilities to be included with any enterprise PAM solution
Back to top
Did you know?
One out of five businesses that suffered a policy breach experience serious impacts to overall business performance, including a direct loss of revenue, a loss of customers, and/or damage to the company’s reputation
Source: EMA Research Report
Challenges to Securing Privileged Access
Unfortunately, currently adopted security practices and solutions are, in general, insufficient to fully secure privileged access use. Based on the survey results, 80% of organizations are indicated to have experienced a privileged access policy violation within the previous year (Figure 10), and these numbers only reflect known policy breaches. The true results are likely somewhat higher, since many organizations lack the monitoring tools necessary to identify all violations. Among respondents who were able to detect breach events, the most frequently noted was the discovery of active privileged accounts for former employees or contractors. It is often the case that IT administrators are unaware of all the privileged accounts to which users were granted at the time of their termination. These unrecognized accounts may remain available and active indefinitely, making them prime targets for bad actors seeking clandestine methods for attaining privileged credentials. These types of breaches were more broadly noted by respondents from large businesses (37%) than small businesses (25%), likely due to the higher density of employee turnover rates apparent in larger organization sizes. More than half (55%) of all respondents from organizations utilizing a free or low-cost password vault as their primary method of controlling privileged access reported incidents of discovered privileged accounts for former users in the last year, indicating it to be the least effective method for enabling privileged account visibility.
Among 23% of survey respondents, incidents of users employing the same password for multiple privileged accounts were also detected over the preceding year. In these instances, an attacker who has managed to attain a password (such as by brute force, phishing, or cracking tools attacks) on one business system would be able to utilize it to gain access to additional business systems. Related incidents were most frequently noted among respondents from financial institutions (36%). They were also most significantly reported by organizations relying on native endpoint operating system tools for securing privileged accounts, clearly because these offer the least effective password controls.
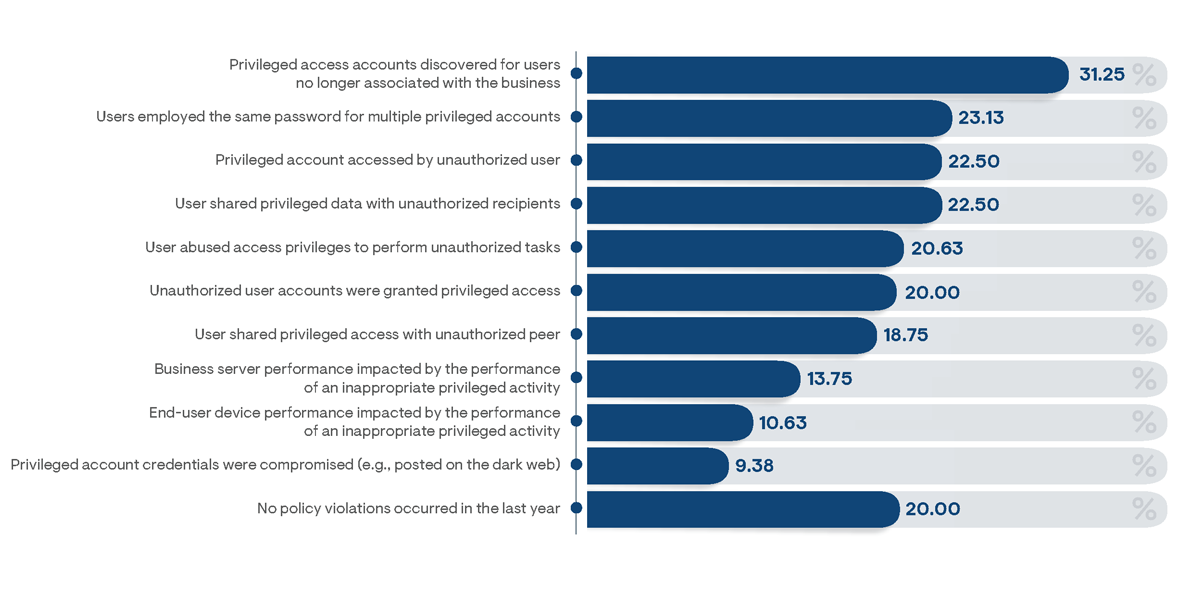
Figure 10: Percentage of respondents indicating privileged access policy violations that had occurred in their organization over the preceding year
The clearest violation of privileged access policies—a privileged account accessed by an authorized user—was discovered to have occurred by more than 22% of respondents. Related incidents were twice as likely to have occurred in large businesses as in small businesses (31% to 14% of respondents, respectively). High incident rates for this breach were particularly noted by respondents from finance (44%) and healthcare (38%) industries. Organizations using free or low-cost password vaulting solutions and those relying on simple shared spreadsheets to manage privileged access were most likely to have experienced an unauthorized privileged account usage, as reported by about 30% of respondents from each demographic. Interestingly, more than half of organizations that grant privileged access to non-administrators reported an unauthorized use of privileged accounts, indicating end users are more likely to employ poor security practices and are not sufficiently being governed in the majority of businesses.
The high incident rate of breach events has not gone unnoticed by IT and security managers, as 93% of survey respondents noted that they do not have confidence that their adopted solution will prevent all privileged access security breaches. Higher levels of confidence were indicated to be achieved from the use of solutions that actively monitor and manage access controls, including IAM, network management, and PAM-dedicated platforms (Figure 11). By contrast, organizations leveraging basic tools—including shared spreadsheets, endpoint management platforms, and in-house-created scripts—achieved significantly lower levels of security confidence in their adopted privileged access solutions.
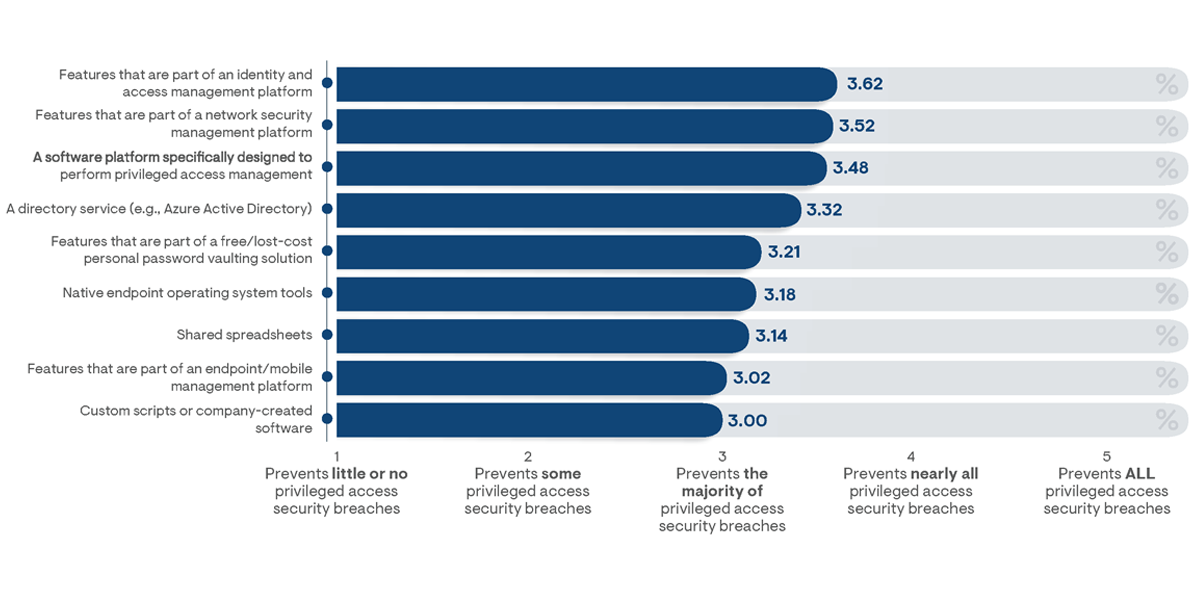
Figure 11: The average level of confidence indicated by survey respondents on the ability of their adopted tools to prevent privileged access security breaches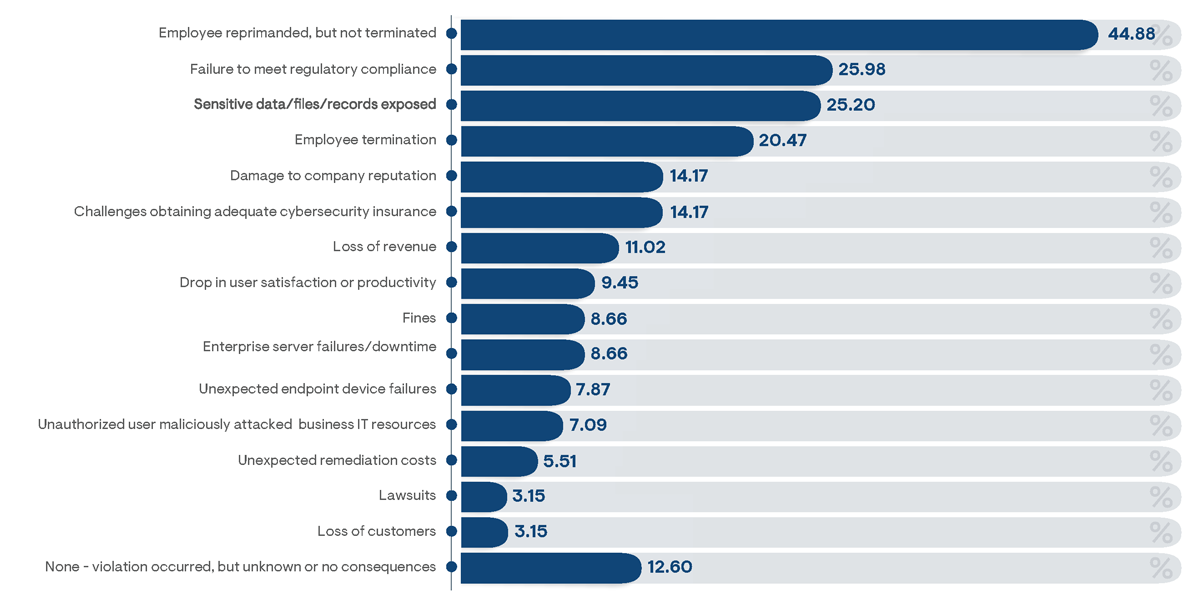
Figure 12: Percentage of survey respondents indicating consequences that directly occurred due to a violation of their organization’s privileged access management policies
Organizations that experienced privileged access policy violations overwhelmingly indicated to have suffered direct business consequences related to the breach. In total, about 87% of survey respondents from breached organizations reported specific impact to business operations (Figure 12). The most frequently noted (and also least impactful) were
incidents of employee reprimands. However, one in five respondents reported that an employee was terminated as a consequence of a privileged access breach event. Clearly, users share the responsibility for securing access to their authorized privileged access with their business and are held equally liable for any consequences resulting from the misuse of their elevated access.
Among consequences incurred on business operations, a failure to meet regulatory compliance and an exposure of sensitive business IT information were most frequently noted by survey responders. The two challenges are inextricably tied because the latter will undoubtedly result in the former. Roughly one out of every five business that suffered a policy breach were indicated to have experienced serious impacts to overall business performance, including a direct loss of revenue, a loss of customers, and/ or damage to the company’s reputation. While only noted by 14% of affected survey respondents, the sudden inability to obtain cybersecurity insurance due to a breach event is a relatively new consequence that is beginning to increase in prominence.
The high frequency rate of privileged access policy violations and their consequences can be broadly attributed to ineffective or poorly deployed PAM solutions. The inhibitors to adopting more effective methods for governing privileged access are principally related to dealing with increasing IT management complexities. In particular, 57% of survey respondents indicated that ensuring their adopted PAM solution integrates with third-party platforms is moderately or very difficult to achieve (Figure 13). Many commercially available cloud and enterprise-hosted software products include their own access processes that are designed to operate independently. Getting these to work seamlessly with a centralized PAM solution often requires the development of integration points using available APIs or SDKs, which need to be maintained and are typically not fully supported by either solution provider. Integrations were determined to be the most difficult for organizations utilizing custom scripts or shared spreadsheets for managing privileged access and were the easiest to enable by businesses that had adopted a PAM-specific platform.
More than half of survey respondents similarly noted the deployment processes for enterprise-hosted PAM software to be moderately or very difficult. This includes the purchase and installation of complex infrastructure components, such as servers, networks, databases, and security controls. Not surprisingly, small businesses were particularly challenged with deploying on-premises PAM solutions, with 86% of related respondents indicating it to be moderately or very difficult. Cloud-hosted PAM solutions, which include resources prebuilt with the service, were indicated to be significantly easier to deploy than enterprise-hosted solutions.
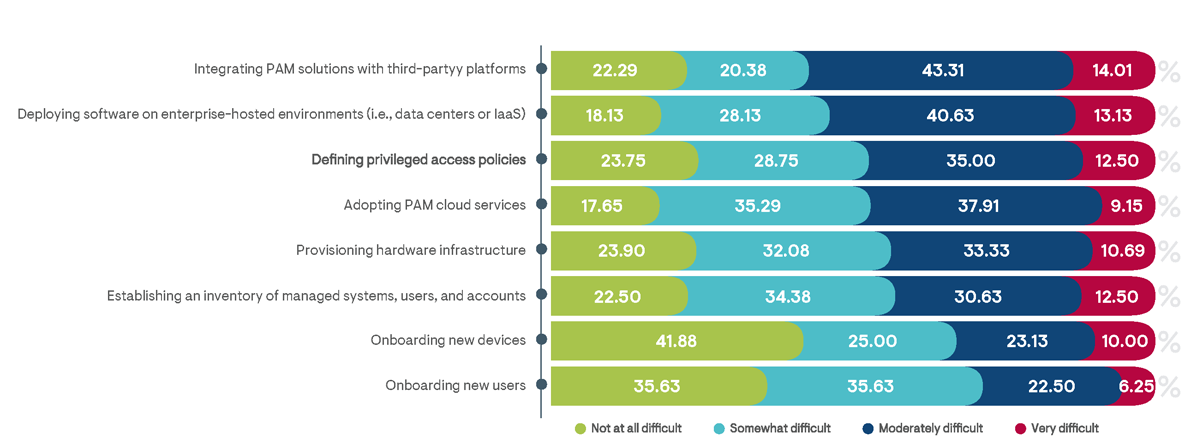
Figure 13: Percentage of survey respondents indicating the level of difficulty experienced with deployment processes for their organization’s current PAM solution
Processes for onboarding new users and devices were noted to be relatively easy to perform by the majority of survey respondents. The one notable exception to this, however, is with organizations utilizing shared spreadsheets for the management of privileged access because they were indicated to have substantial challenges with onboarding new devices, with 57% indicating it to be moderately or very difficult. Tracking privileged access with a spreadsheet requires constant manual updates that can be taxing for administrators required to complete other critical IT management tasks.
Overall, day-to-day PAM management activities were determined to be less impactful than initial deployment tasks. According to survey respondents, themost challenging administration tasks involve ensuring users consistently utilized strong and uncompromised passwords (Figure 14). This includes audits for identifying weak passwords (such as by testing password tables with cracking software) and the identification of compromised passwords that have been posted on the dark web. Difficulties with ensuring password security were particularly noted by organizations supporting PAM with a low-cost password vaulting solution or shared spreadsheets.
Equivalent challenges were also indicated, with attempts to identify privileged accounts across all supported IT services. Most of today’s complex IT environments host IT services across a variety of enterprise server, cloud-hosted, and endpoint resources, and each may maintain its own unique privileged access accounts and administration processes. Centrally identifying which users have privileged access to which resources can be extremely time-consuming without a centralized platform automatically and continuously monitoring privileged accounts and authorizations. Indeed, 46% of organizations that adopted a PAM-specific platform reported they did not consider this to be a challenge at all, indicating this approach to be the most efficient at enabling privileged account visibility.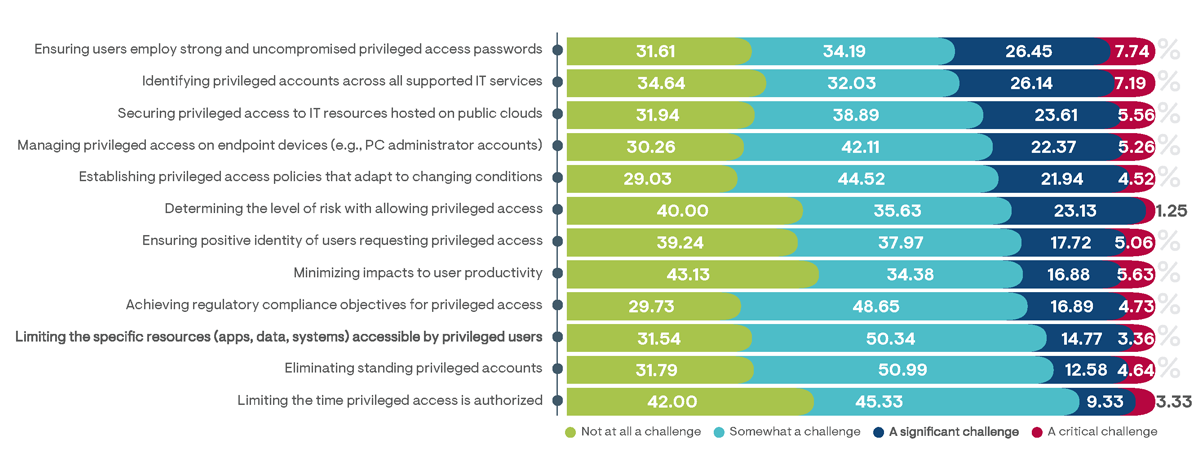
Figure 14: Percentage of survey respondents indicating the level of difficulty experienced with deployment processes for their organization’s current PAM solution
87%
of businesses that experienced a policy violation in the preceding 12 months
reported significant impacts to business operations as a consequence
Source: EMA Research Report
Integrating PAM with Third-Party Platforms
With integration challenges identified as the most difficult element of a PAM solution deployment, it stands to reason that the breadth of integration support directly enabled in a PAM platform can substantially increase its time to value and overall effectiveness. Integrations with third- party IT management solutions can help enable holistic security visibility and contextual awareness of risks associated with privileged access events. Among organizations that have adopted third-party IT management toolsets, the most frequently noted enabled integration is with directory services, such as Active Directory or LDAP (Figure 15). Directory services enable a common data repository that can be used for storing information on users, devices, and shared secrets (e.g., passwords). Enabling integration between PAM solutions and a directory service helps ensure records remain consistent across management solutions and eliminates the duplication of efforts in recording common information. Among survey respondents, 51% indicated that integration with directory services was an essential feature of a PAM solution for their organization.
Integrations are also commonly established between PAM solutions and security platforms. Security information and event management systems (SIEMs) help enable the rapid identification of any misuse of access privileges, as well as determining overall levels of risk posed to enterprise systems. Additionally, integration with identity and access management (IAM) solutions used to authorize and authenticate non-privileged user access can help reduce management efforts by unifying access policies and monitoring tasks. Integrations with SIEM solutions was much more frequently noted by large businesses than small businesses (84% of respondents versus 17% of respondents, respectively), but integrations with IAM platforms were uniformly recognized across industry horizontals.
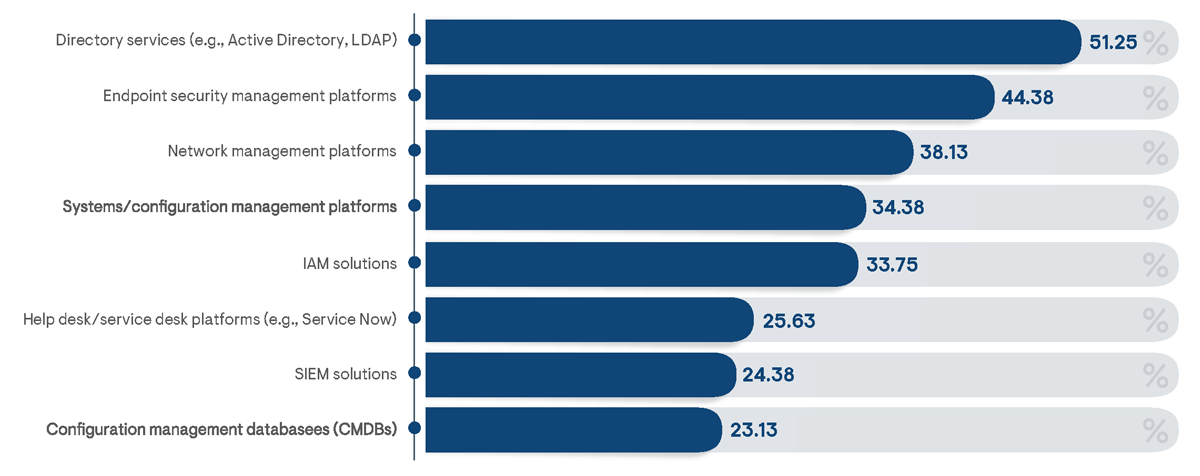
Figure 15: Percentage of survey respondents indicating direct integrations between PAM and third-party management solutions are actively in use in their organizations
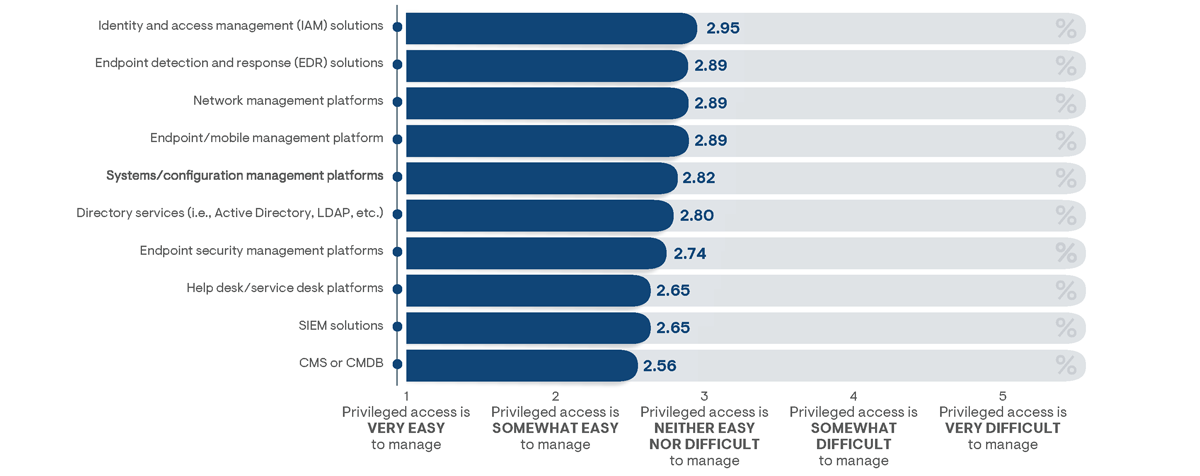
Figure 16: Average survey responses indicating the level of difficulty in managing privileged access segmented by third-party tools that directly integrate with adopted PAM solutions
Direct integrations between PAM solutions and third-party management tools were also noted to reduce overall management efforts. This was particularly recognized by survey responders that had enabled integration with service management platforms (Figure 16). On average, PAM administration efforts were 10% more likely to be recognized by survey respondents as easier to perform than by those without the integration. This improvement increases to a 13% reduction in perceived management efforts among organizations integrating with a service management platform that includes a configuration management system (CMS) or full configuration management database (CMDB). Additionally, direct
integration with a service management platform was indicated to reduce the chances of a privileged access policy violation by as much as 37%. Impacts to security improvements and management effort reductions can be attributed to the fact that direct integrations with service management platforms ensure alerts are submitted to IT administrators in real time and asset records are continuously being maintained. This result correlates directly to positive perceptions of overall PAM value. Survey respondents that had enabled direct integration with a service desk solution were 10% more likely to be “very satisfied” with their adopted PAM solution.
Back to top
Did you know?
Businesses that lacked automation capabilities for auditing privileged access were seven times
more likely to experience a privileged access policy violation than organizations with that capability
Source: EMA Research Report
Privileged Access Management Best Practices and Processes
The effectiveness of any adopted PAM solution can be evaluated by the breadth of key management processes it enables. While most PAM approaches, at minimum, provide the basic capabilities of authenticating users and defining the resources to which the identified users are granted privileged access, the granularity of access definitions and methods for secure privileged activities vary widely across popularly employed solutions. According to survey respondents, most privileged access policies are able to define which specific users are empowered with privileged access to which IT services (Figure 17). Lacking this capability, privileged access is only granted to group accounts (such as “root” or “administrator” accounts) with common authenticators shared by multiple users, substantially reducing security effectiveness. Financial sector businesses are the most likely to define individual privileged users (according to 92% of respondents from that demographic) and healthcare institutions are the least likely (as reported by only 44% of related respondents). Additionally, only 40% of organizations that utilize a free or low-cost password vault to manage privileged access were indicated to grant privileged access to individual users.
The establishment of more granular policy controls was indicated to directly result in increased security effectiveness. In particular, organizations that managed policies specifying to which business services or devices privileged access is granted were determined to be 33% less likely to have experienced a privileged access policy breach in the preceding year. Similarly, survey respondents from organizations that established policies granting privileged access to specific files were 23% less likely to report policy breaches. Ironically, both granular policy definitions were identified as the least likely to be included by respondents’ organizations in support of PAM processes.

Figure 17: Percentage of respondents indicating privileged access policies specifically defined in their organization
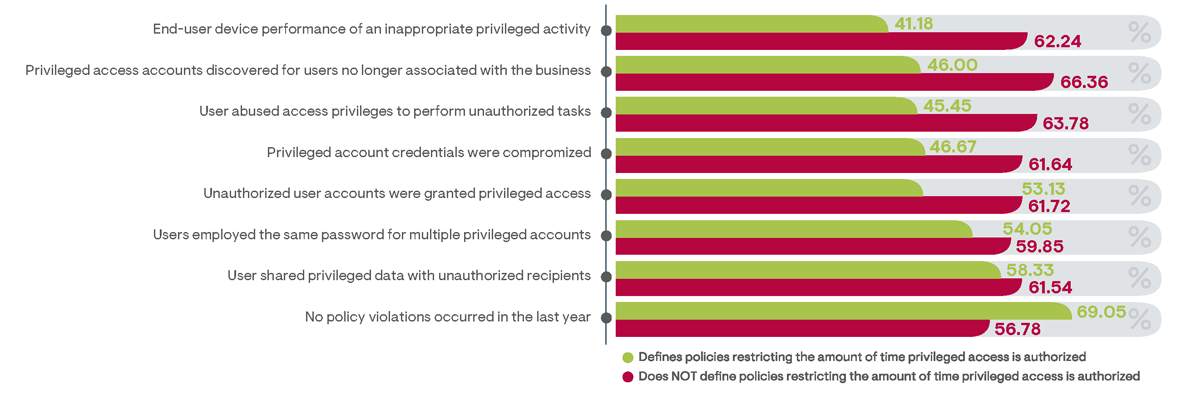
Figure 18: Comparing the percentage of survey respondents indicating policy violations that occurred in their organization in the last year between those that restrict the time privileged access is authorized with those that do not
Exceptional security improvements were also notably achieved by organizations that introduced PAM policies limiting the amount of time privileged access is authorized (Figure 18). The longer privileged access is enabled for a user account, the greater the risk it will be misused. By limiting the amount of time privileged access is required to just the duration required to complete specifically authorized tasks, bad actors are less likely to discover and exploit idle accounts. Survey results bear this out. Incidents of IT device performance impacted by inappropriate privileged activity was reported 44% less frequently by respondents from organizations that disable privileged access after a specified period. Additionally, discoveries of privileged accounts for terminated employees were reported 31% less frequently, incidents of privileged access abuse were noted 29% less frequently, and detections of credentials posted on the dark web were acknowledged 24% less frequently by responders from businesses that limit privileged access times.
PAM solutions that employ automation to enforce privileged access policies are overwhelmingly recognized as an essential component for managing elevated privileges. In fact, survey respondents with at least some PAM automation capabilities estimated, on average, they had achieved 50% of their overall PAM goals, while responders that lacked automated solutions were only 17% of the way into their PAM journey. Automated tools enable the real-time monitoring of privileged access use and the rapid remediation of detected problems and vulnerabilities.
Among organizations that employ automation as part of their PAM solution, the most frequently noted capability is the continuous identification of privileged accounts and their usage across all managed environments (Figure 19). This is differentiated from solutions that only audit access events periodically (e.g., once per day/week/month). Management solutions specifically designed to govern privileged access were the type most frequently noted (by 65% of survey respondents) for supporting continuous monitoring features. Continuous monitoring of privileged accounts and activities ensures any potential risks are addressed in real time, substantially reducing security risks. Organizations that only performed periodic monitoring of privileged access were 2.5 times more likely to have experienced a policy breach in the preceding year than those utilizing continuously monitoring feature sets. In addition, survey respondents, on average, recognized PAM solutions employing continuous monitoring to be “somewhat easy” to manage, while those utilizing periodic monitoring solutions recognized the management of PAM processes to be “somewhat difficult.”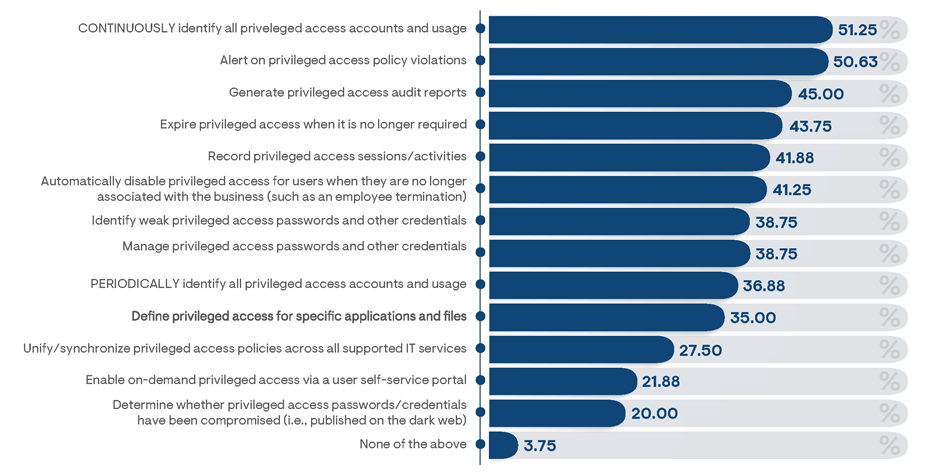
Figure 19: Percentage of survey responders indicating the PAM capabilities currently supported by automated solutions in their organization
PAM automation is essential for enabling holistic visibility into privileged access usage for governance and accountability. In fact, survey respondents that lacked automation capabilities in their adopted PAM solution consistently reported the basic process of establishing an inventory of managed systems, users, and accounts to be “very difficult” to achieve. Accelerating business requirements for reducing management efforts are driving the adoption of PAM solutions that simplify the monitoring of privileged access information. Roughly half of survey respondents indicated their organization leverages automation to detect and alert on privileged access policy violations. Timely notifications on vulnerabilities and breaches are critical to ensuring rapid responses to mitigate risks and proactively prevent privileged account misuse.
Improvements to privileged access visibility also simplifies processes for conducting periodic audits for governance and regulatory compliance attainment. Audit processes can be extremely costly and time-consuming if performed manually. Automation can substantially reduce auditing processes by collecting and generating prebuilt reports on the privileged access granted to users and how they are being used. This timely and accurate information can have a significant impact on reducing security vulnerabilities. According to survey results, organizations that employ automation to generated privileged access audit reports are indicated to have substantially reduced rates of policy breach events. For example, businesses that lacked these capabilities were indicated to be more than seven times more likely to discover that privileged account credentials had been compromised (i.e., posted on the dark web) during the preceding year.
The greatest inhibitor to enabling holistic visibility and management of privileged access is increasing IT infrastructure complexity. Only about 27% of survey respondents noted the ability to unify PAM policies across all supported IT services, including on-premises servers, cloud- hosted environments, web services, and endpoint devices. However, more organizations that had adopted solutions enabling PAM policy synchronization were able to report decreased breach rates. In particular, organizations that adopted a unified PAM approach were indicated to be 72% less likely to have discovered active privileged access accounts for users that had been terminated. This correlation can be attributed to the fact that typically, when users depart, administrators only disable known accounts and fail to recognize access privileges that were granted to less frequented resources. With a unified solution, the disablement of privileged accounts need only be executed in a single location.
87%
of survey respondents indicated that shared privileged accounts
were in use in their organization
Source: EMA Research Report
An Unhealthy Reliance on Shared Privileged Accounts
Despite the obvious risks associated with enabling privileged accounts shared by multiple users, a majority of organizations continue to rely on group accounts as a method of enabling quick and easy privileged access. In fact, 87% of survey respondents indicated that shared privileged accounts were in use in their organization (Figure 20). What makes the use of group accounts so inherently dangerous is the fact that they eliminate the possibility of accountability. Even organizations that stringently monitor and record the execution of privileged tasks are unable to conclusively identify the specific individual responsible for making an unauthorized change if they used a shared account. In addition, the more users who know a password or retain other credentials enabling access to a shared privileged access account, the greater the chances that account will be compromised.
Among survey respondents, database administrators were the type of user most frequently noted to employ shared privileged accounts. High percentages of shared administrator accounts are also very commonly in use with 73% of survey respondents indicating their usage in their organizations (including all types of shared administrator accounts). Shared accounts were indicated to be somewhat more common among small and medium-sized businesses than large enterprises and were more frequently noted by respondents from manufacturing and professional services organizations. Respondents from financial institutions reported the lowest frequencies of shared privileged accounts. 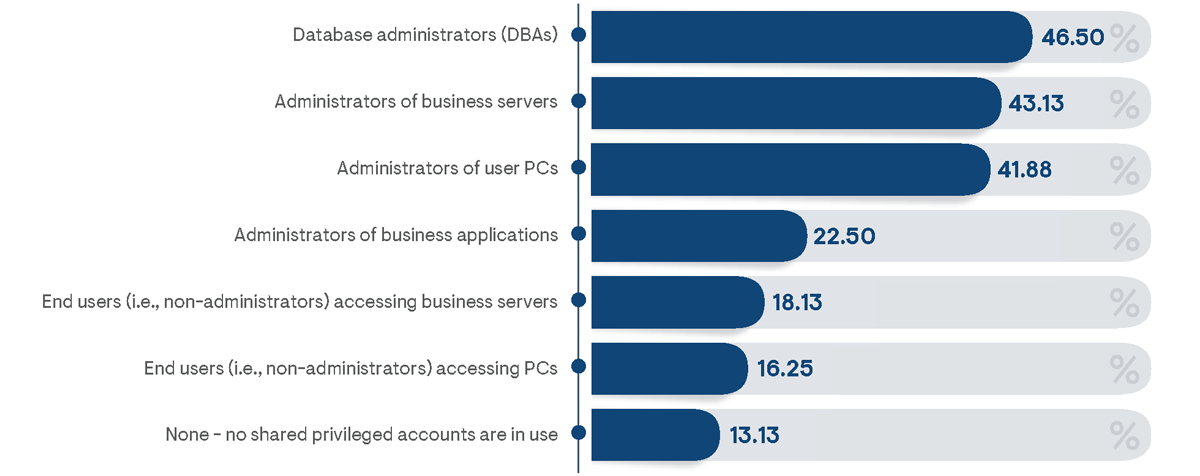
Figure 20: Percentage of respondents indicating the types of users who have access to shared privileged accounts in their organizations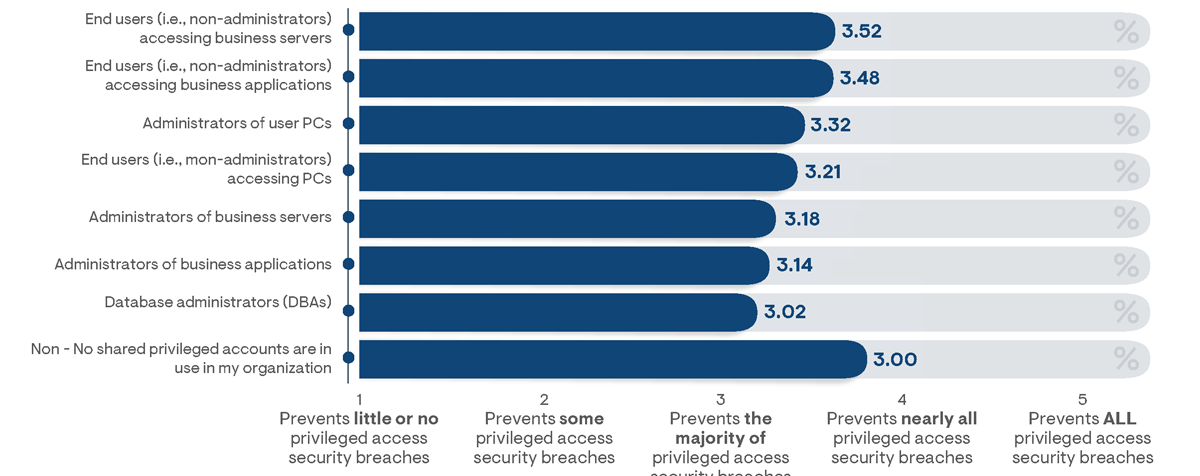
Figure 21: Average survey responses indicating the level of confidence responders have that their organization’s PAM practices will prevent security breaches, segmented by types of supported users with shared privileges
Survey results indicate that perceptions of privileged access security effectiveness are related to the level of reliance on shared privileged accounts. On average, respondents from organizations that did not employ shared privileged accounts expressed higher confidence in the ability of their adopted solution to prevent privileged access security breaches (Figure 21). It is particularly noteworthy that the level of security confidence reported for each type of supported user is roughly inversely proportional to the frequency of their usage. Higher frequency users (such as DBAs) are related to lower confidence scores, while lower frequency users (such as end users) correlate to higher confidence scores. This relationship suggests that the greater the reliance on shared privileged accounts, the less control organizations perceive they maintain over the use of privileged access.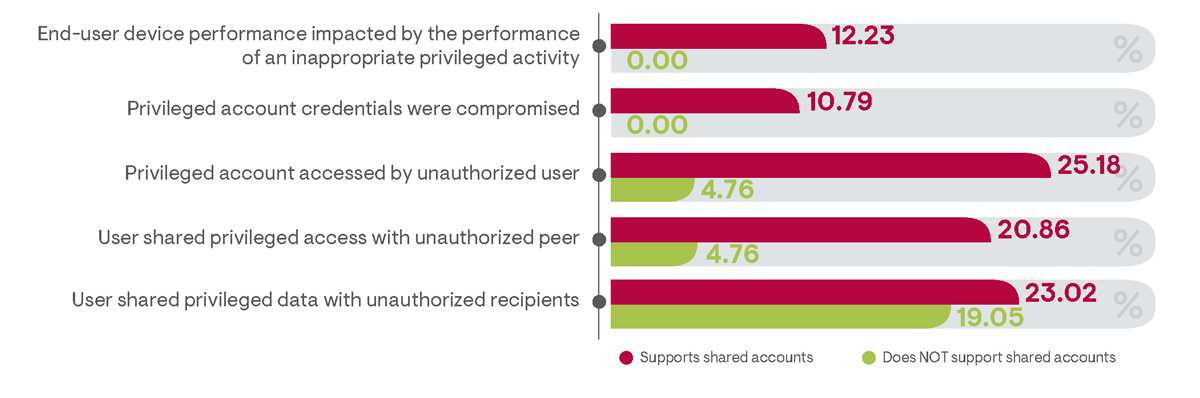
Figure 22: Comparing the average percentage of privileged access policy violations between organizations supporting shared privileged accounts and those that do not support shared privileged accounts
Correlations between the use of shared accounts with known policy violations bear out concerns of security deficiencies (Figure 22). Among survey responders whose organizations did not support shared privileged accounts, there were no reported cases of privileged account credentials reported on the dark web and no impacts to endpoint device performance due to inappropriate privileged activity. Additionally, incidents of privileged accounts accessed by an unauthorized user and users sharing privileged access with a peer were both indicated to be roughly five times more likely with organizations that support shared accounts.
Rather than relying on unfettered group accounts to enable multiple privileged users, survey results suggest that a more secure approach is to adopt solutions that adhere to the “principle of least privilege.” At any given time, authorized users only need to perform a specific set of privileged tasks. By limiting privileged access authorizations to just performing those required tasks, organizations eliminate the chance that elevated permissions will be misused to perform unapproved tasks. PAM platforms supporting “least privilege” allow organizations to centrally define specific policies governing which tasks can be performed by which specific users. This also provides a level of accountability not available in shared accounts since permissions to perform privileged tasks not already approved require a specific authorization.
Did you know?
Reported incidents of privileged access policy violations were 44% less frequent
among organizations with policies that define the length of time privileged access is authorized
Source: EMA Research Report
Risks of Standing Privileged Accounts
Despite increasing evidence and business recognition that utilizing standing privileged accounts is inherently insecure, most organizations continue to employ user accounts that indefinitely retain elevated privileges. In total, 97% of survey respondents indicated their organization maintains at least some standing privileged accounts. Standing privileged accounts are prime targets for hackers and other bad actors because they enable a single access point that completely bypasses security controls allowing unfettered activities. By far the most common standing privileged accounts are those created for specific IT administrators (Figure 23). However, standing privileged group accounts that are shared by multiple administrators were also indicated to be in use by a majority of survey responders. Large businesses were determined to be the least dependent on standing privileged accounts. In particular, finance and healthcare organizations were indicated to be most responsible in reducing the use of standing privileged accounts.
While an argument can be made that IT administrators may require standing privileged accounts in order to support management tasks, this does not account for the relatively high frequency of rarely used or completely unused standing privileged accounts. Among survey respondents, 28% reported they maintained rarely used accounts, while 69% noted the existence of never-used accounts.

Figure 23: Percentage of survey respondents indicating the types of standing privileged accounts that currently exist in their organizations
Default OS standing accounts—including “root” or “administrator” accounts that come preinstalled with typical OS environments—were as frequently noted to be unused as they were reported to be used. Organizations often fail to deactivate default accounts once alternative privileged access has been enabled, either out of concern that they require a failsafe method of privileged access or because they simply lack an understanding of the inherent dangers. Default OS standing accounts are always the first privileged accounts targeted by attackers because the account names are well known and very commonly in use. Among survey respondents that maintain default OS standing privileged accounts, 77% reported they had experienced a privileged access policy violation in the preceding year. By comparison, only about 59% of respondents that did not rely on default OS standing accounts experience a policy violation during that time period (Figure 24).
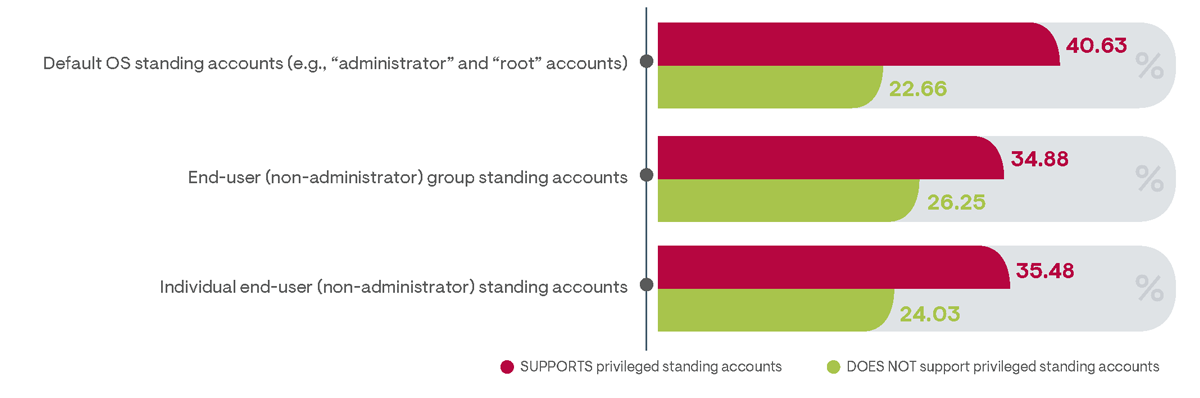
Figure 24: Comparing the percentage of survey respondents indicating they had no policy violations in the preceding year between those whose organizations support standing accounts and those whose do not
The high rate of low use or unused standing privileged accounts was also noted to exist for non-administrators. These accounts are typically created to assist a user with resolving a specific problem, but then sit idle indefinitely, increasing business security risks. Among survey respondents permitting the use of non-administrator standing privileged accounts (both individual and group accounts), the incident rate for policy violations was noted to be 30% higher than for organizations that prevent the use of such accounts.
Given these results, it is no surprise that there is a direct correlation between the existence of standing accounts and an organization’s perception of security effectiveness. When asked to indicate their level of confidence that adopted PAM solutions were able to identify all privileged access granted to business IT resources, survey respondents that did not utilize standing privileged accounts indicated, on average, a significantly higher level of certainty that they had achieved visibility across their IT support stacks (Figure 25). This is because standing accounts can exist undiscovered indefinitely, unless specifically investigated during an audit process. By contrast, non-standing privileged accounts must be authorized each time they are required for use, ensuring records are retained and users are held accountable.
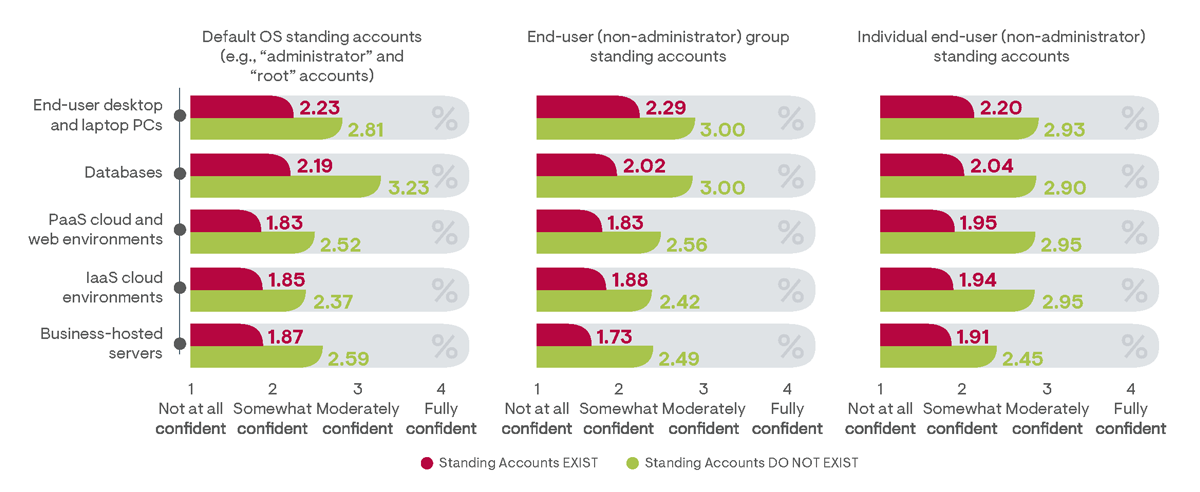
Figure 25:Comparing the average level of confidence indicated by survey responders that their organization’s adopted PAM solution has identified all privileged access on business IT resources between businesses supporting and not supporting standing privileged accounts
The most popular approach to reducing or eliminating standing privileged accounts is the employment of just-in-time (JIT) privileged access authorization technologies. JIT solutions authorize privileged access tasks to be performed by user accounts that would not otherwise be authorized to perform privileged activities, and only authorize the elevated permissions during a predetermined period of time. At the conclusion of the time period, all privileged authorizations are rescinded for the user accounts. Any future privileged access activities that need to be performed by the user’s account requires the initiation of a new authorization process. In this way, business risks are significantly reduced because any compromised accounts are unlikely to retain elevated privileges at any given time.
The key component of a JIT approach is the deactivation of privileged authorizations when they are no longer required. In total, roughly 44% of survey respondents indicated their organization has the ability to automatically expire privileged access when it is no longer required. Among these respondents, 43% indicated their organization experienced no policy violations in the preceding year. By comparison, only 13% of organizations without the ability to expire privileged access reported no policy violations. This indicates a more than threefold increase in security effectiveness by introducing this one key PAM feature.
Of course, JIT solutions require users to request privileged access each time it is required, which can become quite laborious if performed frequently using cumbersome processes, such as requiring a user to contact a help desk. These impacts to user productivity can be greatly reduced by enabling an automated user self-service portal for requesting privileged access. Among survey respondents belonging to organizations that automatically expire privileged access after use, one-third employ a user portal for requesting privileged access. These respondents reported lower frequencies of policy violations specifically related to irresponsible user activities (Figure 26). Most notably, the use of on-demand privileged access via a user self-service portal was indicated to decrease the chances of a user employing the same password for multiple privileged accounts by as much as 80%. This is because multiple privileged accounts are simply not required when using a centralized authentication mechanism. Policy-based controls governing self-service portal authorizations ensure privileged access is restricted to specific devices or applications required for the legitimate performance of privileged tasks, so each individual IT component does not require an independent standing privileged account.
Security improvements with the use of a self-service portal for authorizing JIT privileged access can also be seen with a lower frequency of policy violations that affect the performance of business IT systems. Users who are tempted to use privileged access to make impactful and unauthorized operating system changes are less likely to do so if such tasks require authorization. Additionally, related PAM solutions with policy-based controls can limit self-service portals from authorizing OS changes that can affect system performance. For instance, a user may be authorized to use granted privileged access to install an application but may not be able to change registry or kernel settings.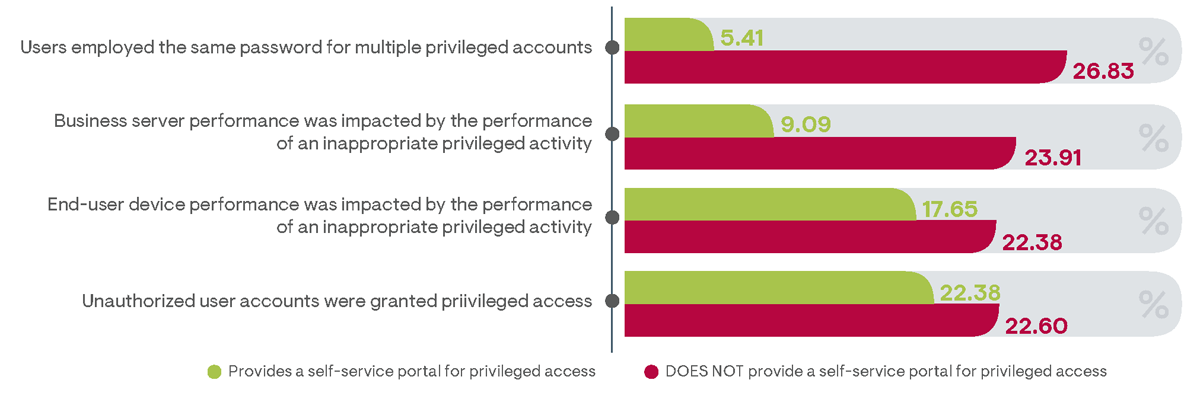
Figure 26: Comparing the percentage of survey respondents whose organizations experienced a policy violation in the preceding year between those providing a user self-service portal for granting privileged access and those that do not
88%
of survey respondents reported that their organization grants employees
local privileged administrator rights to their personal desktop or laptop
Source: EMA Research Report
Managing Privileged Access on Endpoint Devices
Despite increasing evidence and business recognition that utilizing standing privileged accounts is inherently insecure, most organizations continue to employ user accounts that indefinitely retain elevated privileges. In total, 97% of survey respondents indicated their organization maintains at least some standing privileged accounts. Standing privileged accounts are prime targets for hackers and other bad actors because they enable a single access point that completely bypasses security controls allowing unfettered activities. By far the most common standing privileged accounts are those created for specific IT administrators (Figure 23). However, standing privileged group accounts that are shared by multiple administrators were also indicated to be in use by a majority of survey responders. Large businesses were determined to be the least dependent on standing privileged accounts. In particular, finance and healthcare organizations were indicated to be most responsible in reducing the use of standing privileged accounts.
While an argument can be made that IT administrators may require standing privileged accounts in order to support management tasks, this does not account for the relatively high frequency of rarely used or completely unused standing privileged accounts. Among survey respondents, 28% reported they maintained rarely used accounts, while 69% noted the existence of never-used accounts.

Figure 23: Percentage of survey respondents indicating the types of standing privileged accounts that currently exist in their organizations
Default OS standing accounts—including “root” or “administrator” accounts that come preinstalled with typical OS environments—were as frequently noted to be unused as they were reported to be used. Organizations often fail to deactivate default accounts once alternative privileged access has been enabled, either out of concern that they require a failsafe method of privileged access or because they simply lack an understanding of the inherent dangers. Default OS standing accounts are always the first privileged accounts targeted by attackers because the account names are well known and very commonly in use. Among survey respondents that maintain default OS standing privileged accounts, 77% reported they had experienced a privileged access policy violation in the preceding year. By comparison, only about 59% of respondents that did not rely on default OS standing accounts experience a policy violation during that time period (Figure 24).

Figure 24: Comparing the percentage of survey respondents indicating they had no policy violations in the preceding year between those whose organizations support standing accounts and those whose do not
The high rate of low use or unused standing privileged accounts was also noted to exist for non-administrators. These accounts are typically created to assist a user with resolving a specific problem, but then sit idle indefinitely, increasing business security risks. Among survey respondents permitting the use of non-administrator standing privileged accounts (both individual and group accounts), the incident rate for policy violations was noted to be 30% higher than for organizations that prevent the use of such accounts.
Given these results, it is no surprise that there is a direct correlation between the existence of standing accounts and an organization’s perception of security effectiveness. When asked to indicate their level of confidence that adopted PAM solutions were able to identify all privileged access granted to business IT resources, survey respondents that did not utilize standing privileged accounts indicated, on average, a significantly higher level of certainty that they had achieved visibility across their IT support stacks (Figure 25). This is because standing accounts can exist undiscovered indefinitely, unless specifically investigated during an audit process. By contrast, non-standing privileged accounts must be authorized each time they are required for use, ensuring records are retained and users are held accountable.
While much of the focus of PAM solutions and practices tends to be on protecting cloud and on-premises server hosting environments, impacts to end-user devices (i.e., desktop or laptop PCs) should not be overlooked. Roughly 88% of survey respondents indicated that their organization provides employees with local administrator rights to their company- supplied PC or laptop. On average, endpoint privileged access is granted to roughly 24% of business employees. The percentage of users granted endpoint device administrator rights increases with company size, and fully one-quarter of large business employees are empowered with elevated privileges on their workstations (Figure 27). That is a staggeringly high number considering the potential impacts to business operations from privileged access misuse. In an organization of 10,000 employees, about 2,500 can be expected to retain privileged access to their devices. Respondents from healthcare institutions were indicated to be most likely to allow users local administrator rights, granting it to 46% of their workforce, on average.
Organizations that grant users privileged access to their endpoint devices are exposed to some elevated security risks. In particular, survey respondents from businesses that allow users to retain local administrator rights were 34% more likely to report incidents of a compromised privileged account credential. Since non-administrators are more likely to employ easily guessable password and reuse passwords across multiple accounts (including with non-business resources, such as public email or social media tools), they are at greater risk of exposing credentials and having them posted on dark websites.
In addition, incidents of end-user device performance impacted by an inappropriate privileged activity were reported twice as frequently by organizations that allow privileged device users than by those that limit this access to qualified administrators. Non-administrators often lack the expertise required to perform advanced operating system management tasks and are unaware of business rules governing system changes.
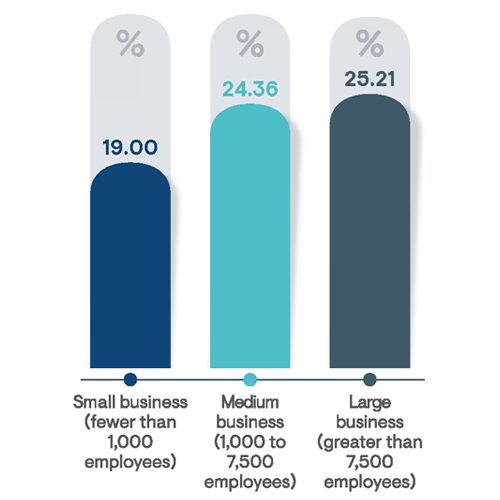
Figure 27: Average percentage of end users (i.e., non-administrators) granted privileged access to their personal endpoint devices by organization size as noted by survey respondents
However, it is not uncommon for end users to believe they have enough of an understanding to make system updates without taking the time to open a help desk ticket or otherwise involve IT administrators.
Despite the fact that many organizations grant end users privileged access in order to reduce the day-to-day management burden on IT administrators, survey results indicate this approach delivers the opposite outcome. One-third of survey respondents from organizations that allow end users privileged access to their workstations report that they find overall PAM processes to be somewhat or very difficult to manage. Only 21% of organizations that restrict non-administrator privileged access to endpoint devices noted PAM to be somewhat difficult to manage, and no respondents from this group identified PAM support to be very difficult.
In fact, survey respondents indicated that PAM administration challenges across all primary practices are very significantly diminished among organizations that do not grant employee access rights (Figure 28).
Not surprisingly, the greatest reduction to management challenges achieved by organizations that do not grant end users privileged access to their workstations was with managing endpoint device administrator accounts. This can be simply attributed to a significant reduction in the number of privileged accounts that need to be monitored and supported. Similarly, more granular PAM policy enforcement requirements—such as limiting privileged access times and the types of privileged tasks that can be performed—are indicated to be greatly simplified by a reduction in the number of privileged users. A key implication from this result suggests that organizations that necessitate the granting of local administrator rights to end users should adopt a PAM-specific platform that specifically defines and enforces policies supporting “least privilege” requirements on endpoint devices in order to reduce management efforts while boosting security effectiveness.
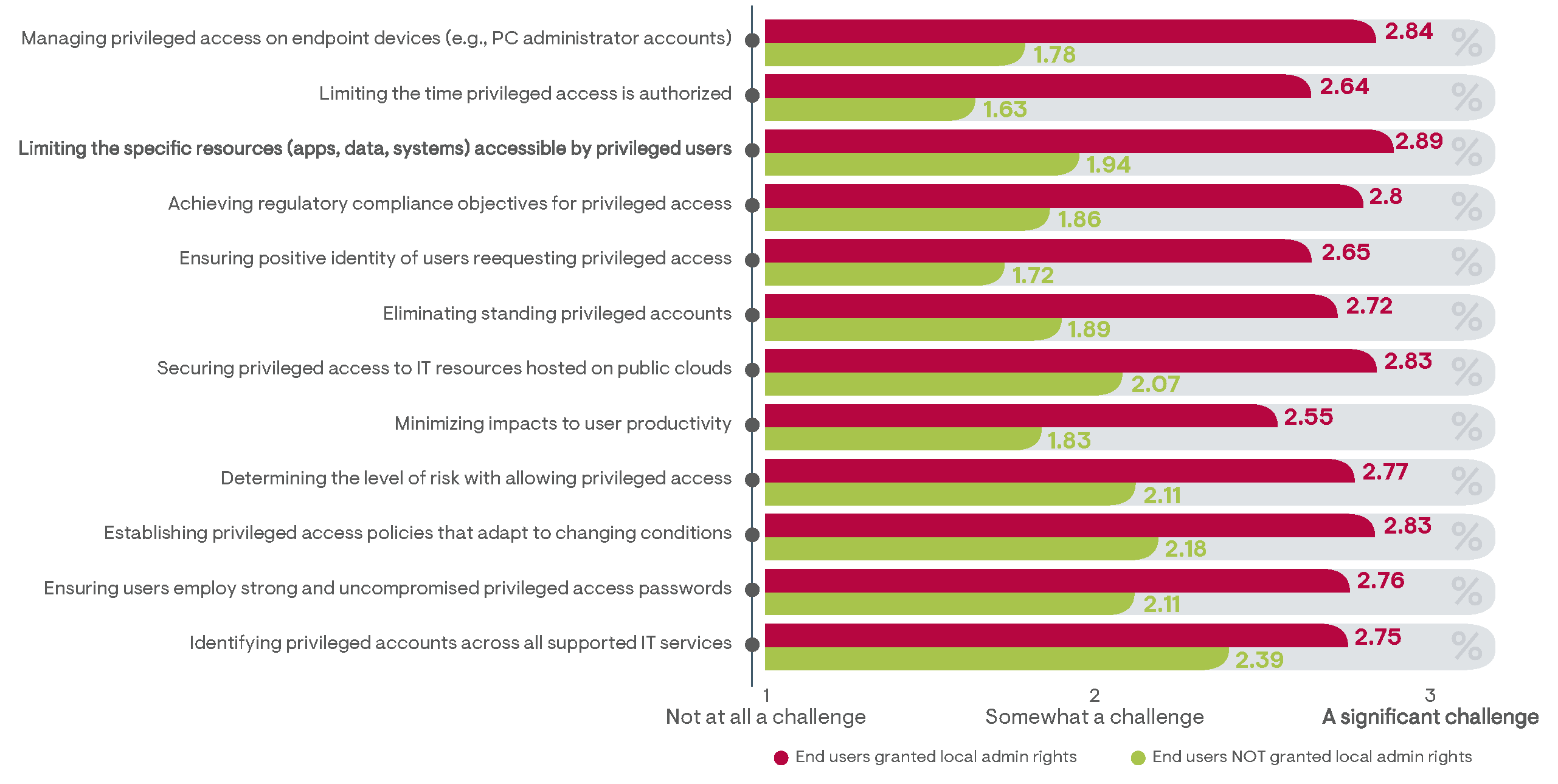
Figure 28: Comparing the average level of challenge in performing critical PAM tasks between survey responders from organizations that grant end users local admin rights to their personal workstation and those that do notFigure 28: Comparing the average level of challenge in performing critical PAM tasks between survey responders from organizations that grant end users local admin rights to their personal workstation and those that do not
Did you know?
Only about 40% of survey respondents indicated they were fully confident
that their adopted PAM solution has identified all privileged access in their organization
Source: EMA Research Report
Outcomes from Adoption of Privileged Access Management Solutions
Perceptions on the effectiveness of adopted PAM solutions are often very subjective. The three key considerations for determining a solution’s value to the business include the level of security provided, how difficult it is to manage, and the impact the approach has on privileged user experiences. Overall, survey respondents displayed high favorability with their adopted PAM solutions, with 51% stating they were somewhat satisfied and 37% indicating they were very satisfied. Only 2% of respondents indicated they were dissatisfied with their actively used PAM tools. According to survey results, PAM solutions with more advanced security-focused features achieved the highest favorability ratings (Figure 29). Most notably, respondents from organizations that utilized PAM platforms that continuously identify all privileged accounts and usage were most likely to report they were very satisfied with the adopted product. By comparison, solutions that only periodically poll or audit managed resources were indicated to be among the least favored. Continuous monitoring is essential for ensuring that vulnerabilities and breaches are detected and remediated in real time, which is the key to enabling proactive PAM and effective governance.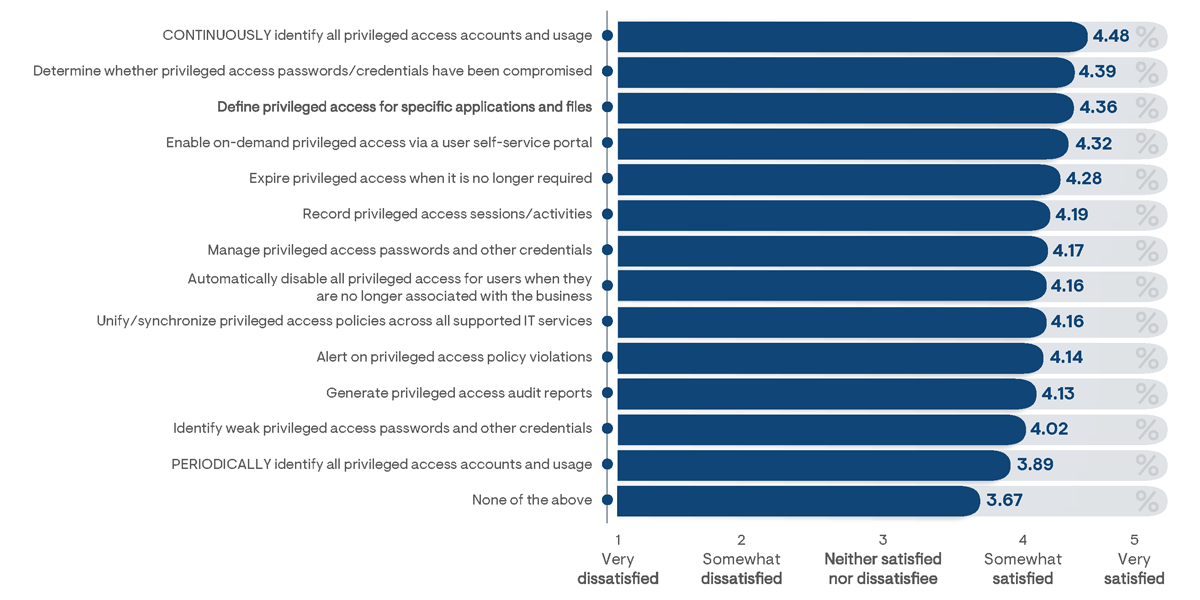
Figure 29: Average responses indicating the level of overall satisfaction with currently employed PAM processes and solutions, segmented by currently supported automation capabilities
Figure 30: Average percentage of survey respondents indicating they are “fully confident” their adopted PAM solution has identified all privileged access in their organization, segmented by type of PAM solution
While overall satisfaction in adopted PAM solutions may be relatively high, confidence in the ability of those tools to provide sufficient visibility into privileged access use is not. Only about 40% of survey respondents indicated they were fully confident their adopted PAM solution has identified all privileged access in their organization. Breaking that result out by adopted solutions for managing privileged access, it becomes clear that the organizations with the highest confidence are those utilizing network security management technologies—such as network access controllers (NACs)—or platforms specifically designed to support PAM processes (Figure 30). Feature sets for both approaches typically support the basic principles of least privileged access by leveraging policy-based controls that define which users or groups of users may perform specific privileged tasks. Solutions lacking these core capabilities, including shared spreadsheets, custom scripts, and low-cost password vaulting solutions, were reported to inspire the least level of confidence in privileged access visibility.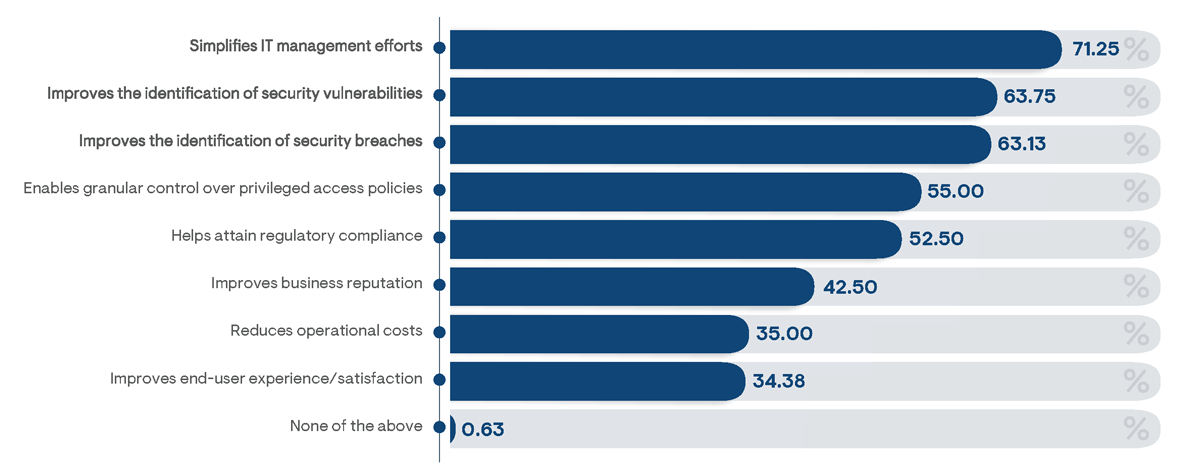
Figure 31: Percentage of survey respondents indicating key advantages they believe are achieved from the adoption of an enterprise-class PAM platform
While the security capabilities of an enterprise-class PAM platform are certainly highly valued, the most frequently noted advantage of adopting a premium PAM solution, according to survey respondents, is with its ability to simplify IT management efforts (Figure 31). This was indicated to be particularly true among large businesses, among which 76% of responders noted value in reducing management efforts. However, only 57% of respondents from small businesses noted reductions of management efforts as an advantage, instead favoring capabilities for identifying security breaches, as reported by 66% of respondents from that demographic.
Interestingly, the reduction of operational costs was not broadly recognized as a key advantage. The adoption of an optimal PAM solution can significantly reduce costs associated with auditing, administration, and breach consequences. However, the survey result suggests this benefit is simply not a priority when considering the adoption of a PAM solution. Organizations are required to meet specific regulatory and business security goals, so for many institutions, budgetary considerations may be secondary. It is also possible that the cost reduction impacts of an enterprise-class PAM platform are not fully appreciated, since much of the results are achieved from indirect cost savings attributed to the reduction of IT administrator time and effort.
93%
of survey respondents reported they do not have confidence that their adopted
PAM solution will prevent all privileged access security breaches
Source: EMA Research Report
EMA Perspective
A lack of sufficient privileged access controls is placing the vast majority of businesses at extreme risk of significant security breaches. With 87% of survey respondents indicating their organization had experienced a privileged access policy violation in just the preceding 12 months and 93% reporting that they do not even have confidence that their adopted solutions will prevent privileged access security breaches, it is clear that currently adopted PAM processes are, in the majority of cases, insufficient to provide the level of protection they were introduced to achieve. Despite the overwhelming evidence, however, many organizations seem content to continue utilizing weak PAM solutions, as evidenced by the high overall satisfaction rates.
The reluctance to establish more effective PAM approaches is undoubtedly related to concerns about the deployment complexity and manageability of more advanced PAM technologies, and many organizations are prioritizing budgets toward alternative methods of security management, such as security information and event management (SIEM) and threat detection systems. While these technologies certainly merit consideration, related solutions may all be rendered completely ineffective by an attacker who has managed to gain privileged access. The broad and continued use of standing and shared privileged accounts certainly provides prime targets for bad actors to bypass even the most stringent security controls.
EMA survey results plainly indicate there are significant advantages to the adoption of an enterprise-class PAM platform that was specifically architected to support the principles of least privilege access. Organizations that adopted solutions with policy-based controls defining which specific resources privileged users have been granted access to were determined to be 33% less likely to have experienced a policy breach. Even more effective PAM solutions are those that limit the amount of time privileged access is authorized. Related platforms supporting JIT functionality that automatically expires privileged access when it is no longer in use were recognized as reducing the chances of a policy violation by 44%, on average. Additionally, PAM platforms that are able to centrally manage privileged access across endpoint devices were shown to reduce the chances of a compromised privileged account credential by 34%, on average. Collectively, these security improvements fundamentally transform enterprise security by minimizing risks to the business’s most sensitive and vulnerable access points.
Perhaps the greatest unsung advantage to adopting an enterprise-class PAM platform is the effect it has on actually reducing the complexity of security management and related costs. In fact, 71% of survey respondents recognized “simplifying management efforts” as the principal advantage of enterprise-class PAM adoption. Automated monitoring and task execution substantially reduce the day-to-day burden on IT administrators with dynamic support for policy management, auditing processes, and credential enforcement. This is further enhanced by solutions that provide self-help user portals that allow authorized users to responsibly gain privileged access without disturbing IT administrators at all. In regard to deployment concerns, the majority of surveyed organizations (57%) indicated their primary challenge was related to difficulties with integrating the platform with third-party solutions. This issue can be significantly mitigated by adopting PAM solutions that offer direct integrations with key technologies (most notably, service management tools).
The most effective approach to any enterprise security strategy is to prioritize solutions that address the organization’s greatest vulnerabilities first, and the distribution of privileged access accounts and their use certainly qualifies as a top-of-the-list item in most cases. With the right PAM solution in place, businesses transition from reacting to systemic privileged policy breaches to proactively preventing breaches from occurring. In addition, organizations advantaged by an enterprise-class PAM solution realize reductions to management efforts and operational costs while ensuring users are limited to utilizing elevated privileges only when absolutely necessary, and only to perform authorized, business- required tasks.
Want to learn more about Zero Trust?
Read our comprehensive Zero Trust Guide
Why Your Privileged Access Management Vendor Matters
The problem: While many modern IAM and PAM options are available, few are customizable and versatile enough to meet those challenges (both micro and macro) without making compromises along the way.
You need a privileged access management vendor that will be with you throughout your journey — a relationship with an experienced team can help you select and sequence your IAM, identity governance, PAM implementations, and more. At each phase, they should work with you to ensure smooth execution and performance.
The right partner can help you make critical strategy decisions that move your access management culture beyond legacy systems and ever-forward. A vendor with extensive experience can help you avoid project pitfalls specific to your organization.
Back to top
Bravura Privilege Awards
2021 PAM Overall Leader
KuppingerCole 2021 Analysis Report on best Privileged Access Management (PAM) solutions
2021 PAM Product Leader
KuppingerCole 2021 Analysis Report on best Privileged Access Management (PAM) solutions
2021 PAM Market Leader
KuppingerCole 2021 Analysis Report on best Privileged Access Management (PAM) solutions
2021 PAM Innovation Leader
KuppingerCole 2021 Analysis Report on best Privileged Access Management (PAM) solutions
-7.27%
is the average percentage share prices fall after a breach
Source: Comparitech
Introducing Bravura Security Fabric
Bravura Security Fabric delivers a cutting-edge solution to identity protection, built-in threat detection, and singular identity, privileged access, and password platform. This all-in-one platform is ready-made for organizations — conquering access challenges out-of-the-box without expensive customization.
Truly framework agnostic, Bravura Security Fabric integrates across various cloud, platform, and security systems with versatility and adaptability. It automates the complex life cycle management of large, dynamic, and unusual user bases — without the need for ad-hoc scripting or additional resources and staff.
The only platform that manages identities with ONE powerful solution
The Bravura Security Fabric singular, powerful framework and platform brings together all the layers of Bravura.
Benefits
Bravura Security Fabric meets all of your digital identity and access security needs with industry-leading features and applications. It’s packed with future-ready technological and architectural building blocks enhanced by decades of reliability to protect, manage, and govern your entire identity and access infrastructure for the next generation. All of this scalable capability comes bundled with Bravura Security’s global support.
Implement a singular platform designed for IAM (including identity governance administration) and PAM challenges out of the box without expensive customization
Simplify your vendor and program deployment, streamline service level agreements, and lower overall cost
Address your most urgent PAM, MFA, and federated SSO needs with the ability to turn services on and off
See value faster while it evolves to protect institutional research, data, finances, and reputation from cybersecurity threats
Bonus
The solution also integrates with the latest security tools, including the Internet of Things (IoT), Operational Technology (OT), Information Technology Service Management (ITSM), and Security Information and Event Management (SIEM).
Interested in learning more about our privileged access management solutions?
Bravura Privilege secures access to elevated privileges. It eliminates shared and static passwords to privileged accounts.
Learn More

![[Image] Bravura Security is 2021 KuppingerCole Leadership Compass PAM Product Leader](https://www.bravurasecurity.com/hs-fs/hubfs/%5BImage%5D%20Hitachi%20ID%20is%202021%20KuppingerCole%20Leadership%20Compass%20PAM%20Product%20Leader.png?width=575&name=%5BImage%5D%20Hitachi%20ID%20is%202021%20KuppingerCole%20Leadership%20Compass%20PAM%20Product%20Leader.png)
![[Image] Bravura Security is PAM Market Leader 2021 in KuppingerCole Leadership Compass](https://www.bravurasecurity.com/hs-fs/hubfs/%5BImage%5D%20Hitachi%20is%20PAM%20Market%20Leader%202021%20in%20KuppingerCole%20Leadership%20Compass.png?width=575&name=%5BImage%5D%20Hitachi%20is%20PAM%20Market%20Leader%202021%20in%20KuppingerCole%20Leadership%20Compass.png)
![[Image] Bravura Security is PAM Innovation Leader 2021 KuppingerCole Leadership Compass](https://www.bravurasecurity.com/hs-fs/hubfs/%5BImage%5D%20Hitachi%20ID%20is%20PAM%20Innovation%20Leader%202021%20KuppingerCole%20Leadership%20Compass.png?width=575&name=%5BImage%5D%20Hitachi%20ID%20is%20PAM%20Innovation%20Leader%202021%20KuppingerCole%20Leadership%20Compass.png)
